Category filter
Deploy Google Santa on macOS devices using Hexnode UEM
Google Santa is a service designed for macOS devices, offering application blocklisting and allowlisting capabilities. With application allowlisting, you can designate trusted applications for execution, whereas blocklisting prevents unauthorized applications from running.
The Google Santa package includes a system extension that monitors application execution. If users attempt to access a blocklisted application, they will receive a message prompt that the application cannot be run.
With Hexnode UEM, admins can easily deploy and install Google Santa on multiple macOS devices. This document will provide you a detailed explanation of how to manage applications via Google Santa using Hexnode UEM.
Add Google Santa to the app inventory
To add the Google Santa DMG file to the app inventory, follow the steps given below:
- Download the Google Santa DMG file on your device.
- Login to the Hexnode UEM console.
- Navigate to the Apps tab and click on +Add Apps > Enterprise App.
- Select macOS, enter the required app details and upload the DMG file.
- Click on Add.
The Google Santa DMG file has now been added to the app repository.
Configure a policy to deploy Google Santa
To deploy Google Santa on your macOS devices, you need to configure Required Apps, System Extensions, and Privacy Preferences policies. The following sections provide a detailed explanation of how to set up these required configurations.
Add the Google Santa DMG file as a required app
To configure a Required Apps policy,
- Login to the Hexnode UEM console.
- Navigate to Policies > New Policy > New Blank Policy.
- Select macOS > App Management > Required App.
- Click on +Add > Add App. Next, search and select the Google Santa DMG file and click on Done.
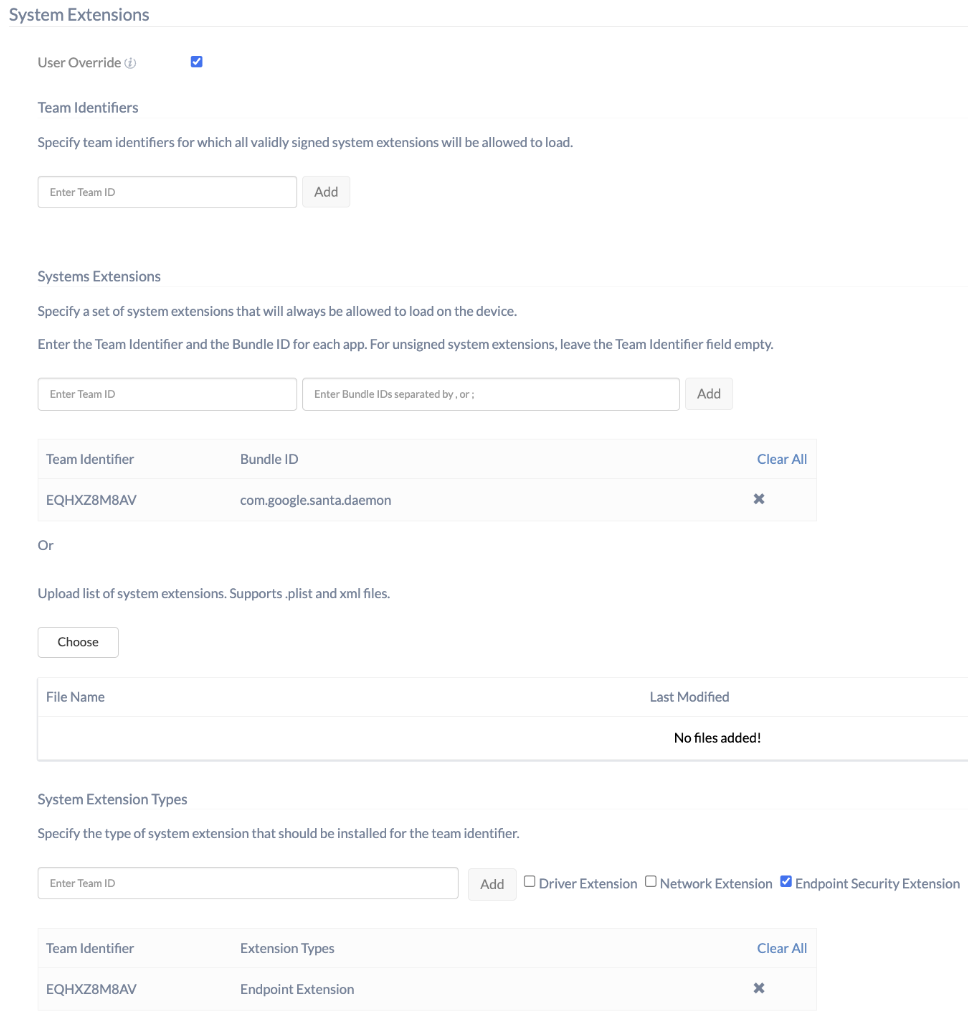
Configure System Extensions (For devices running macOS 10.15 and above)
To configure a System Extensions policy,
- Navigate to macOS > Configurations > System Extensions.
- Click Configure.
- Enable User Override.
- Under System Extensions, enter the Team ID “EQHXZ8M8AV” and Bundle ID “com.google.santa.daemon”. Click on Add.
