“The authority that you give to somebody to do something for you,
when you cannot do it yourself.”
~ Definition of proxy in Oxford dictionary
Proxy servers embody this concept by covering up your identity while delivering requests on your behalf. Among the tools available to navigate the vast digital landscape, the HTTP proxy stands as an intermediary, providing enhanced privacy and security.
Understanding HTTP and Proxy servers in detail
Before we proceed, let’s delve deeper into the realm of HTTP, HTTPS, and proxy servers to know how their interactions shape our online experiences.
HTTP:
Hypertext Transfer Protocol (HTTP) serves as the foundation for communication on the web, enabling the exchange of data between our devices and the websites we visit. Whenever we access a website, our device uses HTTP to request and receive data from the server hosting that site. It’s the language that enables the seamless transfer of information. However, it’s important to note that HTTP communication is not encrypted. It means the data sent between your device and the web server is not protected from eavesdropping or tampering.
HTTPS:
The issues of HTTP are resolved by Hypertext Transfer Protocol Secure (or HTTPS). It employs encryption protocols, such as SSL (Secure Sockets Layer) or TLS (Transport Layer Security), to establish a secure connection between our device and the server. This encryption ensures that the data exchanged remains confidential and cannot be easily intercepted or modified by malicious actors. Websites that use HTTPS have their URLs starting with “https://” and display a padlock icon in the browser’s address bar.
Proxy servers:
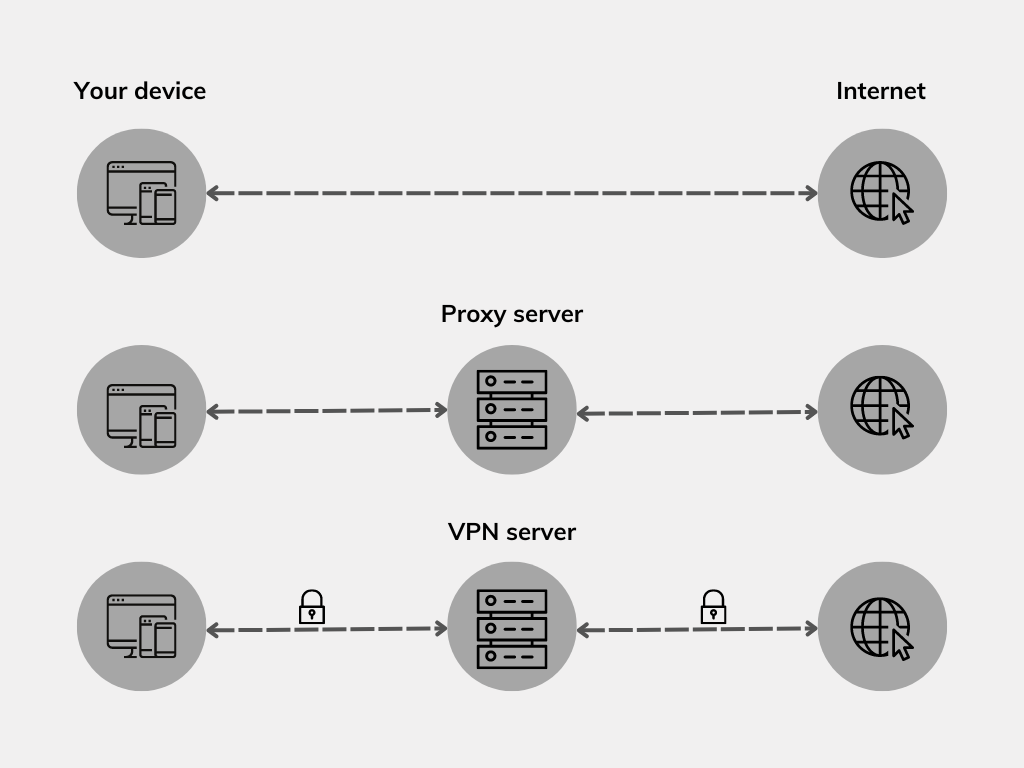
Now, let’s explore how proxy servers fit into the equation. When you make an HTTP or HTTPS request, it first goes to the proxy server instead of directly reaching the intended web server. The proxy server then forwards our request to the destination server on our behalf. Moreover, it acts as an intermediary, facilitating the flow of information and providing an added layer of control and protection. Proxy servers come in various types, each serving specific purposes. Some examples of them are:
-
Forward and reverse proxies:
A forward proxy serves as an intermediary between computers within a private network and the public internet. It accepts connections from subnet users who wish to access resources outside their private network and forwards their requests to the appropriate destinations on the internet. Essentially, it acts as the sole exit point for subnet users seeking access to external resources.
