Category filter
How to Add Certificates for Android Devices
A certificate contains digital data that can secure and authenticate your users to access corporate resources through VPN, Wi-Fi, etc. In addition, it can secure network connections, validate email communications and authenticate users to seamlessly access data.
IT administrators can now leverage the security features in Hexnode UEM to remotely add identity certificates and certificate authorities to Android devices. Once a certificate is uploaded to a policy, it is readily available for use in every other configuration within the same policy where certificate selection is required.
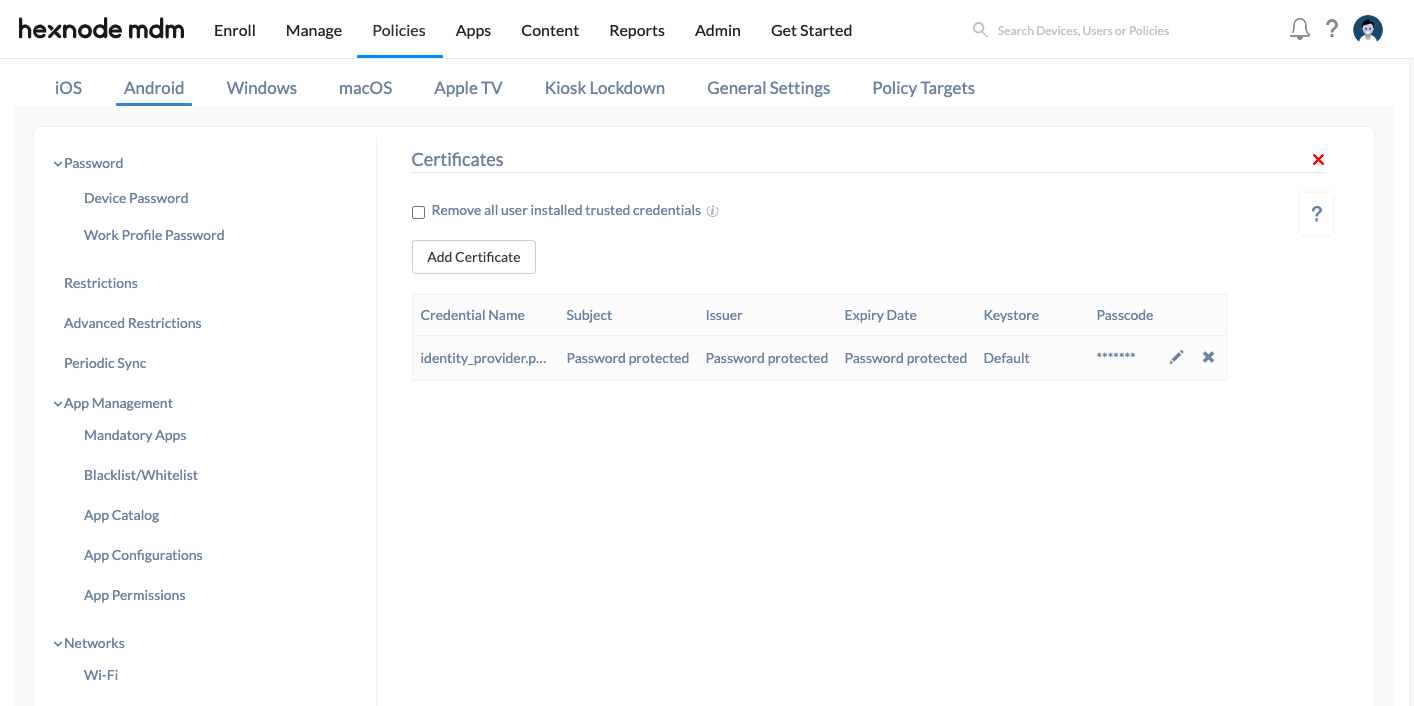
Add Certificate
- Log in to your Hexnode UEM Portal.
- Go to Policies.
- Select an existing policy or create a new one by clicking on New Policy.
- From Android > Security, select Certificates and click on Configure.
- Configure the following option, if necessary:
- Remove all user installed trusted credentials: Check this option to remove all the trusted CA certificates installed by the user and thereby avoid any malicious certificates. Enabling this option will not remove any system CA certificates and certificates installed via the policy. This option is disabled by default.
- Click on Add Certificate and upload the credential certificate.
The certificate will have the following credentials.
- Credential Name: This field becomes visible once the certificate has been uploaded. It will be already filled. However, you can change the name if required. This name is merely to identify the certificate.
- Keystore: It specifies the purpose for which the certificate is used. It can take any of the following three options:
- Default: This allows the certificate to be used for any purpose within the device.
- Wi-Fi: This allows the certificate to be used as identity certificate for Wi-Fi.
- VPN and APPS: This allows the certificate to be used as VPN credentials or for authenticating app communications.
- Credential details: It includes the certificate details such as Subject, Issuer and Expiry date.
Associate Policies with Devices / Groups
If the policy has not yet been saved:
- Navigate to Policy Targets.
- Click on +Add Devices.
- Select the devices and click OK.
- Click on Save to apply the policies to devices.
Apart from devices, you can also associate the policies with device groups, users, user groups, and domains from Policy Targets.
If the policy has been saved, you can associate it with another method.
- From Policies, check the policies to be associated.
- Click on Manage → Associate Targets and select the device.
- Click on Associate to apply policy to the devices.
After importing the certificate to the policy, you may use the edit action to modify the Credential Name, Keystore and Passcode values. It will be reflected across the target devices once the policy is saved.