- Under System Extension Types, enter the Team ID “EQHXZ8M8AV” and check the Endpoint Security Extension box. Click on Add.
Configure Privacy Preferences to allow full disk access
You can either use an existing policy or create a new one to grant full disk access for the necessary components of Google Santa.
- Under the macOS tab, navigate to Security > Privacy Preferences.
- Click on +Add new preference.
- Click on the dropdown beside All Files and select Allow.
- Select Specify Bundle IDs/Path.
To ensure proper functionality of Google Santa, the following components require Full Disk Access:
| Sl No | Identifier Type | Identifier | Code Requirement |
|---|---|---|---|
| 1. | Bundle ID | com.google.santa | identifier "com.google.santa" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = EQHXZ8M8AV |
| 2. | Bundle ID | com.google.santa.daemon | identifier "com.google.santa.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = EQHXZ8M8AV |
| 3. | Bundle ID | com.google.santa.bundleservice | identifier "com.google.santa.bundleservice" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = EQHXZ8M8AV |
Associate target device(s)
- Navigate to Policy Targets and select the Devices, Device Groups, Users, User Groups, or Domains you want to associate the policy with.
- Click on Save.
Shell scripts to manage applications
After successfully associating the policy, you can blocklist/allowlist applications on macOS devices using Google Santa. Deploy the below scripts meant to perform various related operations using the Execute Custom Script action.
Scripting Language – Bash
File extension - .sh
Check Google Santa status
By default, Santa operates in MONITOR mode, allowing all applications to run unless they are specifically blocklisted or lack a valid certificate. To check Google Santa status on your devices, use the following command:
|
1 2 3 4 |
#!/bin/bash CurrentUser=$(ls -l /dev/console | awk '/ / { print $3 }') CurrentUserUID=$(id -u "$CurrentUser") launchctl asuser $CurrentUserUID sudo -iu "$CurrentUser" santactl status |
Fetch file information using Google Santa
You can retrieve all relevant file information using the "fileinfo" command, which can be used to make decisions on blocking or allowing specific files.
|
1 |
/usr/local/bin/santactl fileinfo path/to/file |
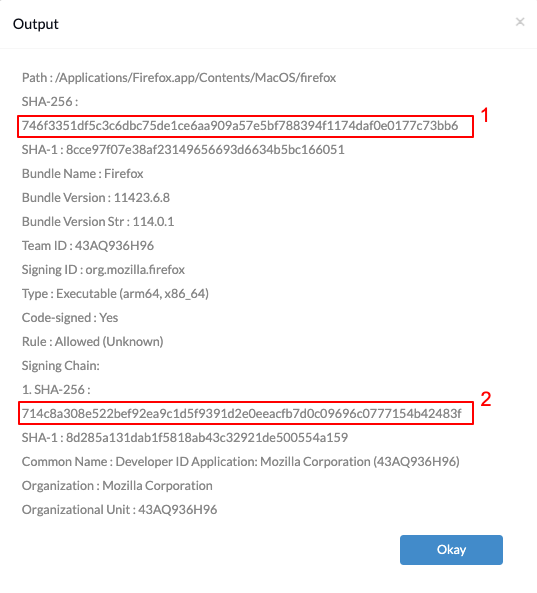
For example, to retrieve information about the Firefox application, execute the below command:
/usr/local/bin/santactl fileinfo /Applications/Firefox.app
Label 1 in the image below represents the bundle hash of the application, and label 2 represents the certificate hash of the application.
Apply rules on applications
Using the generated file hashes, you can create rules and effectively block applications on your devices.
The "rule" command offers various flags:
- allow: Add to allow
- block: Add to block
- silent-block: Block the app without displaying a pop-up
- remove: Removes existing rule
- check: Checks for the presence of a rule
Optionally,
- The --certificate flag is used to indicate whether the given hash is a certificate. This flag applies to all items signed with the same certificate, allowing you to block multiple applications from the same developer.
- The --message flag is used to specify the message displayed to the user when an application is blocked.
Block application using its bundle hash:
Bundle Hashes are specific to each version of the .app file. This implies that if an application is blocked based on its Bundle Hash, only that version of the .app file will be blocked. If a newer version of the file or software is available, it will not be blocked unless a new rule is added.
