Category filter
Configuration profile to manage Chrome apps and extensions on Mac
Whether it’s enforcing installation policies or blocking unauthorized extensions, managing Google Chrome apps and extensions allows admins to provide a secure browsing environment for the users. Admins can easily deploy, configure, and update apps and extensions across devices to enhance productivity and enforce security measures for their users.
With the help of Hexnode UEM, you can remotely manage apps and extensions on Chrome browsers for multiple macOS devices by deploying a configuration profile.
To manage Chrome apps and extensions using the method mentioned below, the Chrome browser on users’ devices must be managed by the organization. To enroll cloud-managed Chrome browsers, sign up for Chrome Browser Cloud Management (CBCM), generate an enrollment token, and add devices to the console.
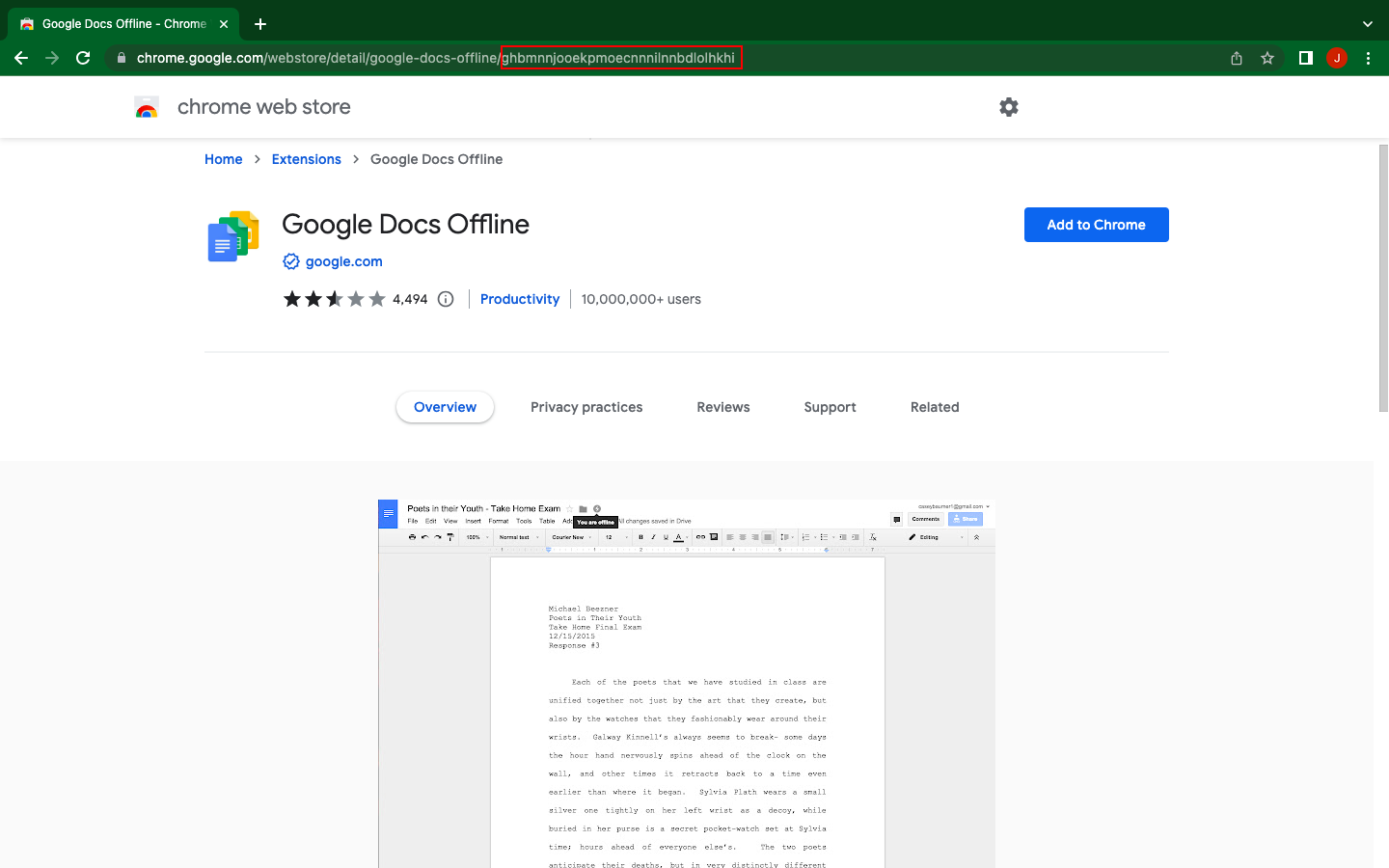
To enforce settings for a particular Chrome app or extension, it is essential to identify the app/extension. Each app and extension available on the Chrome Web Store has a unique identification (ID) that remains the same across different versions.
