Category filter
Ensure device compliance for Conditional Access
This document guides IT administrators on maintaining device compliance and explains how Conditional Access utilizes the compliance status retrieved from Hexnode UEM for iOS/iPadOS, macOS, and Android devices.
Once deployed, devices must follow a set of rules to comply with company policies. On Hexnode UEM, devices that fail to meet such requirements are marked as non-compliant. Compliance status helps administrators identify and address such devices effectively.
Conditional Access is an organization-wide policy that implements granular rules to restrict the usage of organizational resources to specific devices, locations, or browsers, etc., to ensure that resource access is granted only to authenticated entities. Administrators can set up Hexnode UEM as their third-party device compliance partner which adds the compliance state data to Microsoft Entra ID.
After Conditional Access integration, when a device enrolled in Hexnode registers with Microsoft Entra ID, its compliance information is reported to Microsoft Entra ID. If the Conditional Access policy requires the device to be marked as compliant before granting resource access, the device’s compliance status fetched from Hexnode will be used to determine whether to grant or block access.
Device compliance status in Hexnode
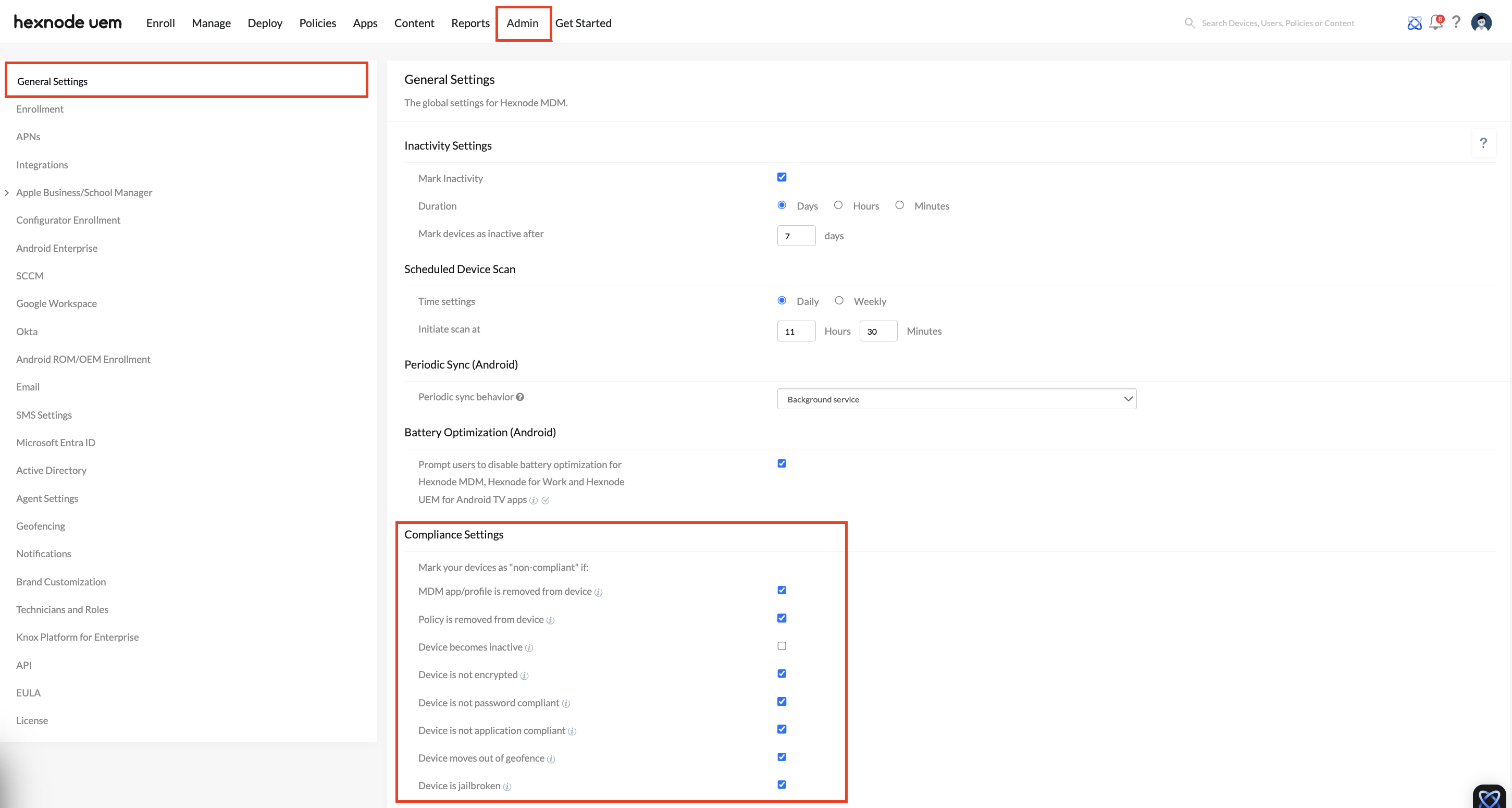
Device compliance criteria can be defined by IT administrators from the Hexnode UEM console, via Admin > General Settings > Compliance Settings.
