Category filter
Password policy for iOS devices
Password enables the users to protect the device from unauthorized access and hence assure device and data security. Hexnode allows the admin to configure password rules to be maintained by the end-users. These rules define the password complexity and strength, which in turn enhances the device security. When a password policy is pushed to an iOS device, the admin is bound to set up a device passcode specific to the set password rules. There can be different scenarios in setting up a password policy:
- If the device already has a passcode and it complies with the set passcode rules: In such a case, no change is required, and the device can be accessed with the same passcode.
- If the device has a passcode but it does not comply with the set passcode rules: In such a case, a pop-up would be raised asking the user to reset the passcode based on the set passcode rules. In order to set a new passcode, the user would be required to enter the old passcode and then reset the device passcode in accordance with the passcode rules pushed to the devices.
- If the device does not have a passcode: A pop-up would be raised asking the user to set a device passcode based on the passcode rules pushed to the device via policy.
Configure password policy for iOS devices via UEM
To set up passcode rules on iOS via policy,
- Log in to your Hexnode UEM portal.
- Navigate to Policies > New Policy. Assign a suitable name and description (optional) for the policy. You can also choose to continue with an existing policy.
- Go to iOS > Passcode. Click Configure.
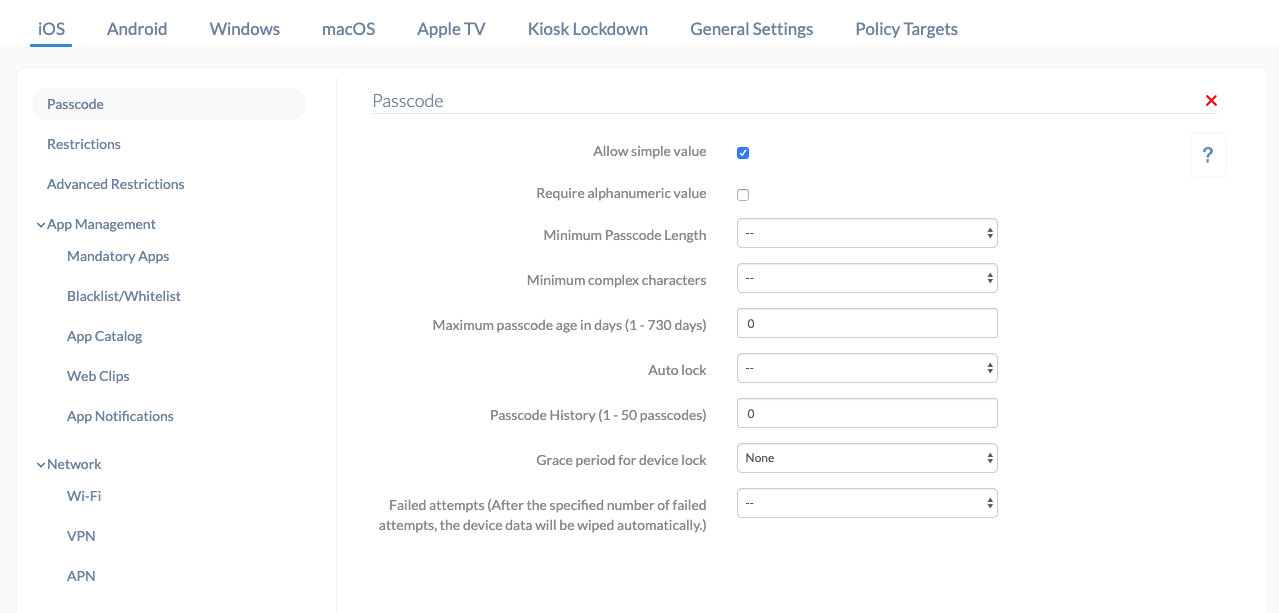
| Settings | Description |
|---|---|
| Allow simple value | The users are allowed to set a simple passcode (without uppercase letters, numbers and special characters, or just numbers) on their device, something like 123456 or abcd. |
| Require alphanumeric value | Users are required to enter alphanumeric (alphabets, numbers, optional special characters) value as their device passcode. |
| Minimum passcode length | Set the minimum number of characters that the passcode should have from the drop-down list. The value can range from 1 to 16. If 10 is set, a passcode with 8, 9 or any lower number of characters is not allowed. |
| Minimum complex characters | Set the minimum number of complex or special characters that can be included in the passcode. The limit ranges from 1 to 4. |
| Maximum passcode age in days (1 – 730 days) | Set a value from 1 to 730 (in days), after which the passcode becomes invalid and needs to be updated. Once the passcode expires, the device remains locked unless a new passcode is set and applied. |
| Auto lock | You can set a value from 1 to 15 (in minutes), after which the device will be locked automatically. |
| Passcode history | You can have the device store the last 1 to 50 passcodes so that these passcodes are not allowed to be set again for the specified number of times. Suppose you set the value as 5. A user has the passcode abcd1234. The user cannot use abcd1234 as the passcode for the next five times if he changes the current passcode. |
| Grace period for device lock | The period up to which a user can unlock the device without using passcodes. Values are None, Immediately, 1 minute, 5 minutes, 15 minutes, 1 hour and 4 hours. If the value is set to 5 minutes, then users can unlock their device within 5 minutes without using a passcode. |
| Failed attempts | Set a value from 4 to 10. If the user enters a wrong passcode for the specified number of times, the device data will be wiped automatically. |
Associating iOS Password Policy with Devices/Groups
If the policy has not been saved,
- Navigate to Policy Targets > Devices > + Add Devices.
