Take your smartphone or laptop and perform a quick scan of the WiFi networks around you. What do you see? Chances are you’ll see a bunch of WiFi names (also called the SSID), along with their transmission frequencies. However, you’re missing out on a crucial piece of information. The security protocol they run on.
Why is this information important? Don the shoes of an attacker. He’s determining his next target. He takes a quick scan of the WiFi networks around him. What does he check for? Not the SSID, not transmission frequency, but the WiFi protocol it operates on.
He spots a well-used network with a weak security protocol, and his eyes light up like a Christmas tree.
With the ubiquity of the internet, attackers like these who try to exploit such security flaws are growing in enormous numbers.
The good news is, you get to be the grinch who ruins their Christmas, simply by securing your network with the right WiFi security protocols.
WPA vs WPA2 – How to choose the right wireless (WiFi) security for your network
An essential aspect of securing your corporate or home network is understanding the differences between the available security protocols and implementing the one suitable for your use cases.
Let us observe and assess a thorough evaluation of the two most common WiFi security protocols used by businesses and individuals – WPA vs WPA2 – and determine which security protocol is suitable for your use case.
What is WiFi Protected Access (WPA)?
WiFi Protected Access (WPA) was introduced in 2003 as a secure encryption protocol designed to replace the flawed Wired Equivalent Privacy (WEP) method and patch up its vulnerabilities. WPA enforces enhanced encryption capabilities including,
TKIP is a dynamic 128-bit encryption key introduced to replace the static encryption key utilized by WEP. Also, the TKIP algorithm is designed to allow users of legacy WLAN equipment to upgrade to TKIP without replacing hardware.
MIC prevents attacks on encrypted packets transmitted via the network. Here, an attacker intercepts, alters and retransmits an encrypted message sent over the network. With MIC implemented, these packets are made tamper-proof.
PSK is used to unlock an encrypted message sent over the network. It helps resist brute force attacks where hackers try to break the encryption after intercepting transmitted data packets. However, even with these capabilities, WPA does share its set of vulnerabilities.
What are the vulnerabilities in WPA?
Even though WPA has a more secure encryption process when compared to its predecessor (the WEP), the TKIP encryption system introduced in the new protocol had to consider being backwards compatible with old generation WEP devices. Hence, the WPA protocol recycled some elements of the compromised old gen WEP system and, of course, those same vulnerabilities ultimately appeared in the new WPA system.
Wi-Fi Protected Setup (WPS) is a network security standard available in many WPA-supported routers. However, WPS was created with convenience in mind. As a result, connecting to the network via WPS typically involves a huge trade off with security. An attacker who manages to obtain the WPS 8-digit PIN using brute force techniques can easily authenticate to your network and extract your WiFi password.
What is WiFi Protected Access 2 (WPA2)?
WPA2 is a WiFi security protocol introduced as a successor to WPA to patch the vulnerabilities of the previous system. WPA2 replaced TKIP with advanced encryption techniques including,
AES is a block cipher that operates on discrete data blocks using a fixed key and a formula. Compared to the RC4 stream cipher, (the encryption cipher used by WPA), AES offers enhanced encryption and robust security for wireless networks.
The CCMP encryption protocol is based on the Advanced Encryption Standard (AES) encryption algorithm. CCMP offers enhanced security when compared with TKIP. However, the enhanced privacy and security of CCMP requires additional processing power, often requiring new hardware.
