Category filter
Script to enable the Downloads folder in kiosk
In multi-app kiosk mode, the device is restricted to a list of approved applications. It also restricts access to files and folders like all other functionalities. Though the kiosk mode induces limitations on device usage, you can add exemptions to the functionalities restricted. For instance, to make the company relevant data downloaded from the web accessible to the user (even when the device is in a kiosk), you can grant access to the downloaded files.
From Windows 10 version 1809 onwards, it is possible to grant explicit access to the Downloads folder on a device locked in multi-app kiosk mode. The doc explains how administrators can execute a script on Windows devices after configuring the multi-app kiosk lockdown policy to grant access to the Downloads folder.
To grant user access to the Downloads folder in File Explorer, the admin can perform the following steps either while creating the multi-app kiosk policy or editing the already associated multi-app kiosk policy:
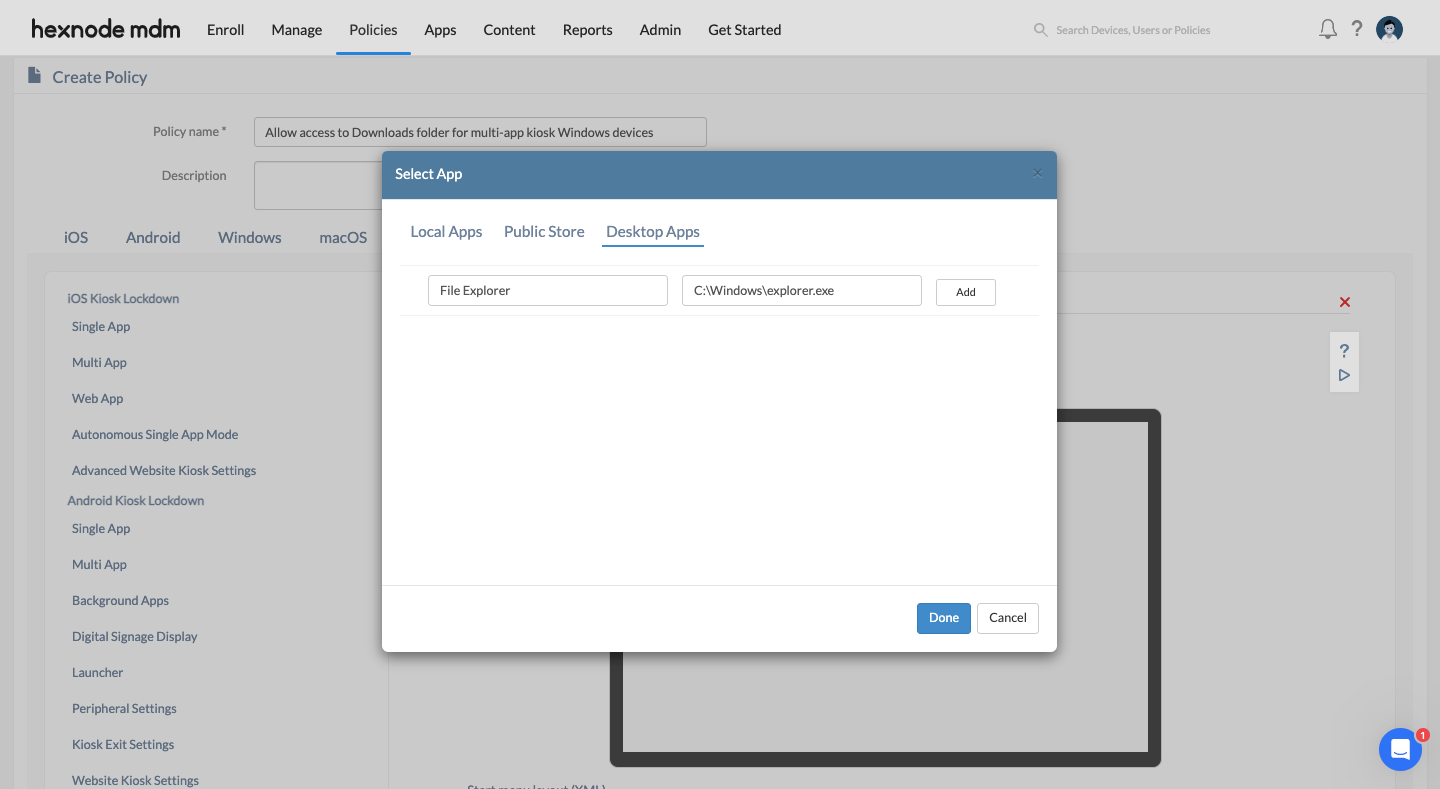
- While setting up the multi-app kiosk policy, add File Explorer as a desktop app:
- Enter the Kiosk account name.
- Click on the + button and select Desktop Apps. Provide the app name as File Explorer and its location C:\Windows\explorer.exe.
- Click on the Add button.
