Category filter
Configure settings for Extensible Single Sign-on for macOS devices
This document helps you configure Extensible Single Sign-on macOS devices. Extensible Single Sign-On (SSO) is a feature introduced by Apple to enhance the login experience for users accessing enterprise apps or websites. When the extensible settings are configured on macOS devices, the device user logs in with the apps and websites once and then gains automatic access to the corresponding apps and websites, without requiring multiple logins.
Configure Extensible SSO settings
- Login to your Hexnode portal.
- Navigate to Policies.
- Select an existing policy or create a new one by clicking on New Policy.
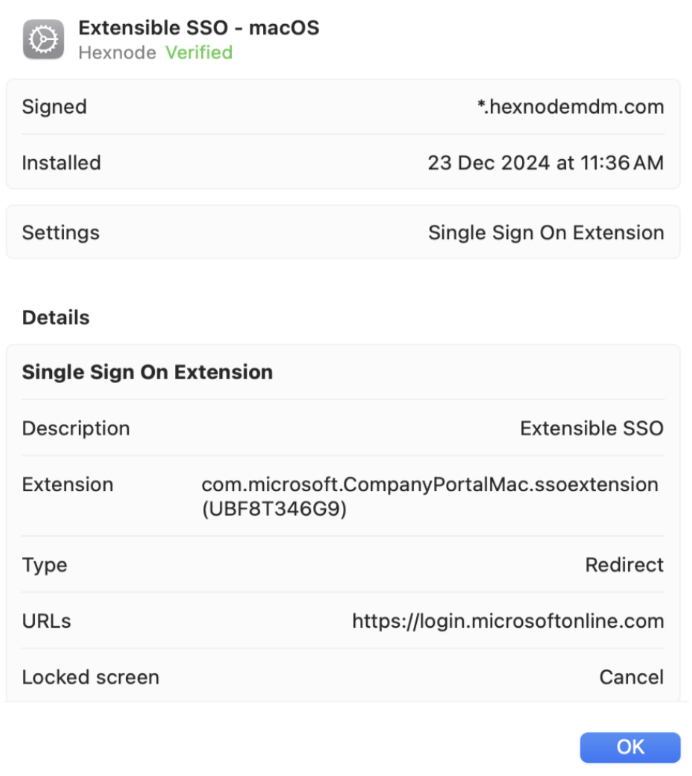
- Go to macOS > Security > Extensible SSO and click on Configure.
There are three types of SSO extension types, which include:
- Credential: Uses stored credentials to authenticate users without requiring re-entry of login details.
- Redirect: Facilitates authentication via modern protocols like OAuth, SAML 2.0, or OpenID Connect by redirecting users to an external identity provider (IdP) like Microsoft Active Directory, for authentication.
- Kerberos: The Kerberos extension on Apple devices enables secure authentication by using encrypted tickets from a central server (Key Distribution Center). This enables the device users to effortlessly authenticate resources such as websites and applications.
Redirect settings
| Settings | Description |
|---|---|
| Extension identifier | Provide the unique bundle identifier of the app extension that performs Single Sign On. |
| Team identifier | Provide the team identifier of the app extension. |
| SSO blocklist | Enter the bundle identifier for apps that don’t use SSO provided by the extension. Multiple values can be added to this field. |
| Lock screen behavior | Lock screen behavior consists of two options:
Select one from the dropdown menu. |
Credential settings
| Settings | Description |
|---|---|
| Realm | Provide the DNS domain name. It should be capitalized. |
| Hosts | Provide the domain name that can be authenticated via the app extension. Multiple values can be added to this field. |
Kerberos settings
The password settings for the apps and websites that perform SSO can be configured with the following options:
| Settings | Description |
|---|---|
| Allow saving password in Keychain Access | When enabled, the user’s password will be saved in the Keychain app. Disabled by default. |
| Require complex password value | When enabled, the system requires a complex password as suggested by Active Directory. Disabled by default. |
| Allow password change | When enabled, the user can change the password. Disabled by default. |
| Minimum password length | Admins can set the minimum password length. The default value is 8. |
| Minimum password age | Admins can set the minimum age for passwords. The default value is 42 days. |
| Password expiry alert | Admins can specify the number of days before password expiration when the system sends a notification to the user. The default value is 14 days. |
| Password history | Admins can set the number of past passwords that cannot be reused on the domain. The default value is 10. |
Custom Configuration
Admins can upload a .PLIST file containing key-value pairs for custom configuration of the SSO extension.
Associate Policies with Devices / Groups.
If the policy has not yet been saved.
- Navigate to Policy Targets.
- Click on +Add Devices.
- Select the devices and click OK.
- Click on Save to apply the policies to devices.
Apart from devices, you can also associate the policies with device groups, user and user groups from ‘Policy Targets’.
If the policy has been saved, you can associate it by another method.
- From ‘Policies’, check the policies to be associated.
- Click on Manage → Associate Targets and select the device.
- Click on Associate to apply policy to the devices.
Here, once the policies have been applied, the managed domain will be configured on your device.
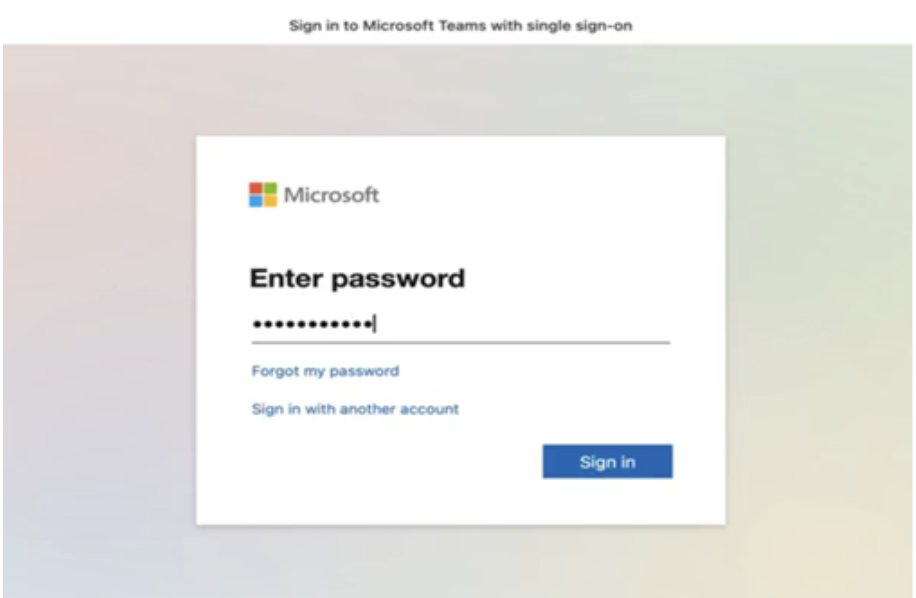
What happens on the device end?
Once the policy is configured, for example, if the Microsoft Teams app is set up with extensible SSO settings, the user will not be prompted to enter their credentials again after the initial single sign-on, as shown below.