Category filter
How to configure VPN for visionOS from Hexnode?
A Virtual Private Network (VPN) enables secure and encrypted data transmission over the internet by creating a private network connection, allowing users to remotely connect to the organization’s network while ensuring secure access to corporate resources. With Hexnode, admins can easily configure VPN for visionOS devices.
Configure VPN settings via policy
To configure VPN settings via policy,
- Login to your Hexnode UEM portal.
- Navigate to Policies > New Policy. Assign a suitable name and description (optional) for the policy. You can also choose to continue with an existing policy.
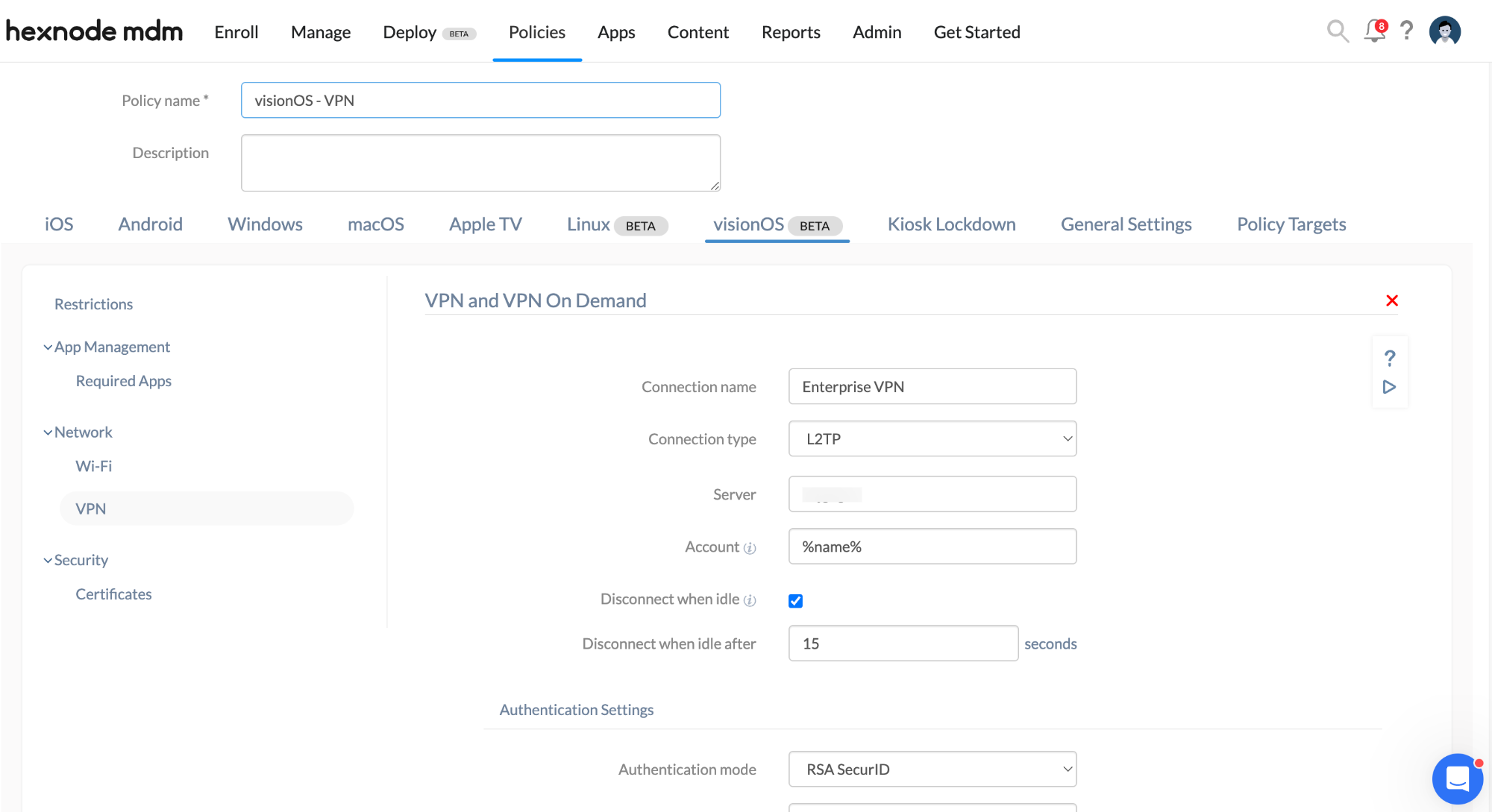
- Go to visionOS > Network > VPN, click Configure.