WPA2 operates on two modes:
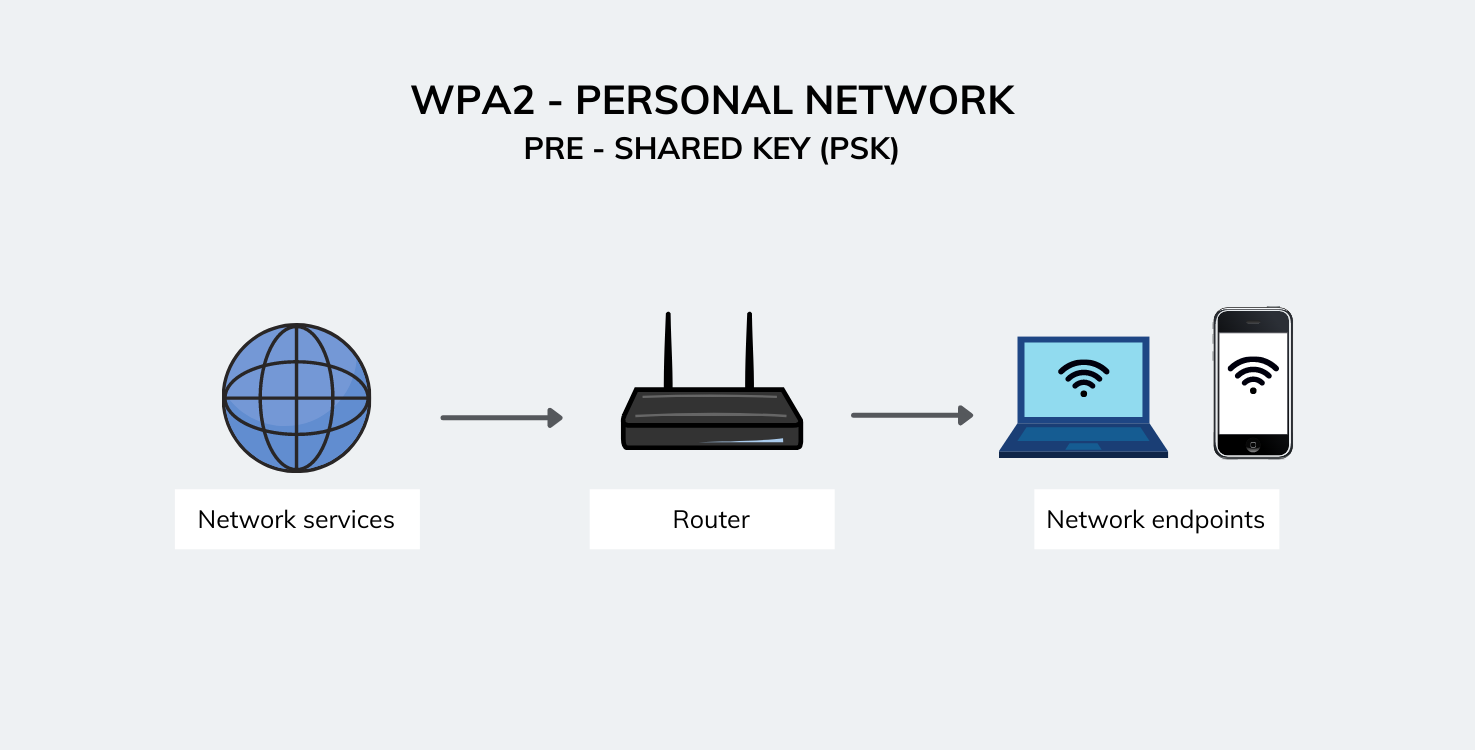
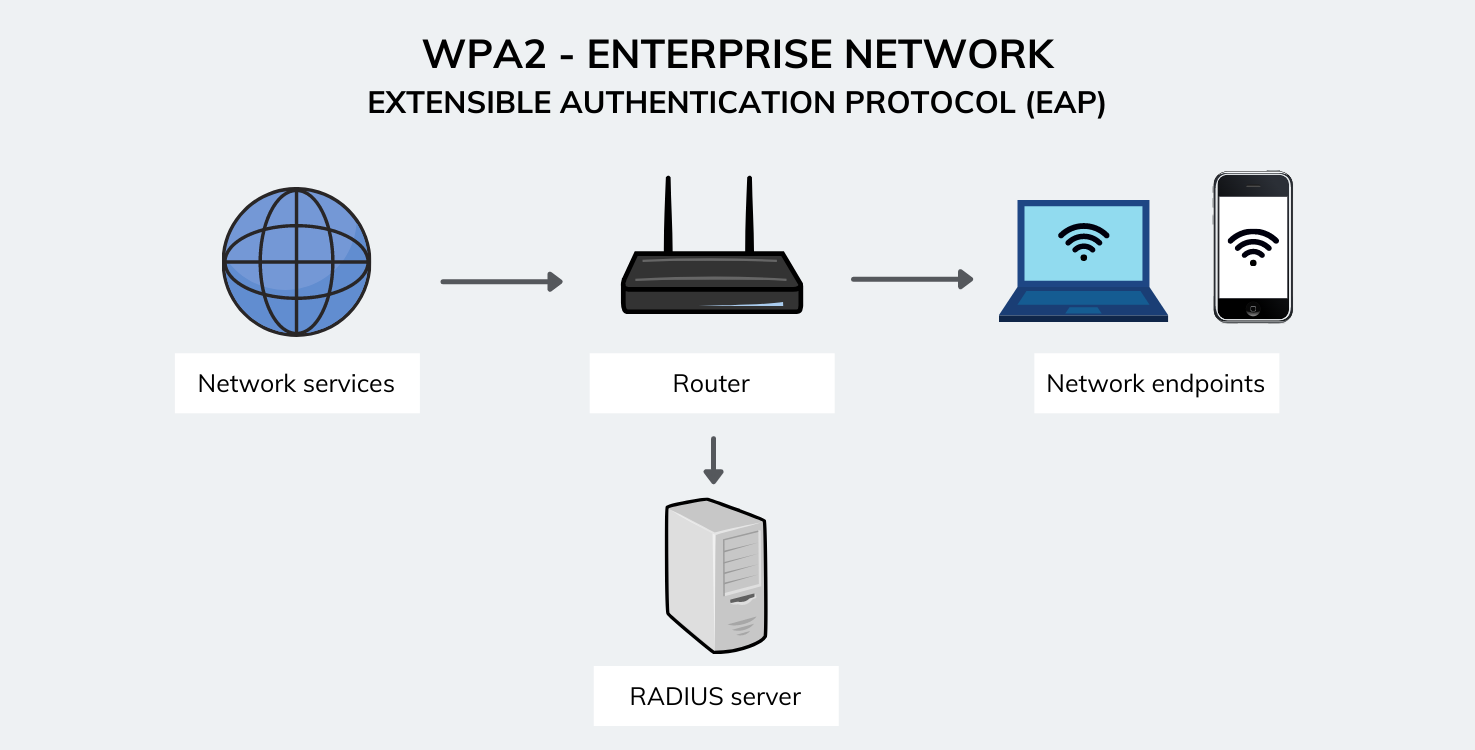
- WPA2 Personal (PSK) – This mode is usually used in residential environments.
- WPA2 Enterprise (EAP) – This mode is more suited to organizational or business use.
What are the vulnerabilities in WPA2?
Although WPA2 networks are extremely secure, vulnerabilities have managed to crack the WPA2 security protocol and decrypt data within the network. The most notable being the key reinstallation attack (KRACK).
In a KRACK attack, the attacker tricks the victim into reinstalling an already-in-use key, by manipulating cryptographic handshake messages. More specifically, the 4-way handshake of the WPA2 protocol. This handshake is conducted when a user wants to join a protected WPA2 network, and is used to verify that both the user and access point uses the correct credentials.
By taking advantage of this vulnerability, the attacker is able to steal sensitive information, manipulate data, and inject ransomware or malware into websites.
However, this vulnerability can be resolved by updating your endpoints and your router to the latest security updates and patches.
WPA vs WPA2 – Comparison table
| WiFi Protected Access (WPA) | WiFi Protected Access 2 (WPA2) | |
| Year of introduction | 2003 | 2004 |
| Data encryption method | Temporal Key Integrity Protocol (TKIP) | CCMP with Advanced Encryption Standard (AES) |
| Cipher type | RC4 stream cipher | AES block cipher |
| Security strength | Weaker security when compared to WPA2 | Offers increased security and privacy when compared to WPA |
| Data integrity method | Message Integrity Code (MIC) | Cipher Block Chaining message (CBC – MAC) |
| Compatibility | Does not require new hardware | Requires new hardware that features 2006 and above models of Network Interface Cards (NIC) |