Devices in Hexnode will be marked as non-compliant if they do not meet the defined criteria. These settings include the following:
- If the MDM app or the MDM profile is removed.
- If a policy assigned to the device is removed.
- If a device is not scanned for a specific number of days.
- If the device is not encrypted.
- If the device does not comply with organizational password policies.
- If the device has any applications blocklisted by the organization installed, or if any of the apps mandated by the organization are missing from the device.
- If a device moves out of a geofence (a location-based restriction with a predefined boundary set by the organization where the device should reside).
- If a device is identified as jailbroken.
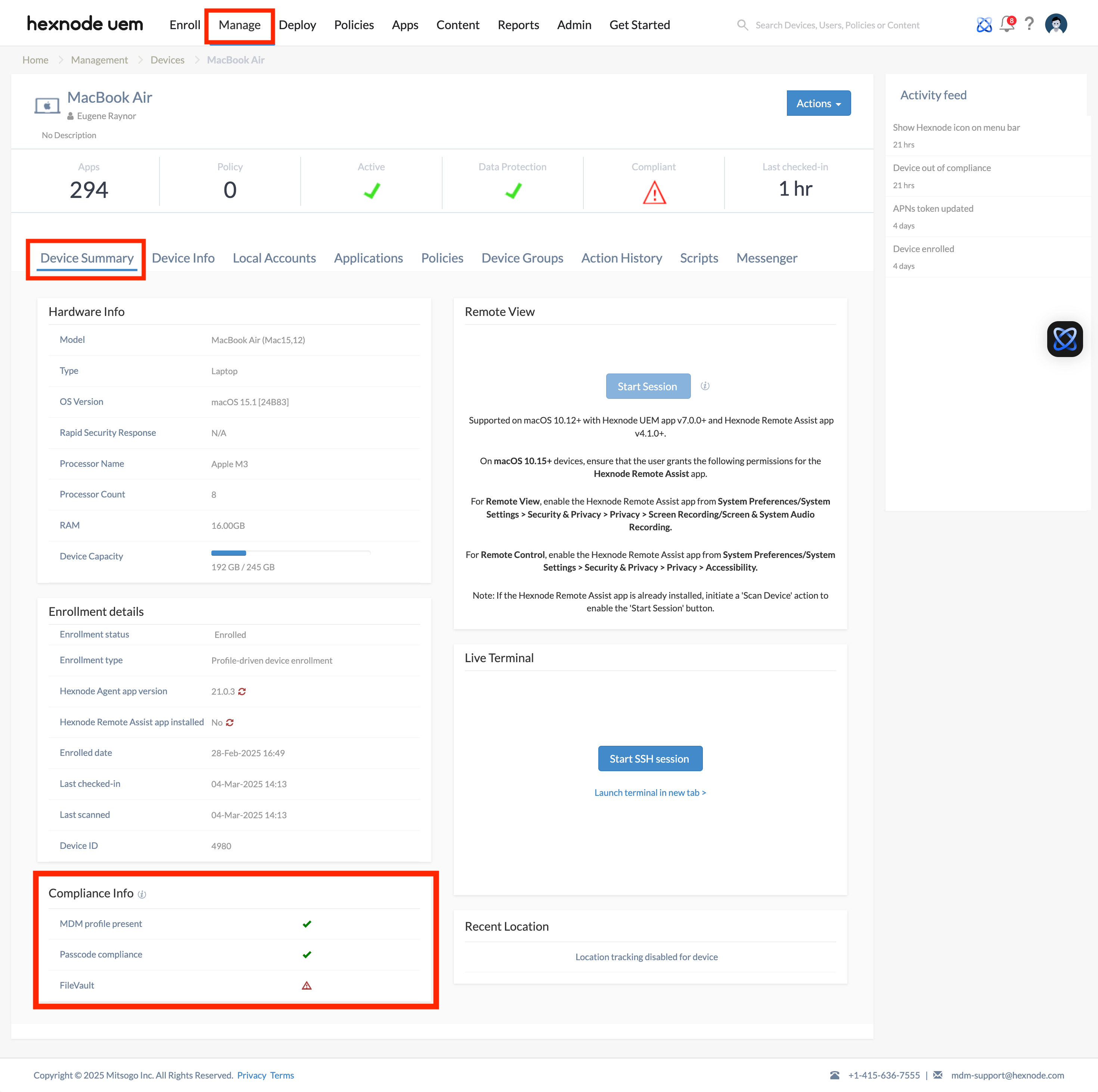