| VPN Settings | Description |
|---|---|
| Connection Name | Provide a name for the VPN connection to be shown in the devices. |
| Connection Type | Select the connection type and the rest of the settings change accordingly. The available connection types are: IKEv2, L2TP, IPSec(Cisco), Cisco AnyConnect, Juniper SSL, F5 SSL, SonicWALL Mobile Connect, Aruba VIA, Check Point Mobile VPN, and Open VPN. |
| Server | Provide the domain name of the server or the IP address of the server to which the devices get connected. |
| Account | Provide the username for authenticating to the VPN server. This field supports the use of wildcards. The supported wildcards are
|
| Disconnect when idle | Select this option to automatically disconnect the VPN after a specified period of inactivity. |
| Disconnect when idle after | Set the idle time duration from the drop-down menu. The VPN will automatically disconnect after the specified period of inactivity. |
Configuring IKEv2 Settings
| IKEv2 Settings | Description |
|---|---|
| Remote Identifier | Enter the remote identifier to identify the IKEv2 server. The supported formats are:
|
| Local Identifier | Enter the local identifier supplied by the VPN client and used by the mobile device. The supported formats are:
|
Authentication Settings
| Setting | Description |
|---|---|
| Authentication mode | Authentication consists of three options: None, Shared secret, and Certificate. Select one from the dropdown menu. |
Options available when Shared secret is selected
| Setting | Description |
|---|---|
| Shared secret | A second password required to establish a connection. Also known as pre-shared key, the shared secret is previously known to the device and the VPN server, and no one else. This key is used just to establish a connection and not used for encryption. |
Options available when Certificate is selected
| Setting | Description |
|---|---|
| Certificate | To authenticate using certificate, select an existing certificate profile. |
| Certificate type | Specify the encryption type used by the certificate. The available encryption types are: RSA, ECDSA256, ECDSA384, ECDSA521, and RSA-PSS. |
| Server certificate issuer common name | Provide the Server certificate issuer common name of the VPN server certificate to establish the VPN connection. |
| Server certificate common name | Provide the common name of the certificate itself. If left blank, the remote identifier value is used. |
| Enable certificate revocation check | When enabled, allows the device to check the certificates it gets from the VPN server against a Certificate Revocation List (CRL). Disabled by default. |
Advanced Settings
| Settings | Description |
|---|---|
| Extended authentication | Extended Authentication is an IKEv2 extension that requires remote VPN users to provide their usernames and passwords for authentication. This adds an extra layer of security to VPN connections, ensuring that only authorized individuals can access the network. |
| Username | Provide a username for the VPN server. |
| Password | Provide a password for the VPN server. |
| TLS maximum version | Select the maximum TLS version to use with EAP-TLS authentication from the drop-down menu. |
| TLS minimum version | Select the minimum TLS version to use with EAP-TLS authentication from the drop-down menu. |
| Dead Peer Detection Rate | Select how often the VPN client should send keepalive messages to the VPN server to verify the connection’s integrity. The available options are:
|
| Perfect forward secrecy | Enables Perfect Forward Secrecy (PFS) for your VPN connection. Doing so prevents past sessions from being decrypted. |
| Use IPv4/IPv6 internal subnet attributes | Select this option to enable both IPv4 and IPv6 tunnels for the VPN connection. |
| Disable IKEv2 server redirect | When checked, it ensures that the device will connect only to the specified server and will not follow redirection requests. |
| Enforce routes | Select this option to ensure that network traffic always travels through the VPN tunnel. |
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
| Security parameters | Select the configurations required for either IKE SA or Child SA parameters. |
The list of configurations required for IKE SA or Child SA security parameters include:
| Settings | Description |
|---|---|
| Encryption Algorithm | You can select one of the below algorithms:
|
| Integrity Algorithm | You can select one of the below algorithms:
|
| Diffie-Hellman Group | Select the required Diffie-Hellman group. The available groups are 1, 2, 5, 14(default), 15, 16, 17, 18, 19, 20, 21. |
| Lifetime (in minutes) | Enter a value (in minutes) between 10 and 1440 to specify the re-key interval.Default value is 1440 |
Configuring L2TP Settings
Authentication Settings
| Setting | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and RSA SecurID. Select one from the dropdown menu. |