To locate an app or extension ID:
- Go to Chrome Web Store.
- Find and click on the desired app or extension.
- The app or extension ID can be found at the end of the URL as a 32-character string. For example, ID for Google Docs Offline is ghbmnnjooekpmoecnnnilnnbdlolhkhi.
Create a configuration profile that includes all the necessary settings. Use the ExtensionSettings policy to manage extensions in the Chrome browser. With this policy, you can:
- Set a default policy that applies to all apps and extensions using the * key.
- Control the installation behavior and permissions of extensions, and customize the settings for individual apps or extensions using their unique app or extension ID.
You can choose to block, allow, automatically install or force install apps and extensions on users’ Chrome browsers.
You can set the installation mode using the following keys:
- allowed: Users can install apps and extensions from the Chrome Web Store. This is the default key if no installation mode is specified in the profile.
- blocked: Users are restricted from installing apps or extensions from the Chrome Web Store. A custom error message (up to 1000 characters) can be defined to inform users about the block using the blocked_install_message key.
- force_installed: Extensions specified in this key are automatically installed without user interaction. Users cannot disable or remove these extensions. The download location for the extensions also needs to be defined.
- normal_installed: Extensions specified in this key are automatically installed without user interaction. Users have the option to disable these extensions. The download location for the extensions also needs to be defined.
When you choose to automatically install an extension on devices, you must specify the download location in Chrome within the configuration profile using the update_url key.
Define the extension download location:
- If the extension is available on the Chrome Web Store, use the URL: https://clients2.google.com/service/update2/crx.
- If you are hosting the extension on your own server, provide the URL from which Chrome can download the packed extension in the .crx file format.
Prevent users from installing apps and extensions that request a specific permission. Specify the permission as the value for the blocked_permissions key.
Refer Chrome app and extension permissions to get a list of permissions that can be blocked from the ‘API’ column in the table provided.
Prevent the extensions from modifying specific websites. It’s important to note that this setting does not limit the installation or removal of extensions.
You can configure the following settings. Along with them, specify the website URLs that you want to prevent the apps and extensions from modifying.
- runtime_blocked_hosts: Restricts extensions from interacting with the websites specified here.
- runtime_allowed_hosts: Allows extensions to interact with the specified websites, even if they are listed in runtime_blocked_hosts.
The format of host patterns is [http|https|ftp|*]://[subdomain|*].[hostname|*].[eTLD|*],
The required components are [http|https|ftp|*], [hostname|*], and [eTLD|*], while [subdomain|*] is optional.