Conversely, a reverse proxy operates in the opposite direction. It serves as a single-entry point for external systems attempting to access resources within a private subnet. By acting as a gateway, the reverse proxy efficiently routes incoming requests from external sources to the appropriate resources within the private subnet, ensuring secure and controlled access.
-
Open and closed proxies:
Open proxies are publicly accessible, allowing anyone to use them as intermediaries. While they offer anonymity, they can also be misused for malicious activities.
Closed proxies, also known as private proxies, are accessible only to a specific group of users or organizations. They provide more control over access and ensure a higher level of security.
It’s important to note that while proxy servers can enhance privacy and security, they may introduce certain risks if not configured or managed properly. Untrusted or malicious proxy servers can potentially intercept and manipulate your data, compromising your privacy and security. Therefore, it’s essential to use trusted and secure proxy servers.
HTTP proxy: Basics and benefits
An HTTP proxy server is designed to handle HTTP traffic. It has a unique understanding of and an ability to manage web-based communication. It operates silently in the background, making our online interactions better.
When you send an HTTP request to access a webpage, it first goes through the proxy server. This process creates a layer of separation between your device and the website, introducing several benefits along the way. Some of its benefits include:
-
Improved privacy and security:
The proxy server hides your IP address, enhancing anonymity and privacy. It shields your identity from websites, making it harder to track online activities. Proxy servers can also filter and block malicious content, providing an added layer of security.
-
Access to blocked content:
By routing your requests through an HTTP proxy server located in a different region or network, you can bypass content restrictions. This allows access to websites and online services that may be blocked or unavailable in your current location.
-
Caching and performance optimization:
HTTP proxy servers can cache frequently accessed web content. When you request a webpage that has been previously visited, the proxy server can provide the cached version, reducing bandwidth usage and improving load times. This caching mechanism enhances overall browsing performance, especially for heavily visited websites.
Common use cases for HTTP proxy
HTTP proxies serve a variety of purposes, catering to both personal and enterprise needs.
1. Web scraping and data gathering:
- Personal use: Individuals may utilize an HTTP proxy for web scraping, extracting data from websites for personal projects or research.
- Enterprise use: Companies may also employ HTTP proxies to gather market intelligence, monitor competitors, or collect data for business analytics.
2. Geo-restriction bypassing:
- Personal use: Internet users may use an HTTP proxy to bypass geo-restrictions, accessing region-specific content such as streaming services or websites.
- Enterprise use: Organizations may require access to geo-restricted content for market research, advertising campaigns, or global operations.
3. Load balancing and traffic management:
- Enterprise use: Organizations can utilize HTTP proxies for load balancing, distributing incoming traffic across multiple servers to optimize performance and ensure high availability of web services.
4. Content filtering and parental controls:
- Personal use: HTTP proxies can be used for content filtering and parental controls, allowing individuals to restrict access to specific websites or block inappropriate content for themselves or their families.
- Enterprise use: Organizations may implement HTTP proxies to enforce content filtering policies, preventing employees from accessing malicious or non-work-related websites during office hours.
5. Security and firewall bypassing:
- Personal use: Individuals may utilize HTTP proxies to bypass firewalls or access blocked websites for personal reasons.
- Enterprise use: Enterprises can deploy HTTP proxies to enhance network security, blocking malicious websites and preventing unauthorized access to sensitive data.
Setting up and configuring an HTTP Proxy
Setting up an HTTP proxy involves a few straightforward steps. Whether you’re configuring it for personal use or within an enterprise environment, here’s a step-by-step guide to get you started:
Step 1: Choose and subscribe to an HTTP proxy server
- Research and select a reliable HTTP proxy server solution that aligns with your needs. This can involve subscribing to a cloud-based or on-premises proxy server service that provides the features and scalability required by your organization.
- Once chosen, proceed to subscribe to the service or deploy the on-premises proxy server infrastructure within your organization. Follow the registration or setup instructions provided by the service or software provider.
Step 2: Configure proxy server settings
- After successfully subscribing to a cloud-based service or deploying an on-premises proxy server, the next step is to tailor its settings to align with your unique needs and preferences.
