Category filter
Configuration profile to disallow account modification on macOS devices
Allowing the addition of Internet Accounts and Apple IDs not associated with the organization can pose risks and challenges to managed devices. By restricting account modifications, administrators can maintain control over the devices’ account settings, ensuring compliance with the organization’s policies.
Disallowing account modifications on macOS devices can be effectively achieved by using a custom configuration profile. This configuration profile, which can be deployed using Hexnode’s Deploy Custom Configuration feature, helps enforce security measures across all devices.
Disallow account modification on macOS devices
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadDisplayName</key> <string>Restrictions</string> <key>PayloadIdentifier</key> <string>com.apple.applicationaccess.8C0F15FE-A045-4AE8-916A-4E03BF256140</string> <key>PayloadType</key> <string>com.apple.applicationaccess</string> <key>PayloadUUID</key> <string>AF20748F-BF79-44DE-9DF1-7A7F03278378</string> <key>PayloadVersion</key> <integer>1</integer> <key>allowAccountModification</key> <false/> </dict> </array> <key>PayloadDisplayName</key> <string>Disable Internet Accounts & Apple ID</string> <key>PayloadDescription</key> <string>This configuration profile disables modification of Internet Accounts and Apple ID</string> <key>PayloadIdentifier</key> <string>com.Hexnode.blockID</string> <key>PayloadOrganization</key> <string>Hexnode UEM</string> <key>PayloadScope</key> <string>System</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>8428E11A-E902-45CE-ADC8-D0E4EAE04370</string> <key>PayloadVersion</key> <integer>1</integer> <key>TargetDeviceType</key> <integer>5</integer> </dict> </plist> |
Here, allowAccountModification is the key that controls whether users can modify the Internet Accounts and Apple ID on a device. When allowAccountModification is set to false, it means that the ability to change, add, or remove Internet Accounts and Apple IDs is disabled on the device. If an account already exists, users can’t modify it.
What happens at the device end?
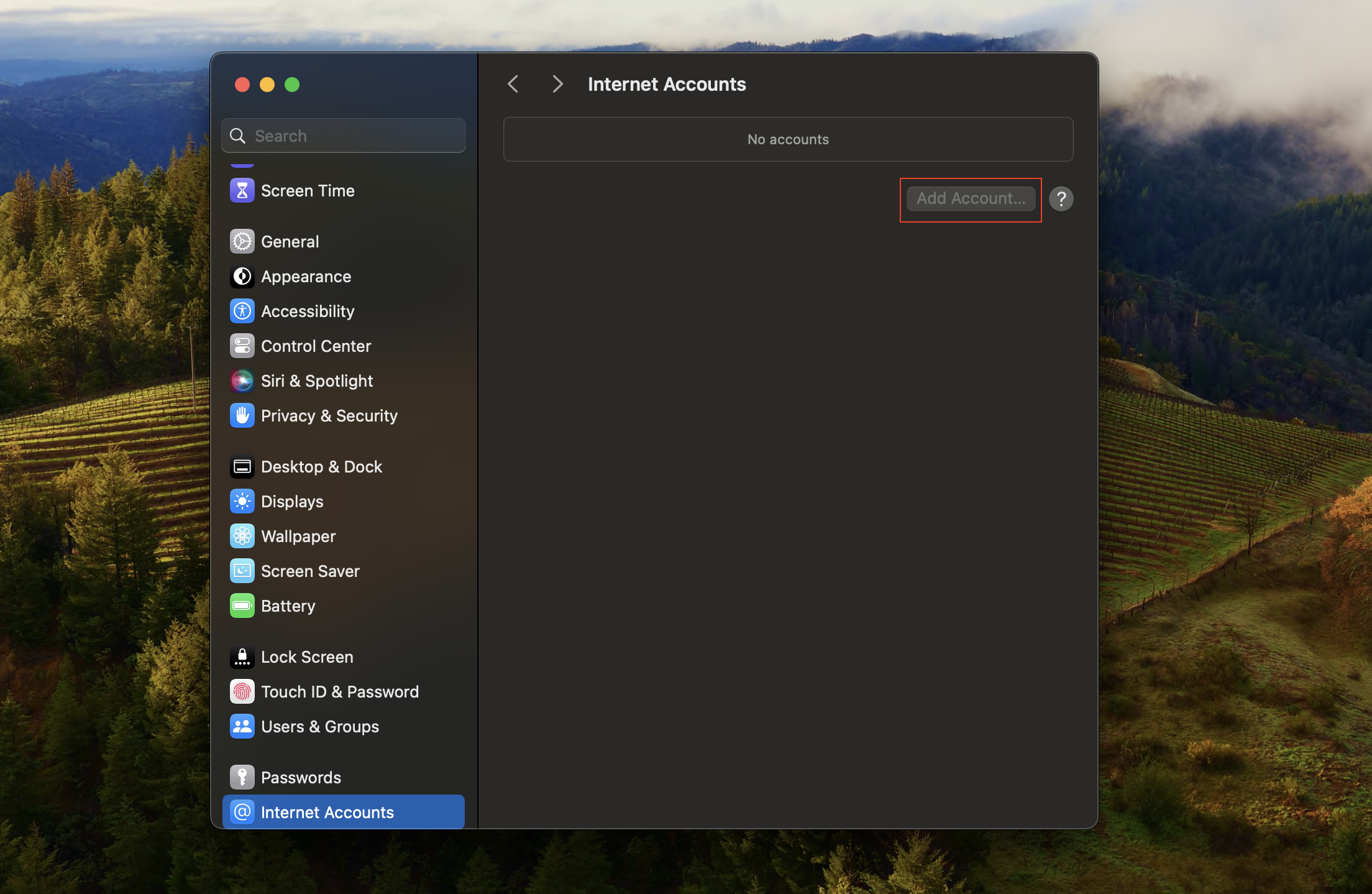
After deploying the configuration profile to the macOS device, the ability to add Internet Accounts on the device will be disabled. You can check this by accessing the Internet Accounts section in the System Settings of the Mac.