Options available when Password is selected
| Settings | Description |
|---|---|
| Password | Provide the password as the authentication mode. |
| Shared secret | A second password required to establish a connection. Also known as pre-shared key, the shared secret is previously known to the device and the VPN server, and no one else. This key is used just to establish a connection and not used for encryption. |
| Send all traffic | Send all network traffic via VPN. Disabled by default. |
| Authentication plugin | Select an authentication plugin from the drop-down menu. The available options are EAP-RSA, EAP-TLS and EAP-KRB. |
Configuring IPSec (Cisco) Settings
| IPSec (Cisco) Settings | Description |
|---|---|
| Password | Provide the password for server authentication. |
Authentication Settings
| Setting | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Shared secret/group name and Certificate. Select one from the dropdown menu. |
Options available when Shared secret/group name is selected
| Settings | Description |
|---|---|
| Group name | The group name of the connection. |
| Shared secret | A second password, previously known to the device and the VPN server (and no one else), required to establish a connection. This key is not used for encryption, it is used just to establish a connection. |
| Use hybrid authentication | Enable this option to use hybrid authentication. Hybrid authentication is a more secure way of authentication by using a server-side certificate for the process. Hybrid authentication is disabled by default. |
| Prompt for password | The device prompts the user to provide the password. By default, the device will not prompt for password. |
Configuring Cisco AnyConnect Settings
| Cisco AnyConnect Settings | Description |
|---|---|
| Group name | The group name of the connection. |
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
Authentication Settings
| Settings | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and Certificate. Select one from the dropdown menu. |
| Password | Provide the password for authentication. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
Configuring Juniper SSL Settings
| Settings | Description |
|---|---|
| Realm | Provide the authentication realm. This is the server to which the device needs to be authenticated to. |
| Role | Assign a role to the user. In short, specify the resources which the users can access. |
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
Authentication Settings
| Settings | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and Certificate. Select one from the dropdown menu. |
| Password | Provide the password for authentication. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
Configuring F5 SSL Settings
| F5 SSL Settings | Description |
|---|---|
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
Authentication Settings
| Settings | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and Certificate. Select one from the dropdown menu. |
| Password | Provide the password for authentication. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
Configuring SonicWALL Mobile Connect Settings
| SonicWALL Mobile Connect Settings | Description |
|---|---|
| Login group or domain | The login group name or the domain name. |
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
Authentication Settings
| Settings | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and Certificate. Select one from the dropdown menu. |
| Password | Provide the password for authentication. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
Configuring ArubaVIA, Check Point Mobile VPN and Open VPN Settings
| Settings | Description |
|---|---|
| Include all networks | Select this option to route all network traffic through the VPN tunnel with some controllable exclusions. |
| Exclude APNs | Select this option to exclude network traffic for the Apple Push Notification service (APNs) from the VPN tunnel. This setting is available only when Include all networks is enabled. |
| Exclude local networks | Select this option to exclude all local network traffic from the VPN tunnel. This setting is only available when Include all networks is enabled. |
Authentication Settings
| Settings | Description |
|---|---|
| Authentication mode | Authentication consists of two options: Password and Certificate. Select one from the dropdown menu. |
| Password | Provide the password for authentication. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
VPN On Demand
When a VPN profile is set up, users must manually activate it, and it disconnects automatically when network connectivity is lost. VPN On Demand automates connections to the VPN on specified networks, removing the need for manual activation. You can customize these connections with multiple rules through the UEM console. VPN On Demand can be configured for all the Connection Types.