- Define proxy server access policies, which may also include specifying allowed clients, setting up authentication requirements, and configuring content filtering rules if necessary.
Step 3: Test the proxy server
- Configure a web browser on a client device to utilize the proxy server for web browsing.
- Access various websites to confirm that the proxy server is effectively handling the requests and returning the web content as expected.
Step 4: Additional configuration (Optional)
- Depending on your requirements, you may need to configure additional settings, such as caching options, logging, SSL/TLS encryption, or integration with other network components.
Step 5: Adjust network settings (Enterprise setup)
- In an enterprise environment, configure network settings to route client traffic through the proxy server.
- Modify the proxy settings on client devices or configure network devices (such as routers or firewalls) to redirect traffic to the proxy server.
Step 6: Regular maintenance and monitoring
- Regularly monitor the performance and logs of your HTTP proxy server to ensure smooth operation.
- Keep the proxy server software up to date with the latest security patches and updates.
Remember to consult the documentation or support resources provided by the software or service you choose for more detailed instructions and advanced configuration options.
Identity and Access Management secure the IT environment while monitoring the individual network users who utilize resources such as organizational data, tools, and devices. Take a look at this guide to gain deeper insights into IAM solutions and enhance the security of your devices.

Featured resource
Hexnode Identity and Access Management Solution
Potential drawbacks and limitations of HTTP proxy
While HTTP proxies offer numerous benefits, it’s important to be aware of their potential drawbacks and limitations. Here are some factors to consider:
1. Connection speed and latency issues:
Using an HTTP proxy can introduce additional latency to your internet connection. Since the proxy server acts as an intermediary, it can result in slower response times, especially if the server is located far away from your physical location. The connection speed may also be affected by the overall load on the proxy server and the bandwidth limitations of the network it operates on.
2. Reliability and availability concerns:
The reliability and availability of an HTTP proxy server depends on various factors, such as the server’s hardware, network infrastructure, and maintenance practices. If the proxy server experiences downtime or technical issues, it can disrupt your internet access. Free or public HTTP proxy servers may be less reliable and prone to frequent outages or capacity limitations due to high usage.
3. Incompatibility with certain websites or applications:
Some websites or applications may not function correctly when accessed through an HTTP proxy. This can occur if the website or application relies on specific protocols or requires direct client-server communication without an intermediary. Additionally, websites that employ anti-proxy mechanisms or detection techniques may block access from known proxy server IP addresses.
4. Possible security risks and vulnerabilities:
Public or untrusted HTTP proxy servers may log and track your online activities, compromising your privacy. It is crucial to use trusted proxy servers and be mindful of the data you transmit through them. Proxy servers may also be susceptible to security vulnerabilities, potentially leading to unauthorized access or data breaches. Regular updates and security practices should be implemented to mitigate these risks.
5. Unencrypted Data-in-transit:
Another limitation of HTTP proxies is that the data transmitted between the client and the proxy server is not encrypted. This means that the information passing through the proxy is susceptible to interception and unauthorized access by malicious individuals. If maintaining data privacy and security is a top priority, it is recommended to use an additional layer of encryption, such as a Virtual Private Network (VPN).
It’s essential to evaluate these drawbacks and limitations when considering the use of an HTTP proxy. Depending on your specific needs and circumstances, these factors may or may not significantly impact your experience. Understanding both the benefits and limitations of HTTP proxies will help you make informed decisions and choose the most suitable approach for your online activities.
Wrapping up
Setting up an HTTP proxy offers a range of benefits, including enhanced privacy, security, and performance in web browsing. However, it’s important to be aware of its limitations, such as potential latency issues, reliability concerns, incompatibility with certain websites or applications, and the lack of encryption for data-in-transit.
To address these drawbacks and ensure a higher level of security and privacy, a Virtual Private Network (VPN) emerges as a better alternative to HTTP proxies. Moreover, VPNs encrypt all data-in-transit, providing enhanced confidentiality and protection against interception.
With Unified Endpoint Management (UEM) solutions like Hexnode, administrators can easily deploy both proxy and VPN configurations to client devices in bulk. Hexnode simplifies the process of managing and configuring proxies, ensuring consistent privacy, security, and performance across various platforms. By leveraging Hexnode UEM, administrators can also optimize network performance, identify potential threats, and enforce security policies effortlessly.
Securely manage endpoints with Hexnode
Try Hexnode's 14-day free trial and gain first-hand experience with our device management features.
Try out now