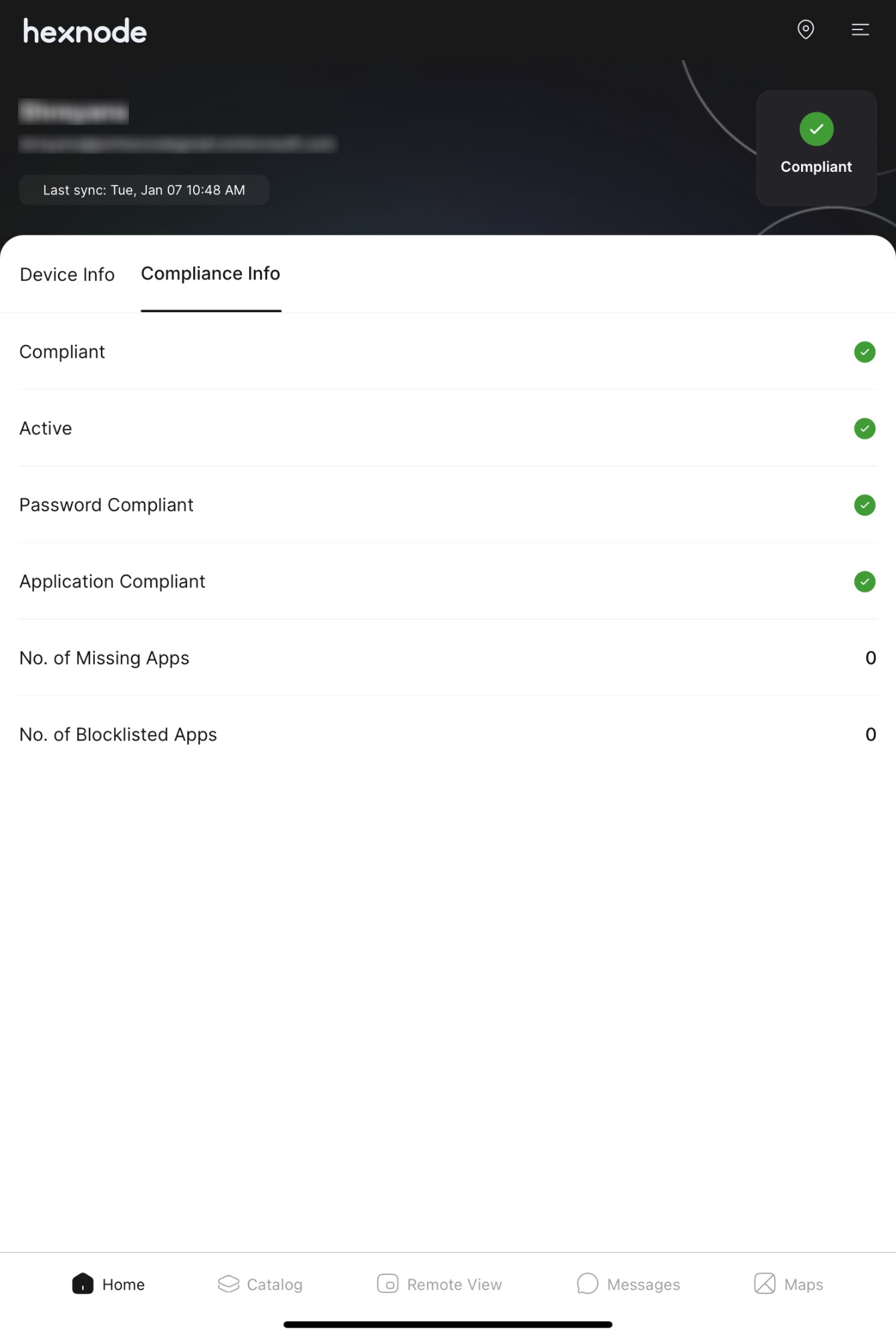
To check the compliance status of a device from the Hexnode UEM console, navigate to Manage > Devices > select a device > Device Summary > Compliance Info.
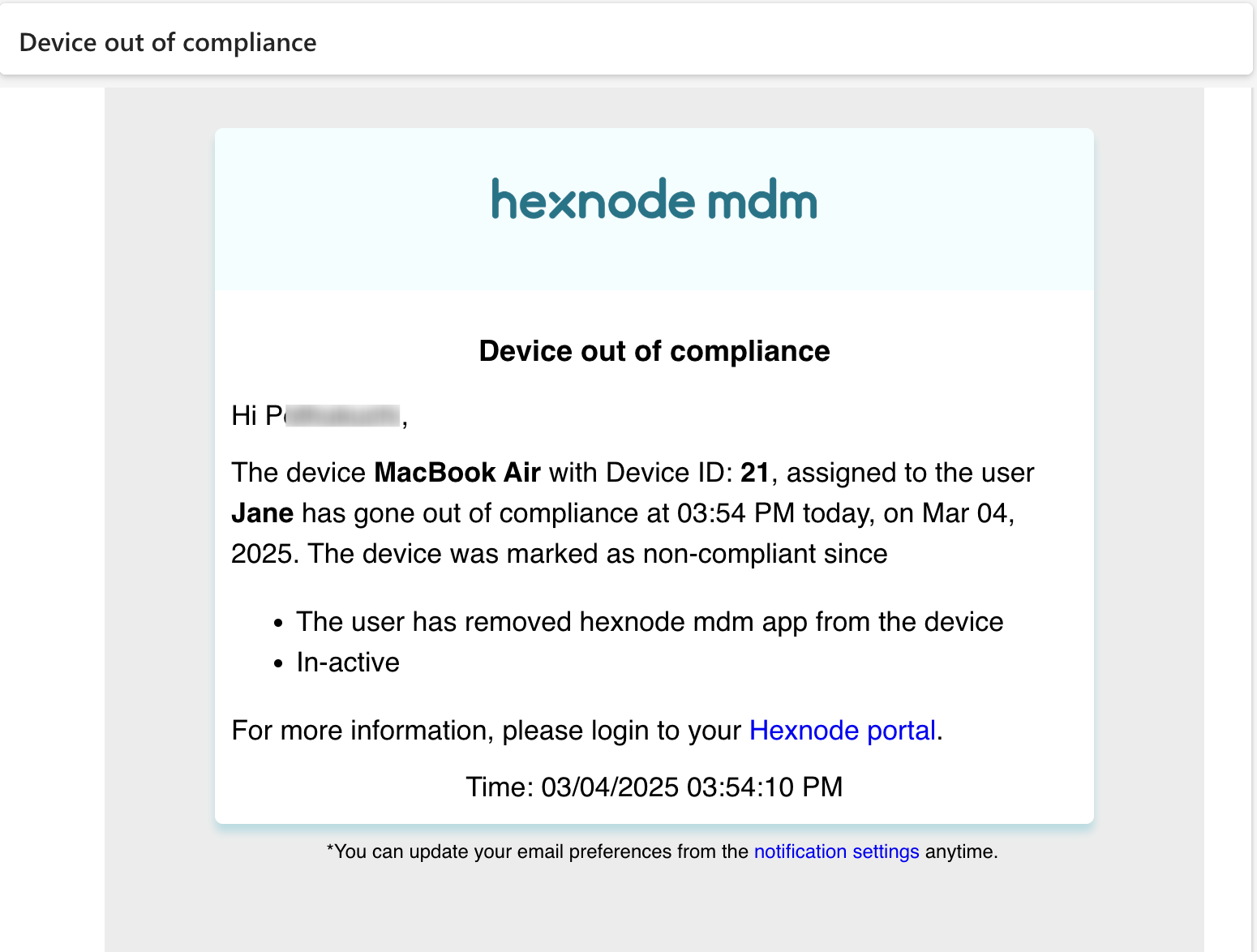
Hexnode UEM also provides Notification settings through which Administrators and associated users will be notified via email if any device turns non-compliant.