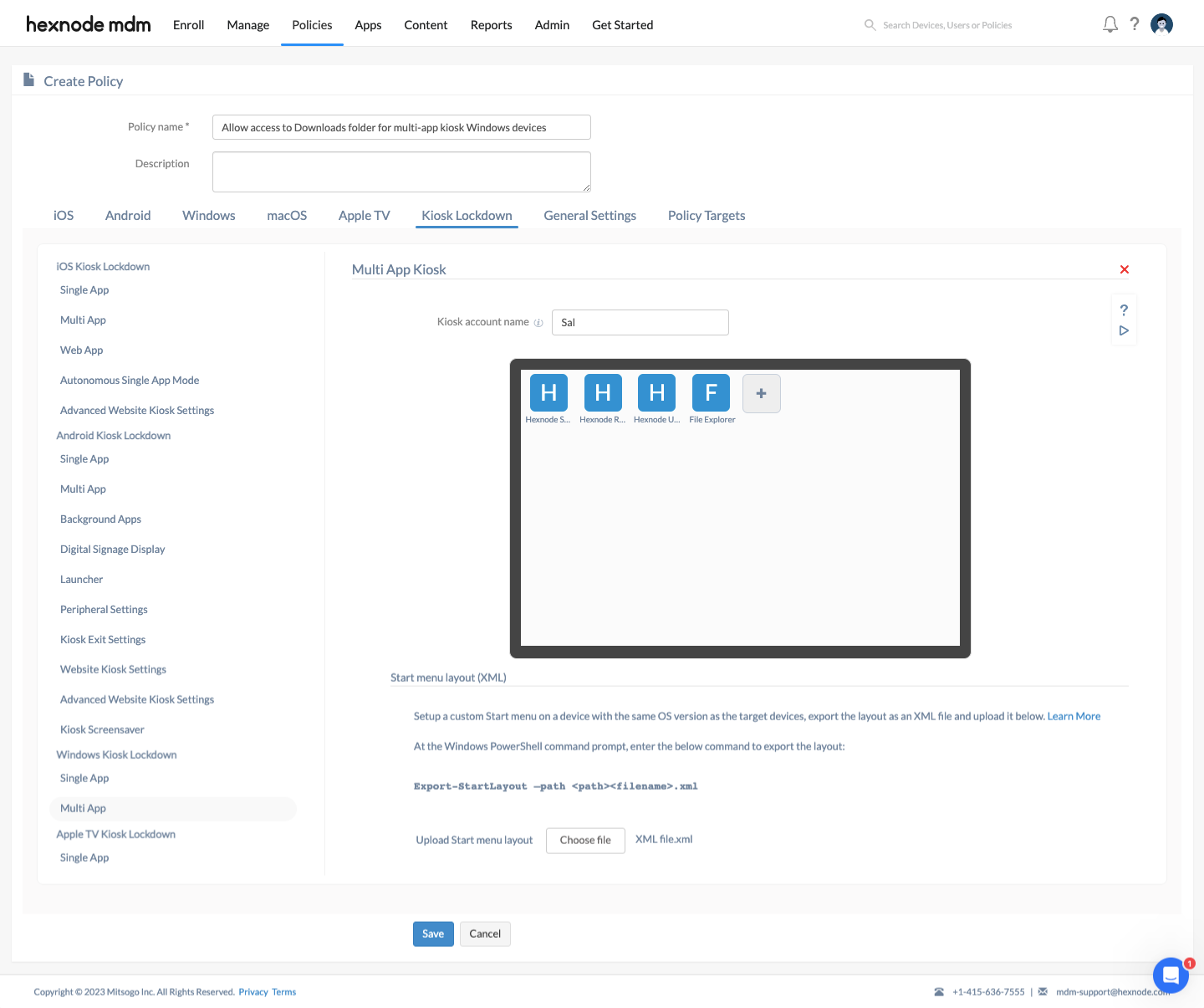
- Customize the start layout with the File Explorer application, and then export the updated start layout.
- Import the Start layout .xml file to this policy.
- Associate devices/groups and save the policy.
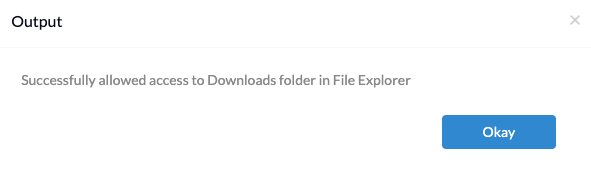
- After successfully applying the policy, execute the below PowerShell script to those devices/groups using the Execute Custom Script action.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
try { $nameSpaceName="root\cimv2\mdm\dmmap" $className="MDM_AssignedAccess" $obj = Get-CimInstance -Namespace $namespaceName -ClassName $className $configuration = $obj.configuration #checking whether kiosk policy is configured or not if(-not($configuration)) { Write-Host "Multi app kiosk policy is not applied in the device, Please configure it before executing this script." return } #including namespace for allowing fileexplorer restrictions. $conf1 = $configuration if(-not($configuration.Contains("xmlns:v2="))) { $v2nameSpace = @" xmlns="http://schemas.microsoft.com/AssignedAccess/2017/config" xmlns:v2="http://schemas.microsoft.com/AssignedAccess/201810/config" "@ $conf1 = $configuration.replace('xmlns="http://schemas.microsoft.com/AssignedAccess/2017/config"', $v2nameSpace) } #allowing downloads folder in file explorer $conf2 = $conf1 if(-not($conf1.Contains("<v2:FileExplorerNamespaceRestrictions>"))) { $downloads = @" </AllAppsList> <v2:FileExplorerNamespaceRestrictions> <v2:AllowedNamespace Name="Downloads"/> </v2:FileExplorerNamespaceRestrictions> "@ $conf2 = $conf1.replace('</AllAppsList>', $downloads) } Add-Type -AssemblyName System.Web $obj.configuration = [System.Web.HttpUtility]::HtmlEncode($conf2) Set-CimInstance -cimInstance $obj Write-Host "Successfully allowed access to Downloads folder in File Explorer" } catch { Write-Host $_.Exception.Message } |
Once the script is executed successfully, users will have access to the Downloads folder both through File Explorer and via a web browser.