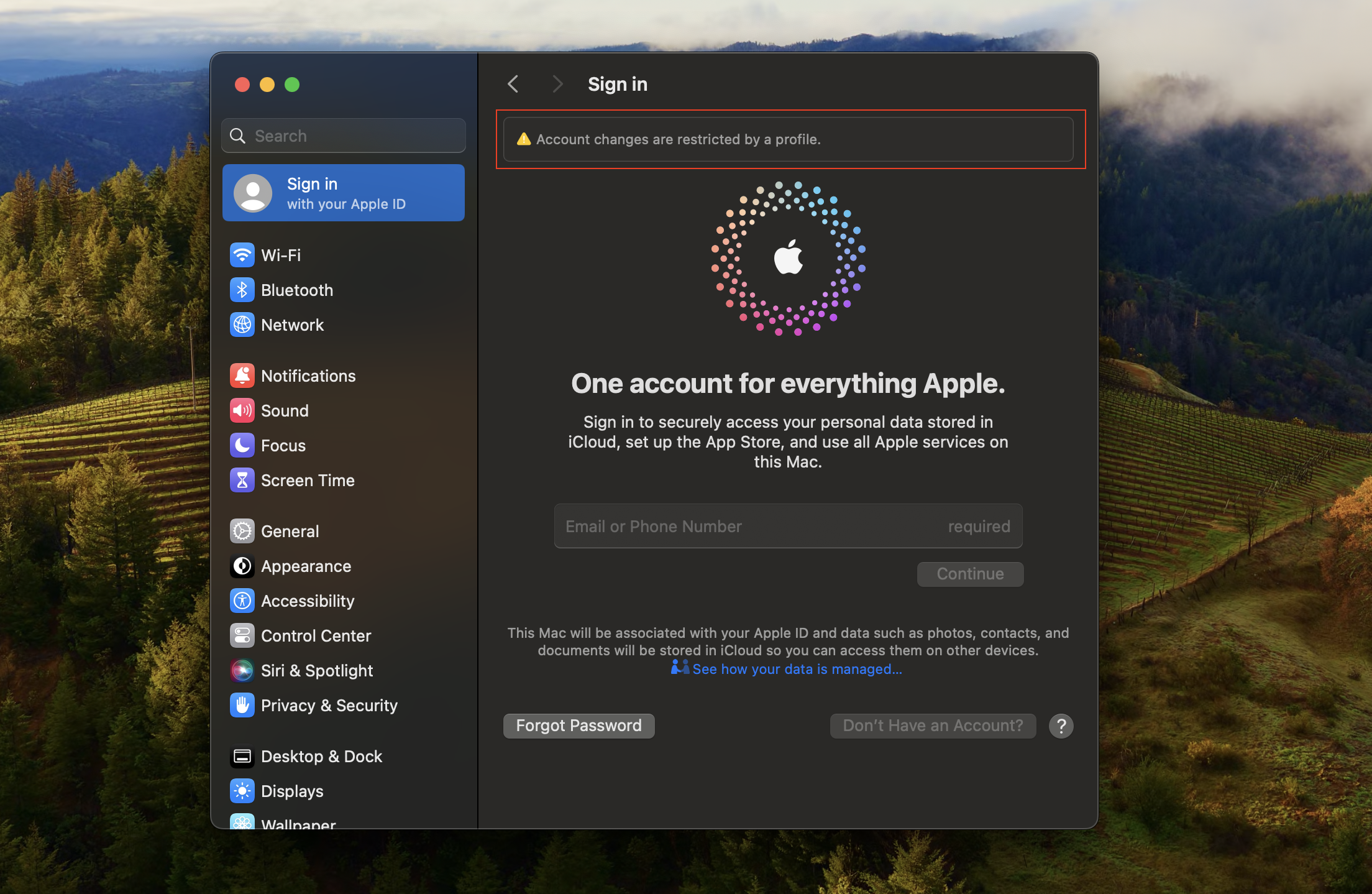
Likewise, the option to add an Apple ID will also be disabled. This can be confirmed by clicking on the Sign in with your Apple ID option within the System Settings.