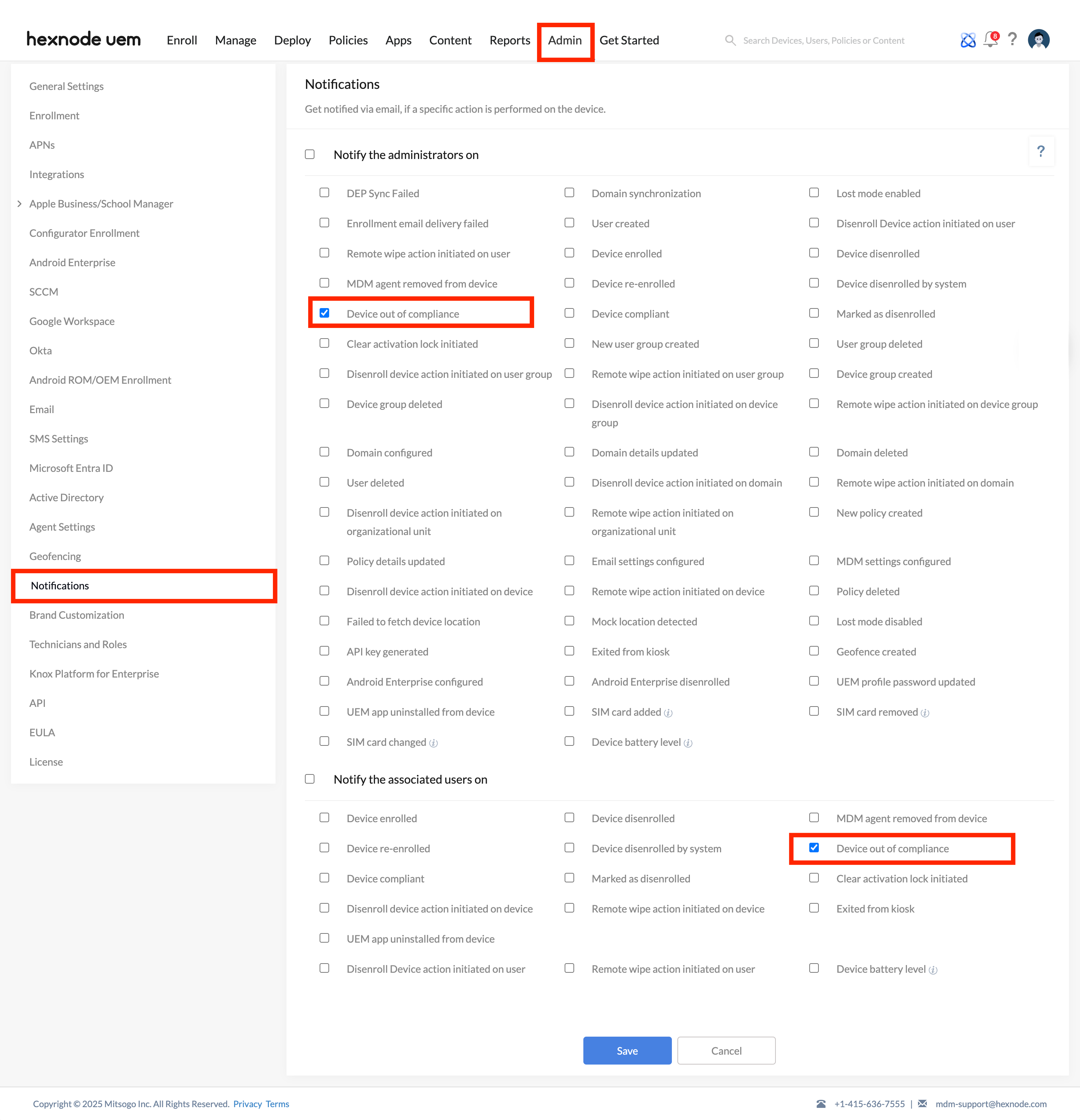
To ensure admins are notified of the compliance status of devices, navigate to Admin > Notifications. Under Notify the administrators on, check the field Device out of compliance. Additionally, you can check the same field under Notify the associated users on to notify users via email.