Enable VPN On Demand
To set up VPN On Demand, choose the authentication type as Certificate in Machine Authentication/User Authentication. Then, check the option VPN On Demand and then on + Add VPN On Demand Rule to set up the configurations.| Settings | Description |
|---|---|
| Action | Select the action that defines the VPN connectivity of the device based on the configured on-demand VPN rules. If the configured rules are satisfied, the selected action is carried out on the device. You can choose any one of the following actions:
Connect: Choose this action to unconditionally initiate an on-demand VPN connection whenever the system tries to connect to a network. The network connectivity will be blocked until the VPN connection is established. Disconnect: Choose this to disable the current VPN connection and to disable future on-demand VPN connections on the device. Evaluate Connection: Use this option to apply DNS settings with per-domain exceptions, allowing for specific domains to bypass the VPN when they match defined criteria. Ignore: Choose this to stop making new on demand VPN connections; however, the current VPN status of the device will be left unchanged. |
| Network type | Select the network type to be configured for VPN On Demand. The available options are Ethernet, Wi-Fi(default) and None. |
| SSID | Enter the SSID of a Wi-Fi network. The on-demand VPN configurations will take effect only if the device is connected to the specified network. You can add multiple SSID’s by clicking on the “+Add” icon. |
| Domain | Provide the domain name. The connection can only be established if the device’s current network search domain is added to this list. You can add multiple domains by clicking on “+Add”. |
| Server Address | Provide the IP Address. The VPN on-demand connection rules are satisfied only if the network’s specified DNS server addresses match the IP addresses added here. You can add multiple addresses by clicking “+Add”. |
| Probe URL | Enter an HTTP or HTTPS URL to probe. The VPN on-demand rule is fulfilled only if this URL is successfully fetched. If it succeeds, the URL will return an HTTP 200 OK response without any redirections.
If this field is left empty, the HTTP request does not factor into the VPN connection rules. |
Proxy Settings
The available values are None, Manual and Automatic.
- None – Select this option if you don’t want to set up a proxy server.
- Manual – To set up proxy manually, provide
- Server – The IP address or the domain name of the proxy server.
- Port – Port number of the proxy server.
- Authentication – Username required to connect to the proxy server.
- Password – Password which is required to authenticate to the proxy server.
- Automatic – If you’d like to set up proxy automatically, provide the proxy server URL.
DNS Settings
| Settings | Description |
|---|---|
| DNS protocol | DNS protocol consists of three options: None, Cleartext, HTTPS, TLS. Select one from the dropdown menu. |
Options available when Cleartext, HTTPS and TLS is selected
| Settings | Description |
|---|---|
| Domain name | Provide the name for the domain. |
| Certificate | To authenticate using certificate, select an existing certificate profile. |
| Server address | Select the required DNS server address from the dropdown menu. |
| Server name | Provide the hostname of a DNS-over-TLS server, which is used to validate the server’s certificate. This key is required only when the DNS protocol is set to TLS. |
| Server URL | Provide the URI template for a DNS-over-HTTPS server. |
| Search domains | Provide a list of domain strings that are used to fully qualify single-label host names. |
| Selective DNS routing | Provide a list of domains that should be resolved using the VPN’s DNS server, offering enhanced privacy and security. |
Associate the policies with visionOS devices
If the policy has not been saved,
- Navigate to Policy Targets > +Add Devices.
- Choose the target devices and click OK. Click Save.
- You can also associate the policy with device groups, users, user groups or domains from the left pane of the Policy Targets tab.
If you have the policy saved already,
- Go to Policies tab and choose the desired policy.
- Click on the Manage drop-down and select Associate Targets.
- Choose the target entities and click Associate.