- Choose the target devices and click OK. Click Save.
- You can also associate the policy with device groups, users, user groups, or domains from the left pane of the Policy Targets tab.
If the policy has been saved,
- Go to Policies. Choose the desired policy.
- Click on the Manage drop-down and select Associate Targets.
- Choose the target entities and click Associate.
What happens at the device end?
If the passcode is not already set on the device or the existing passcode does not comply with the policy requirements, a prompt to set a new passcode will appear for the user. There will be a time window (up to an hour) until the user can use the device without changing the passcode. Once the user crosses the time limit, the user is forced to set the new passcode to further use the device after unlocking.
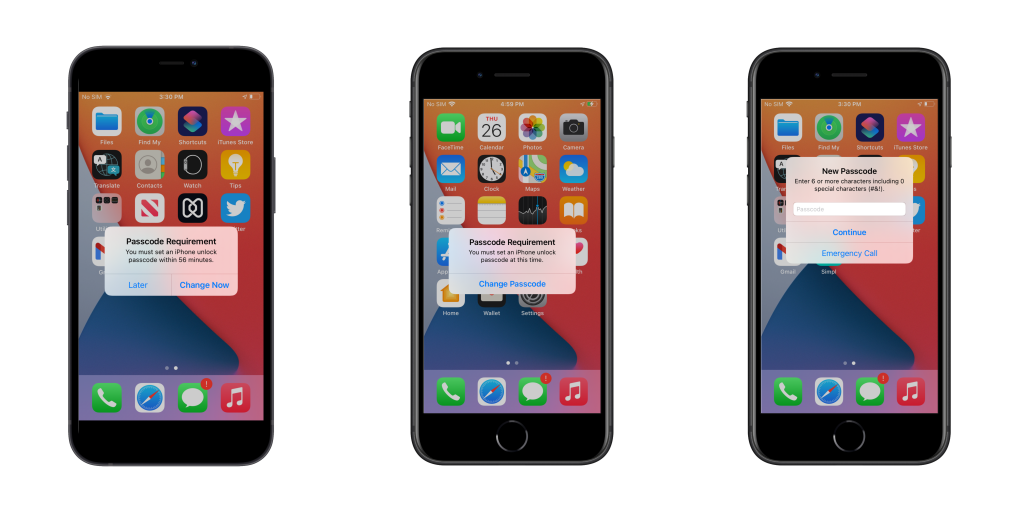
Associating the passcode policy with an iOS device also associates the policy with any Apple Watch paired with the device. Thus, the user should also configure a passcode for the Apple Watch when prompted. Below are a few cases of how the passcode restrictions affect the Apple Watch paired to iOS devices.
Case 1: When a policy requiring numeric passcode is associated:
The users must configure a passcode with the required numeric restriction on the Apple Watch.
Case 2: When a policy requiring letters or special characters in the passcode is associated:
Users must unlock their iPhones to unlock the Apple Watch. Open the Apple Watch app on the paired iPhone, and select Passcode > Unlock with iPhone under the My Watch tab.


