Category filter
How to Set Passcode Rules for macOS Devices?
Devices used for work should have better security posture than personal devices. The macOS device password protects the corporate apps and resources on it from unauthorized access. It is possible to remotely configure an enterprise-grade password criterion for the macOS devices using Hexnode UEM. The devices will be marked as non-compliant if it fails to meet the password requirements that have been set or if no password is configured on the devices.
Configuring macOS Passcode Settings
To set up passcode restrictions,
- Login to the Hexnode UEM portal.
- Go to Policies, create a new policy or edit an already existing one.
- In the case of a new policy, add a policy name, which is mandatory before saving the policy, and an optional description.
- Navigate to macOS > Passcode > Configure to avail the different passcode restrictions available on macOS.
Passcode configurations:
| Password Settings | Description |
|---|---|
| Allow simple value | Uncheck this option to block users from setting simple values as the device passcode. Simple values include structured and repeating character sequences (For instance: abcd, 1234, etc.). By default, this option is checked. |
| Require alphanumeric value | Check this option to enforce the use of alphanumeric characters – a mix of numbers and letters as the device password. By default, this field is unchecked. If enabled, the password should contain at least 1 letter and 1 number. |
| Change password at next login |
If this option is checked, the user is prompted to change the password to meet the required criteria before logging in the next time. |
| Minimum passcode length | Set the minimum length of the device passcode. It could be any integer between 1 and 16. If the minimum passcode length is set to 7, users will be blocked from setting a password with 6 or less characters. By default, this field is left empty. That is, Hexnode will not change the device passcode length settings in the Mac. |
| Minimum complex characters | Enter the minimum number of special characters – numbers, uppercase letters and symbols (#, $, &, etc.), that the passcode should have. It can take a value between 1 and 4. If 2 is configured as the minimum number of complex characters, you cannot set a password with less than 2 special characters. By default, Hexnode does not update this setting on the device. |
| Maximum passcode age in days | Passcode age is the maximum number of days after which the passcode will expire. The passcode that was used to unlock the device will become invalid after the set period and the user can only unlock the device after changing the password. You can set a value between 0 and 730 days as the password age. By default, this is 0. That is, the OS will never force the password to expire. |
| Auto lock | Automatically locks the device if it stays idle for a specified amount of time. Available values are never (default), 1 minute, 2 minutes, 3 minutes, 4 minutes, 5 minutes, 10 minutes and 15 minutes. |
| Passcode history | It allows the device to store some recently used passcodes which cannot be reused as the new passcode. The available values are from 0 to 50. If the value is set to 0 (default), no password will be stored on the device. That is, you can reuse the current password as the new password when the current one expires. Setting a value of 5 will store five recently used passcodes on the device. The OS will block any attempt by the user to use any of the previous 5 passcodes while setting a new one. However, reusing the first password as the sixth passcode or later will render no issues. |
| Grace period for device to lock | The time limit before a device can be unlocked without a passcode. Values are none (default), immediately, 1 minute, 5 minutes, 15 minutes, 1 hour and 4 hours. If 5 minutes is set, you can unlock the device without entering the passcode within 5 minutes of inactivity. |
| Maximum failed attempts | Specify the number of failed login attempts allowed before the account gets disabled. When disabled, an admin account can be used to reset the disabled account’s password, or the password can be reset using Apple ID credentials or a FileVault recovery key. |
| Custom regular expression | A regular expression (regex) is a text string consisting of a sequence of characters that the system uses to match and validate the passcode set by the user. When configuring a passcode policy, administrators can use regex to create patterns that enforce specific rules, such as requiring certain characters or formats in the passcode. The regex string must not exceed 2048 characters in length. |
| Regular expression content description | Provide a content description for the regex value provided. |
Associating Passcode Restrictions with Devices
Associating the policy with target Apple devices:
- When the policy is not yet saved,
- Go to Policy Targets within the Policies tab.
- Click on Devices > + Add devices, select the required devices and click OK to associate the policy with the target devices.
- When the policy has already been saved,
- From the Policies tab, select the appropriate policy.
- Then click on Manage > Associate Targets > choose the target devices and click on Associate to associate the policy with the target devices.
What happens at the device end?
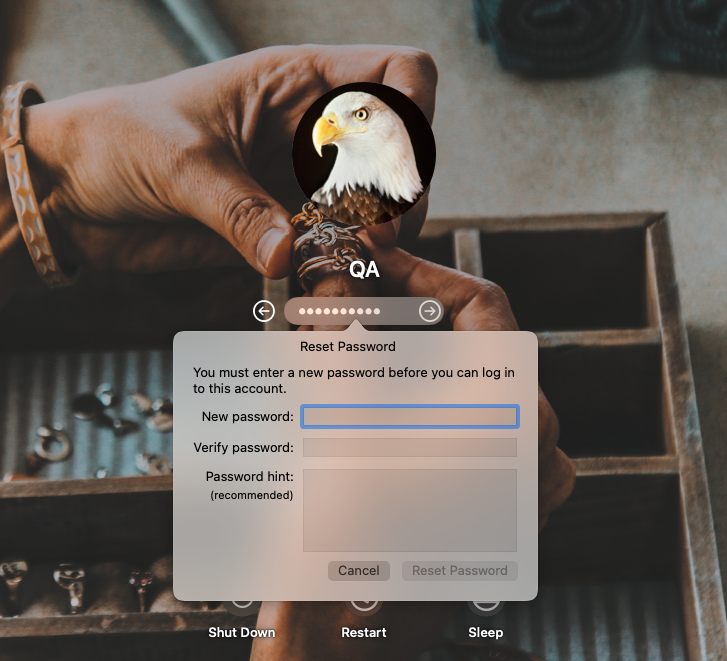
The password policy will be applied for all users on the target Mac. If the current password of a user is non-compliant with the configuration, the next time the user attempts to log in, they will be prompted to change the password.
If the user is already logged in, they won’t be able to modify any locked settings on System Preferences until the password is reset. The user will also be blocked from saving a new password till the entered password complies with your set criteria.
They will be required to change the password again when the compliance expires.