| Ease of deployment | Easy to deploy and configure | Requires complicated setup especially with WPA2-EAP |
| Enterprise usage | Does not provide enterprise solutions | Has enterprise solutions |
| Processing power | Requires minimal processing power | Requires more processing power |
The verdict – WPA vs WPA2
When comparing the features of WPA vs. WPA2, WPA2 will be the most suitable option to secure your wireless (WiFi) network.
“The only downside to WPA2 is the need for more processing power and its incompatibility with older hardware.”
With these attributes in mind, let us assess precisely when we should go for a WPA network over a WPA2 network.
When should you choose WPA
WPA has a less secure encryption method, and there isn’t an enterprise solution to support business usage.
However, if you have older hardware, WPA can be used with minimal processing power and could be the better option presuming you’re willing to make compromises in security.
When should you choose WPA2
WPA2 is ideal for both residential and business use cases. It provides advanced security with AES-CCMP encryption and a dedicated enterprise solution to support business networks.
WPA2 has been the industry standard for wireless (WiFi) protocols since its introduction, with the Wi-Fi Alliance stating that all future devices with the Wi-Fi trademark have to use WPA2 for security.
Is choosing the right WiFi security protocol enough to protect your wireless network?
Nope. The journey to securing your wireless (WiFi) network does not end with choosing a wireless security protocol. It is just as essential to configure your wireless network effectively to ensure it is safe from any potential attacks or vulnerabilities. You can also use the assistance of a Unified Endpoint Management solution to streamline and deploy network security configurations to managed devices.