How to check compliance status at the device end?
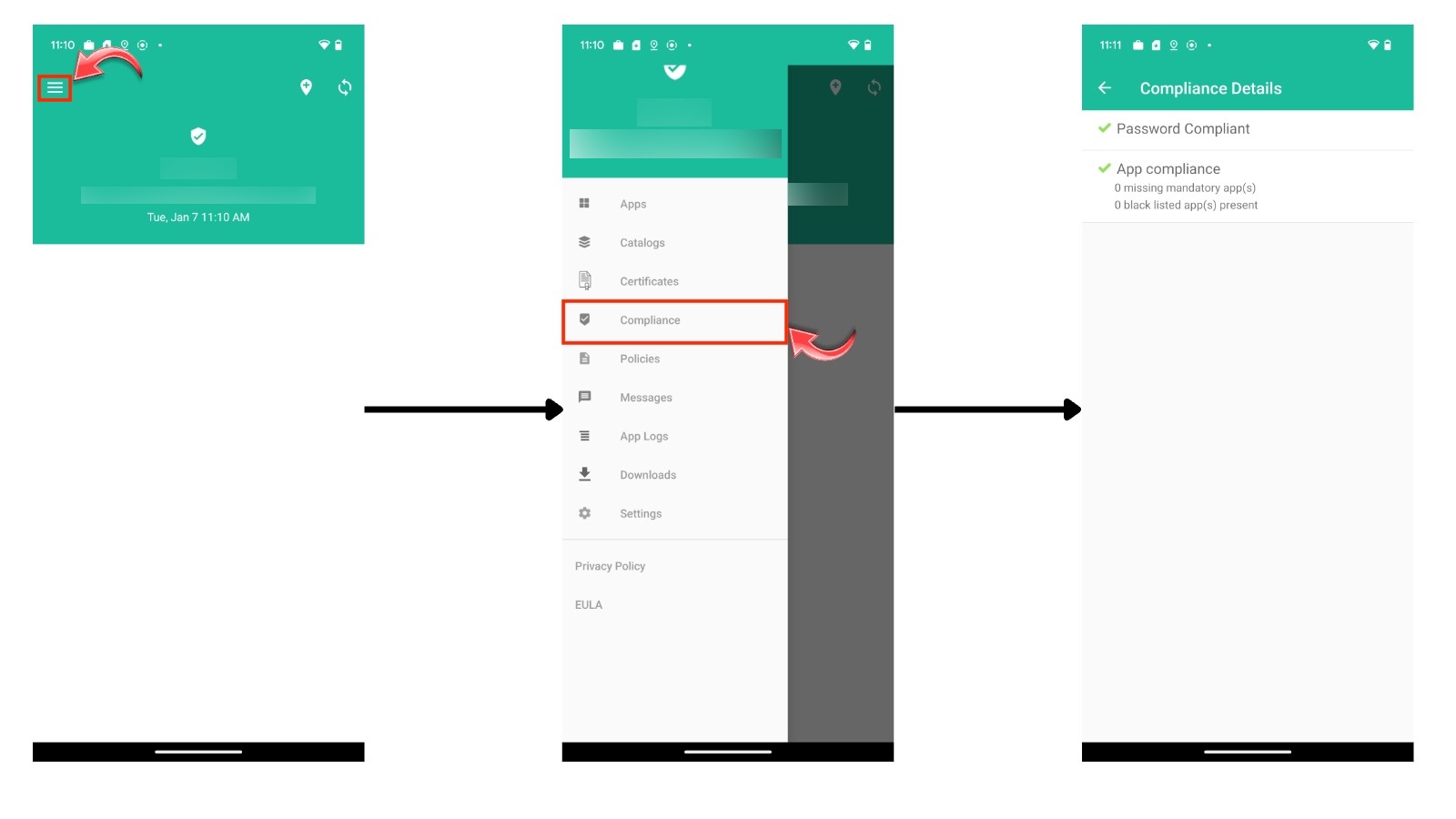
To verify if a device meets the compliance criteria, open the Hexnode UEM app and navigate to the Compliance section. The path to access this section varies by platform as follows:
Android
On Android devices, the compliance status can be accessed by clicking on the menu at the top left corner of the screen and selecting Compliance.
If the device does not comply with the organization’s password policies, it will be marked as password non-compliant.
If any required apps are missing or blocklisted apps are installed, the device will be marked as application non-compliant. Required apps are those that your organization mandates to be present on devices, while blocklisted apps are those that are prohibited. This field also shows the number of missing required apps and the number of blocklisted apps installed on the device.
Mac
On macOS devices, select Compliance from the left menu.
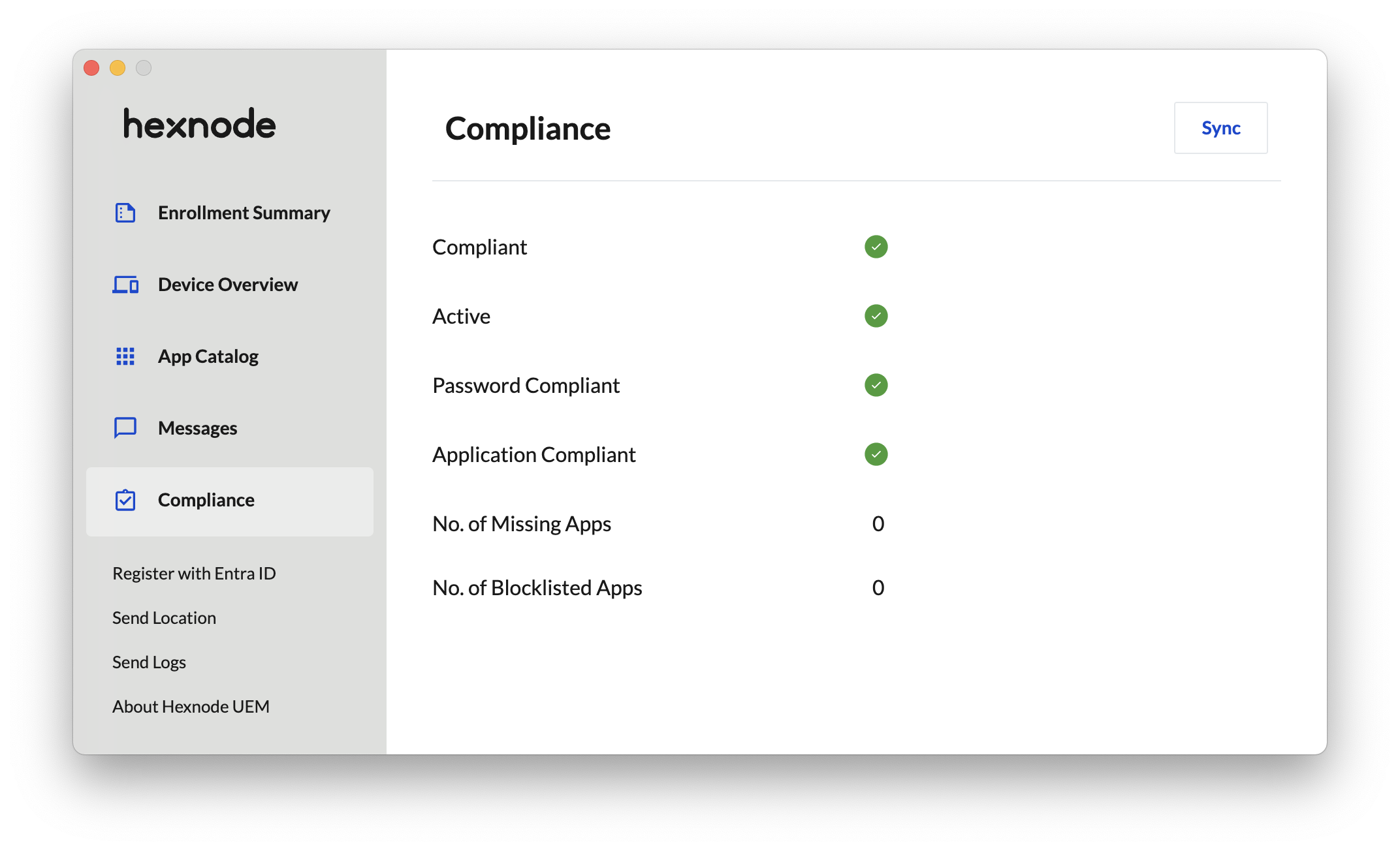
On macOS devices, the compliance information displays the following details:
- The overall compliance status of the device.
- Whether the device is actively connected with Hexnode UEM.
- Whether the device complies with the password rules set by the organization.
- Whether all required apps are installed and if any blocklisted apps are present. If not, the number of missing required apps and the number of blocklisted apps will be listed accordingly.
iOS/iPadOS