Here are a few examples for specifying the host pattern.
| Accepted host patterns | Matches | Doesn’t match |
|---|---|---|
| *://*.hexnode.* | http://hexnode.com https://academy.hexnode.co.uk |
https://hexnode.google.com http://hexnode.google.co.uk |
| http://hexnode.* | http://hexnode.com http://hexnode.ly |
https://hexnode.com http://academy.hexnode.com |
| http://hexnode.com | http://hexnode.com | https://hexnode.com http://academy.hexnode.co.uk |
| http://*.hexnode.com | http://hexnode.com http://academy.hexnode.com http://z.z.hexnode.com |
https://hexnode.com https://academy.hexnode.com |
| http://hexnode.co.* | http://hexnode.co.com http://hexnode.co.co.uk |
http://hexnode.co.uk |
| http://*.academy.hexnode.com | http://z.academy.hexnode.com | http://not.hexnode.com |
| *://* | All Urls |
Invalid host patterns
- http://*hexnode.com
- http://hexnode.com/
- http://hexnode.com/*
- http://z.*.hexnode.com
- http*://hexnode.com
Sample configuration profile
You can use the Deploy Custom Configuration feature to deploy the below sample configuration profile, which:
- Blocks all apps and extensions, except for Google Translate (aapbdbdomjkkjkaonfhkkikfgjllcleb).
- Displays a generic message “This extension is blocked” if the user tries to add blocked extensions. If the user tries to add Google Docs Offline (ghbmnnjooekpmoecnnnilnnbdlolhkhi), they will get the message “Request IT admin to get this extension”.
- Restricts the extension from accessing https://www.wikipedia.org webpage.
- Block all extensions that capture audio directly from microphone.
- Automatically install Google Keep Chrome extension (lpcaedmchfhocbbapmcbpinfpgnhiddi) without giving users the option to disable it.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadContent</key> <dict> <key>com.google.Chrome</key> <dict> <key>Forced</key> <array> <dict> <key>mcx_preference_settings</key> <dict> <key>ExtensionSettings</key> <dict> <key>*</key> <dict> <key>installation_mode</key> <string>blocked</string> <key>blocked_install_message</key> <string>This extension is blocked</string> <key>runtime_blocked_hosts</key> <array> <string>https://www.wikipedia.org</string> </array> <key>blocked_permissions</key> <array> <string>audioCapture</string> </array> </dict> <key>lpcaedmchfhocbbapmcbpinfpgnhiddi</key> <dict> <key>installation_mode</key> <string>force_installed</string> <key>update_url</key> <string>https://clients2.google.com/service/update2/crx</string> </dict> <key>aapbdbdomjkkjkaonfhkkikfgjllcleb</key> <dict> <key>installation_mode</key> <string>allowed</string> </dict> <key>ghbmnnjooekpmoecnnnilnnbdlolhkhi</key> <dict> <key>blocked_install_message</key> <string>Request IT admin to get this extension</string> <key>installation_mode</key> <string>blocked</string> </dict> </dict> </dict> </dict> </array> </dict> </dict> <key>PayloadDisplayName</key> <string>Google Chrome extension settings</string> <key>PayloadEnabled</key> <true/> <key>PayloadIdentifier</key> <string>com.Chrome.75AD74EC-C4A4-428D-893E-E4877F0D8804</string> <key>PayloadType</key> <string>com.apple.ManagedClient.preferences</string> <key>PayloadUUID</key> <string>75AD74EC-C4A4-428D-893E-E4877F0D8804</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDescription</key> <string>Chrome apps and extension policy</string> <key>PayloadDisplayName</key> <string>Google Chrome extension settings</string> <key>PayloadIdentifier</key> <string>macOS.A837FD2C-9088-4957-B6E9-9C5575007337</string> <key>PayloadOrganization</key> <string>CompanyName Inc.</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadScope</key> <string>System</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>5D542BFF-21AC-4E7F-A05C-AAED3B4E9E19</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
After associating the configuration profile, you can remotely fetch a list of the installed Google Chrome extensions on the macOS device with the help of a script. Alternatively, you can check the device to ensure that all settings in the profile is applied to its Chrome browser.
