Category filter
Configuration profile to enable private data in macOS Unified Logs
The following document helps IT administrators enable private data in macOS unified logs using a configuration profile.
Apple has replaced its traditional Apple System Log (ASL) with a new format called the Unified Logging System. The Unified Logging System is a more centralized, efficient, and secure logging system introduced with macOS 10.12 Sierra in September 2016. With unified logs, Apple has improved privacy during logging by masking sensitive information, such as user information and DNS queries, as private. This restriction prevents any applications from reading sensitive data from the logs. However, this can also be an issue for users trying to debug issues, as they won’t be able to access this information even with administrative privileges. With the help of the following configuration profile, private data in macOS unified logs can be enabled, allowing users to access it. IT administrators can deploy this configuration profile using Hexnode’s Deploy Custom Configuration feature.
Enable private data in unified logs
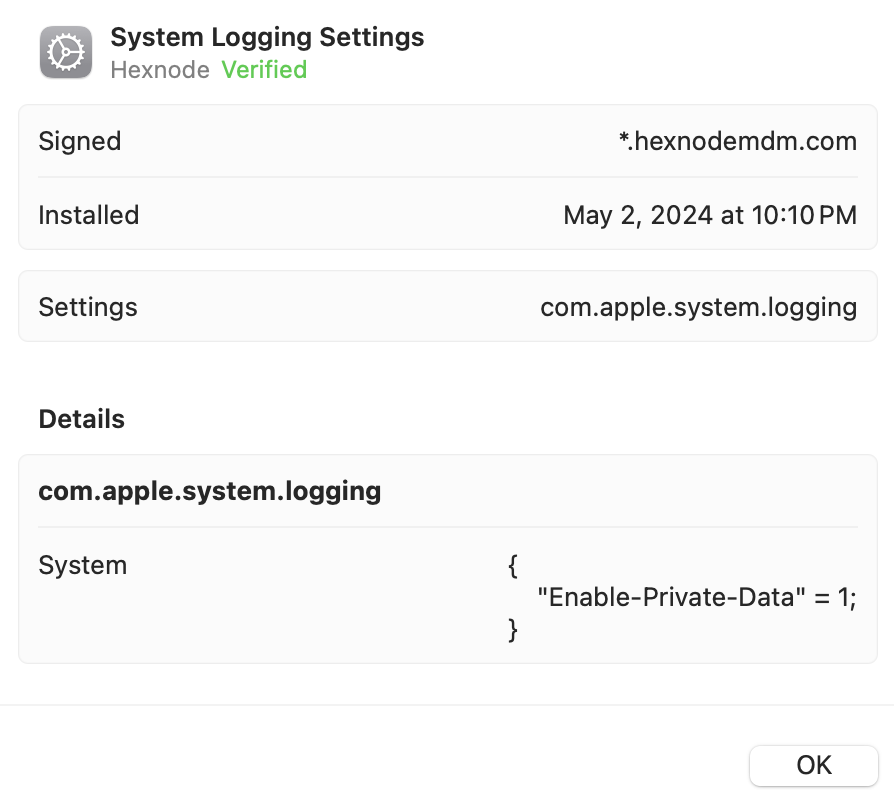
The following configuration profile uses the Enable-Private-Data key to enable access to private data in the macOS unified logs.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>System</key> <dict> <key>Enable-Private-Data</key> <true/> </dict> <key>PayloadIdentifier</key> <string>com.example.mysystemloggingpayload</string> <key>PayloadType</key> <string>com.apple.system.logging</string> <key>PayloadUUID</key> <string>0ff59613-35e9-495c-88c8-01963de4ac80</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDisplayName</key> <string>System Logging Settings</string> <key>PayloadIdentifier</key> <string>com.example.loggingconfig</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>F06807F4-7C54-4E4D-86D1-3B247A0534E9</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
What happens at the device end?
Upon successful installation of the configuration profile, it unlocks all the private data that will be logged from the moment of installation of the profile.
You can verify the profile installation by checking the profile corresponding to the System Logging Settings within the Profiles preferences.
To observe results at the device end, open the Terminal application on your Mac and enter the following command to view unified logs related to directory services:
sudo log stream --predicate '(subsystem == "com.apple.opendirectoryd") && (senderImagePath == "\/System\/Library\/OpenDirectory\/Modules\/PlistFile.bundle\/Contents\/MacOS\/PlistFile")'
Ensure that you have unlocked the ‘Users & Groups’ section in ‘System Preferences/System Settings’ using administrative credentials, as accessing OpenDirectory logs may require administrative privileges.