Check out to know more about the emerging device platforms and how Unified Endpoint Management(UEM) solutions help enterprises manage these devices better.

Featured resource
Understanding Unified Endpoint Management (UEM)
Here are 12 additional steps you can adopt to secure your wireless (WiFi) network.
12 steps to secure your wireless (WiFi) network

1: Use UEM to push Wi-Fi network configurations
When pushing WiFi configurations using a UEM solution like Hexnode, you can configure the WiFi PSK (password) in the configuration profile and push then to the required endpoints, thereby avoiding the need to provide users with the PSK. This, in turn reduces the chances of your PSK being exposed.
Wi-Fi Security: Tips to secure data across public Wi-Fi networks
2: Update your firmware and software
Ensure your software and network device firmware are updated to the latest security patches. Hardware and software manufacturers usually patch out any new vulnerabilities that may have occurred by providing the latest security patches. Ensure you stay updated with these patches.
3: Push VPN configurations
Configuring a VPN to encrypt local traffic is a smart move that offers additional protection for your network. It provides a secure encrypted channel for traffic flow, making it extremely challenging for attackers to monitor your network. Use Hexnode to push VPN configurations in bulk to all your enterprise devices.
On-Demand, Per App or Always On? Choosing the right VPN for Apple devices
4: Enforce minimum Wi-Fi security level for managed devices to connect
With UEM, configure minimum WiFi security levels that must be fulfilled before a managed device can connect to the said network. This in-turn reduces the chances of vulnerabilities that may occur when devices connect to less secure WiFi networks.
5: Depoy WiFi certificates
Deploy WiFi certificates to managed devices to ensure an added layer of security. Once a certificate is uploaded to Hexnode, you can remotely deploy the certificate to the required endpoints.
6: Configure global HTTP proxy for managed devices
You can route network traffic through a proxy server by configuring global HTTP proxy settings for managed devices. This ensures that any attacker who tries to steal confidential data can access only the proxy address, whereas the actual servers remain anonymous. Hexnode UEM enables organizations to deploy proxy configurations in bulk to the specified endpoints.
7: Disable users from adding, modifying, or resetting Wi-Fi and VPN configurations
Once you’ve configured the required network security settings, you need to ensure that these configurations are not tampered with. Prevent your users from adding, modifying, or resetting network configurations by specifying the same using Hexnode.
8: Disable specific apps from connecting to Wi-Fi
There may exist chances that vulnerabilities may enter your network through suspicious apps installed on your endpoints. More so if your organization does not have a proper app management strategy in place. However, with Hexnode, you can restrict WiFi usage to just the required work apps and avoid said vulnerabilities from entering your network.
9: Monitor and restrict Wi-Fi data usage
Monitor WiFi usage using Hexnode UEM by keeping track of how your users utilize your managed WiFi network and preventing excessive WiFi bills from racking up by restricting data usage after a specified pre-set limit.
10: Set up geofences and restrict devices from connecting to Wi-Fi outside work zones
Geofences are virtual barriers that you can place around geographical locations, enabling you to set up work zones and restrict functionalities on managed endpoints within the zone. By setting up a geofence with Hexnode and configuring dynamic groups, you can prevent managed devices from connecting to a WiFi network when they are outside work zones.
11: Move your router to a physically secure location
Doesn’t seem like much, but if an attacker has physical access to your network hardware, all they have to do is reset the hardware and you’re vulnerable. To be safe, always keep your network hardware in a secure restricted location.
12: Secure endpoints that access your Wi-Fi network
Securing your network hardware and software with the best tools, but leaving your endpoints that connect to the network unmanaged, would be akin to building strong walls but leaving the gate open. It is essential to secure and manage your connected endpoints to prevent any potential vulnerabilities from entering the system.
Employing Hexnode’s Unified Endpoint Management solution enables businesses to manage their entire endpoint management lifecycle from device deployment, to configuration, management, and retirement, all of which can be performed remotely from a centralized console.
WPA3 – The next generation of wireless (WiFi) security protocols
After 14 years of WPA2, Wi-FI Alliance released the latest WiFi security protocol, WPA3 in April 2018.
WPA3 brings in new features to enhance Wi-Fi security, including increased protection from password guessing attempts and individualized encryption for personal and open networks. It also equips enterprise networks to take advantage of higher-grade security protocols.
However, WPA3 won’t run on just any wireless hardware and software. Instead, the new standard requires users to update their hardware to support the new technology.
Hence, as of the time writing this blog, WPA2 still remains the most common wireless (WiFi) security protocol used by enterprise and residential networks alike.