On iOS/iPadOS devices, the compliance status can be seen under the Compliance Info tab. This includes the overall compliance status of the device, whether it is actively connected with Hexnode UEM, and if it adheres to the password rules set by the organization. Additionally, it displays if any required apps are missing or if blocklisted apps are found, along with the specific number of each.
How to make a registered device compliant again?
When a Microsoft Entra ID registered device does not meet the compliance criteria set by the organization via Hexnode UEM, it cannot access organizational resources. When a user tries to log in to the configured resources, an error message, “Device must comply with your organization’s compliance requirement”, will be displayed.
Click on Check Compliance to review the device’s compliance status.
To restore compliance, the device must meet the specific criteria configured by your IT administrator in the Hexnode console. This includes adhering to organizational passcode policies, ensuring required apps are installed and no blocklisted apps are present, maintaining encryption standards, or remaining within confined areas (defined jurisdiction). It may also mandate that the device must remain active, retain its MDM app/profile, and not be jailbroken. The criteria set in the Hexnode solely determine the compliance of the device.
To ensure device compliance with organizational policies, follow these steps in the Hexnode UEM console:
- Required apps: To verify that the required apps are installed on the device, navigate to Manage > Devices > select the desired device > Applications. Use the search bar to find the apps. If an app is missing, perform a Scan Device remote action to sync the device details with Hexnode. If the app is still not listed, redeploy it to the device.
- Blocklisted apps: To check for blocklisted apps, go to Manage > Devices > select the desired device > Device Summary and review the Compliance Info tile. Verify under the Applications tab that there are no blocklisted apps based on your organization’s policy.
- Encryption standards: Ensure the device maintains encryption standards by checking the compliance settings configured in Hexnode for it. If encryption is not enabled, follow the necessary steps to enforce it.
- Geofencing: To verify if the device is staying within the confined areas (defined jurisdiction), review the policies that apply geofencing to the device. Make sure the device is within the designated geographic areas specified in the policy.
- Jailbroken devices: Check the device’s Compliance Info tile to determine if it is jailbroken. If it is, administrators should take immediate corrective actions, such as erasing/wiping/resetting the device to its factory settings to remove the jailbreak.
Once these conditions are fulfilled, the device will regain compliance status, enabling users to access organizational resources securely through Microsoft Entra ID.