To block the Firefox application using its bundle hash and provide the user with a custom message, use the below script:
|
1 |
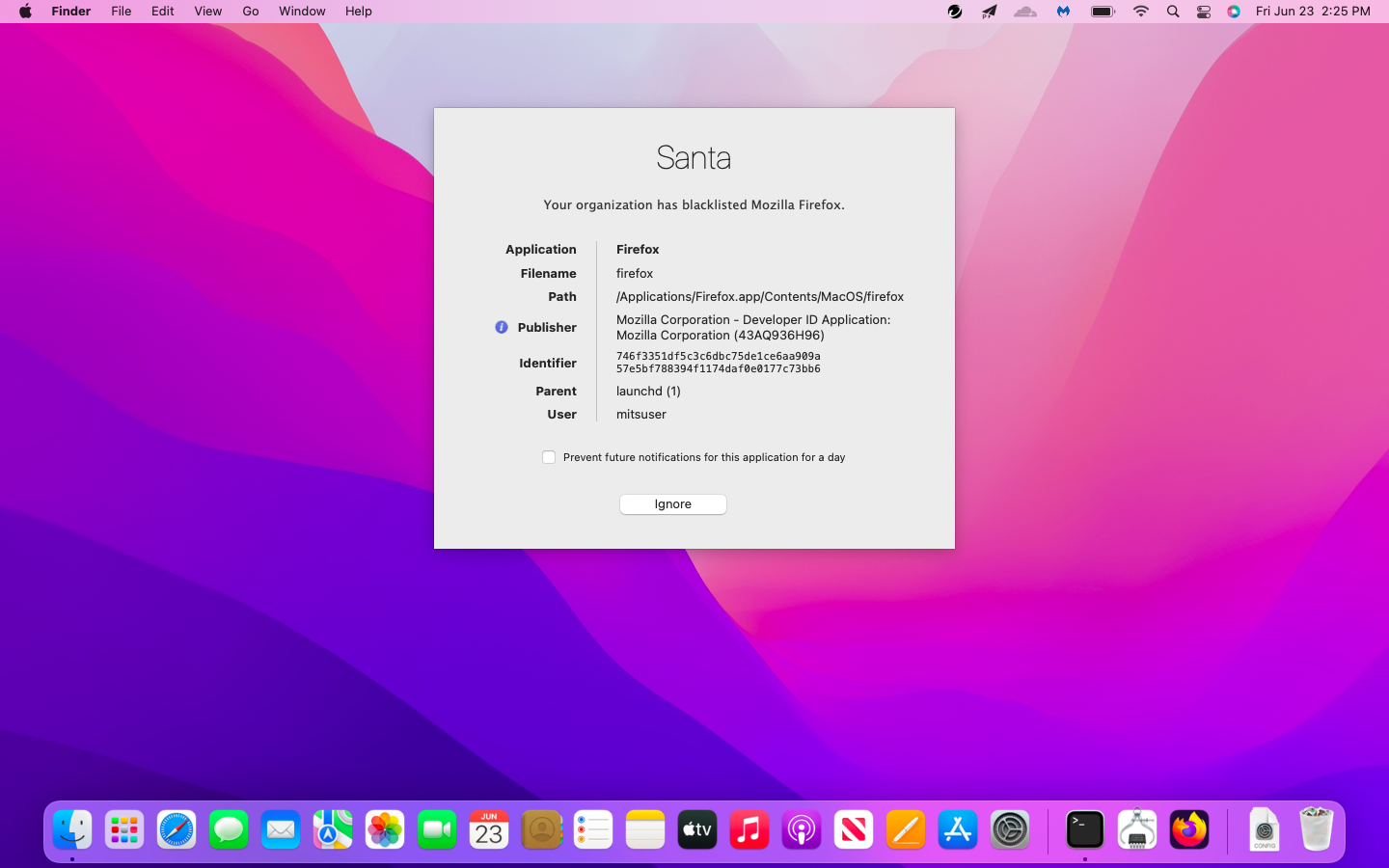
/usr/local/bin/santactl rule --block --sha256 746f3351df5c3c6dbc75de1ce6aa909a57e5bf788394f1174daf0e0177c73bb6 --message "Your organization has blacklisted Mozilla Firefox." |
When the user attempts to access the blocked application, they will receive a message prompt.
To block the application without any message prompt for the user, replace the –block flag with –silent-block in the above script.
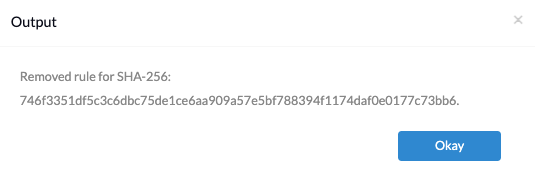
To remove the block on the application, you can use the same command, but with the --remove flag instead of --block:
|
1 |
/usr/local/bin/santactl rule --remove --sha256 746f3351df5c3c6dbc75de1ce6aa909a57e5bf788394f1174daf0e0177c73bb6 |
Block application using its certificate hash:
Certificates serve as a signature from the software developer. When you block a certificate, it will block all versions of the software associated with that certificate. It will also block any other applications signed with the same certificate. However, it's important to note that this can have unintended consequences if the device uses other items signed by the same certificate. For instance, blocking a certificate for native macOS applications will also block all Apple software on the device.
To block all versions of the Firefox application, use its certificate hash in the below script:
|
1 |
/usr/local/bin/santactl rule --block --sha256 714c8a308e522bef92ea9c1d5f9391d2e0eeacfb7d0c09696c0777154b42483f --certificate --message "Your organization has blacklisted Mozilla Firefox." |
To remove the block implemented using certificate hash of the application, you can use the same command, but with the --remove flag instead of --block:
|
1 |
/usr/local/bin/santactl rule --remove --sha256 714c8a308e522bef92ea9c1d5f9391d2e0eeacfb7d0c09696c0777154b42483f --certificate |