Category filter
How to push iOS app configuration using XML?
With Hexnode UEM, you can deploy iOS app configuration using an XML file when the app is being distributed. Admins can pre-configure in-app settings (based on logins and accounts, for instance) thus eliminating the need for users to set up apps for first-time use.
This feature is supported on all types of apps added to the Hexnode console, including VPP apps, App Store apps, and apps added via manifest URL and IPA files. The app configurations (in XML format) added to the app in the Hexnode app inventory are deployed alongside the app during its installation to ensure the configured settings are applied as soon as the app installs. App configurations cannot be applied to apps already installed on the device. The XML file cannot be deployed separately. The configurable variables depend on the provisions built in by the app developer, which may vary from vendor to vendor in the case of enterprise apps.
Deploy iOS app configurations using XML
The following steps explain how to push app configurations to devices from the Hexnode portal.
- Login to your Hexnode UEM portal.
- Navigate to Policies > New Policy.
- Provide a name (this field is mandatory) and a description of the policy.
- Go to iOS > App Management > App Configurations.
- Click +Add new configuration.
- Select the app for which you want to define configuration. Ensure the app is already present in the Hexnode app inventory.
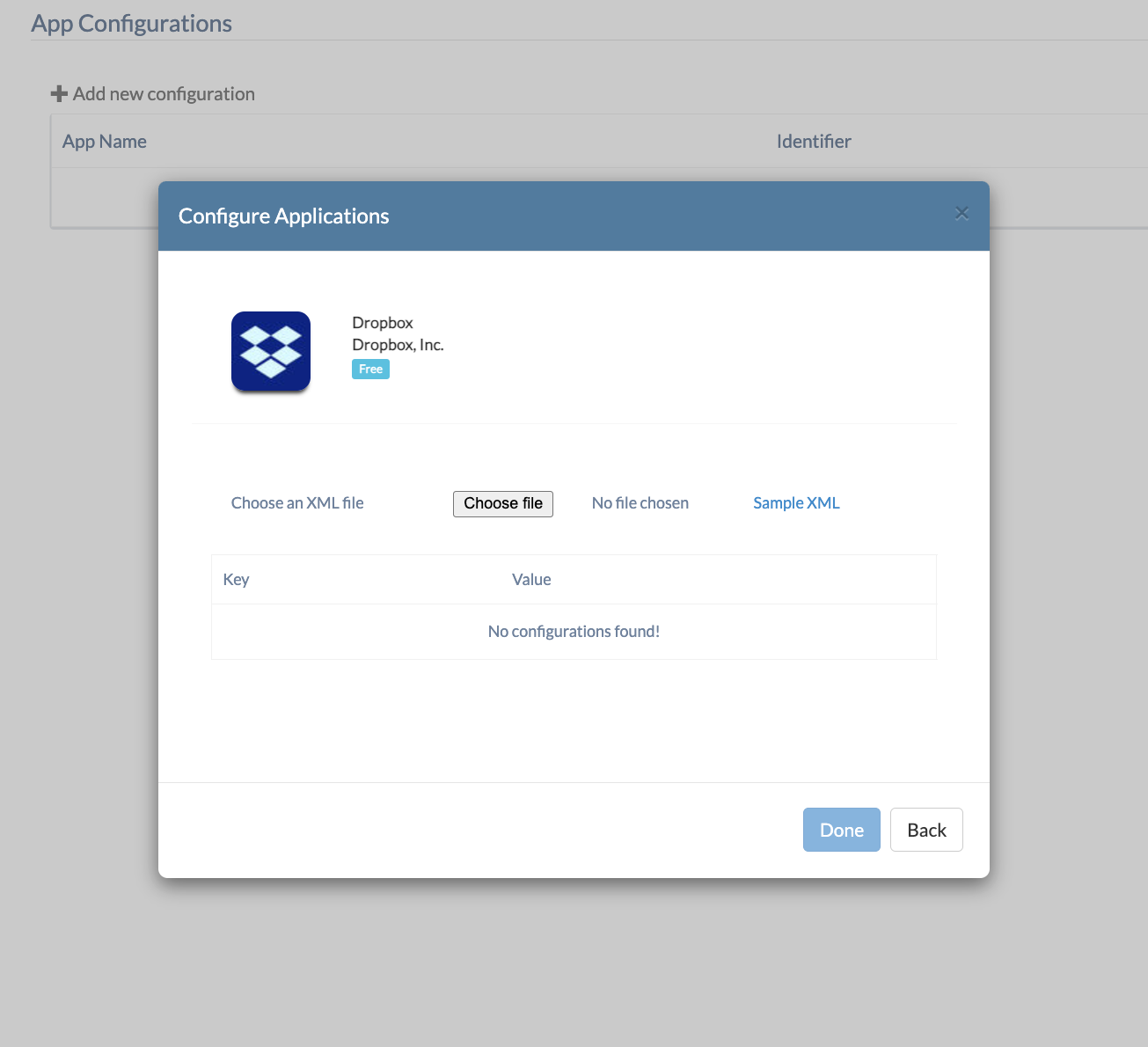
- Upload the app configuration XML file by selecting Choose file (You can download the sample XML file from the portal to view the correct format for preparing the app configuration file).
- Click Done.
- Save the app configuration by clicking Save.
- To associate the policy with target devices, go to Policy Targets.
- Select the devices or device groups you want to associate the policy to and click OK to confirm.
- Click Save to apply the policy.
A sample XML file for the Google Chrome app (that has been added to the Hexnode portal as a VPP app) will be of the format given below.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>AdsSettingForIntrusiveAdsSites</key> <integer>1</integer> <key>AllowedDomainsForApps</key> <string></string> <key>AuthNegotiateDelegateWhitelist</key> <string></string> <key>AutoFillEnabled</key> <true/> <key>AutofillAddressEnabled</key> <false/> <key>BuiltInDnsClientEnabled</key> <true/> <key>CertificateTransparencyEnforcementDisabledForUrls</key> <array> <string></string> <string></string> </array> <key>DefaultDownloadDirectory</key> <string></string> </dict> </plist> |
Once the policy is deployed to the devices, the app gets installed and is setup based on the configurations.