Here are the steps to follow:
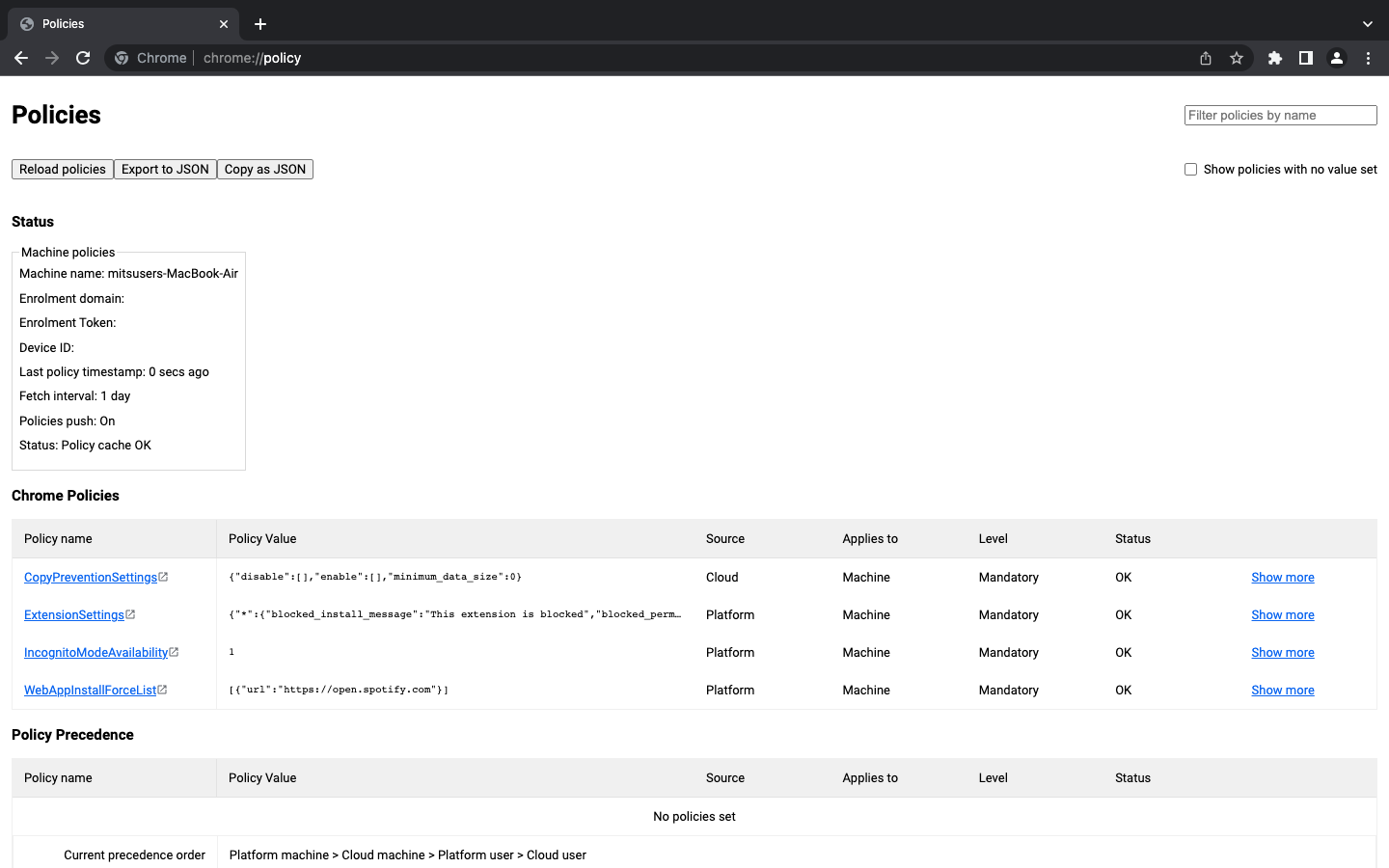
- Open the Chrome browser.
- Enter chrome://policy in the URL field.
- Click on Reload policies to ensure the latest policies are applied.
- Enable the Show policies with no value set option to view all policies.
- Verify that the Status is set to OK and confirm that the policy values match the configurations you have set.