In December 2023, Hexnode performed an unbiased, vendor-agnostic survey with 1000 IT professionals from small and medium-sized enterprises. Respondents, aged 18 and above, represented all levels of management, including top, middle, and front-line roles. The survey included 1,000 participants from 11 different verticals. The goal was to shed light on the existing landscape and difficulties in the sector, as well as to assess their understanding of supply chain security. In this blog post, we’ll give you an early peak at some of our survey’s important results, which will help logistics experts enhance their operations and plans.
Trends in the Supply Chain technology
The evolution towards a digitized supply network has revolutionized the supply chain industry, reshaping the way operations are conducted and managed. This shift has empowered stakeholders to leverage advanced technologies, such as sensors embedded in shipping containers, to achieve real-time monitoring of crucial parameters including location, temperature, and condition of goods. Embracing this Industry 4.0 approach equips organizations with the ability to proactively address potential issues such as delays, spoilage, or theft, thus mitigating risks and preserving the integrity of the supply chain.
Additionally, cloud-based supply chain management systems are a major game-changer. These solutions provide a unified platform for managing operations across several stakeholders. By centralizing data and procedures, they enable seamless communication, collaboration, and coordination across the supply chain ecosystem. This increased connectedness not only promotes efficiency, but also transparency. Stakeholders may make educated decisions based on real-time insights and analytics, improving resource allocation, reducing interruptions, and providing more value to consumers.
However, amidst the rapid digitization of operations, an alarming statistic stands out: 42% of organizations are ill-prepared for cyberattacks, lacking a clearly delineated or effective incident response plan for their supply chain security.
Vulnerability due to 3rd party software
Did you know 52% of organizations have encountered cybersecurity incidents on at least one occasion due to third-party vendors?
Yeah, you read that right. In this industry, third-party software plays a pivotal role in enhancing operational efficiency and scalability. They can be a Supply Chain Planning (SCP) Software, a Warehouse Management System (WMS), or the Transportation Management System (TMS), these third-party vendors provide a range of services tailored to meet specific needs within the supply chain ecosystem. They specialized services and expertise that complement the core functions of logistics companies.
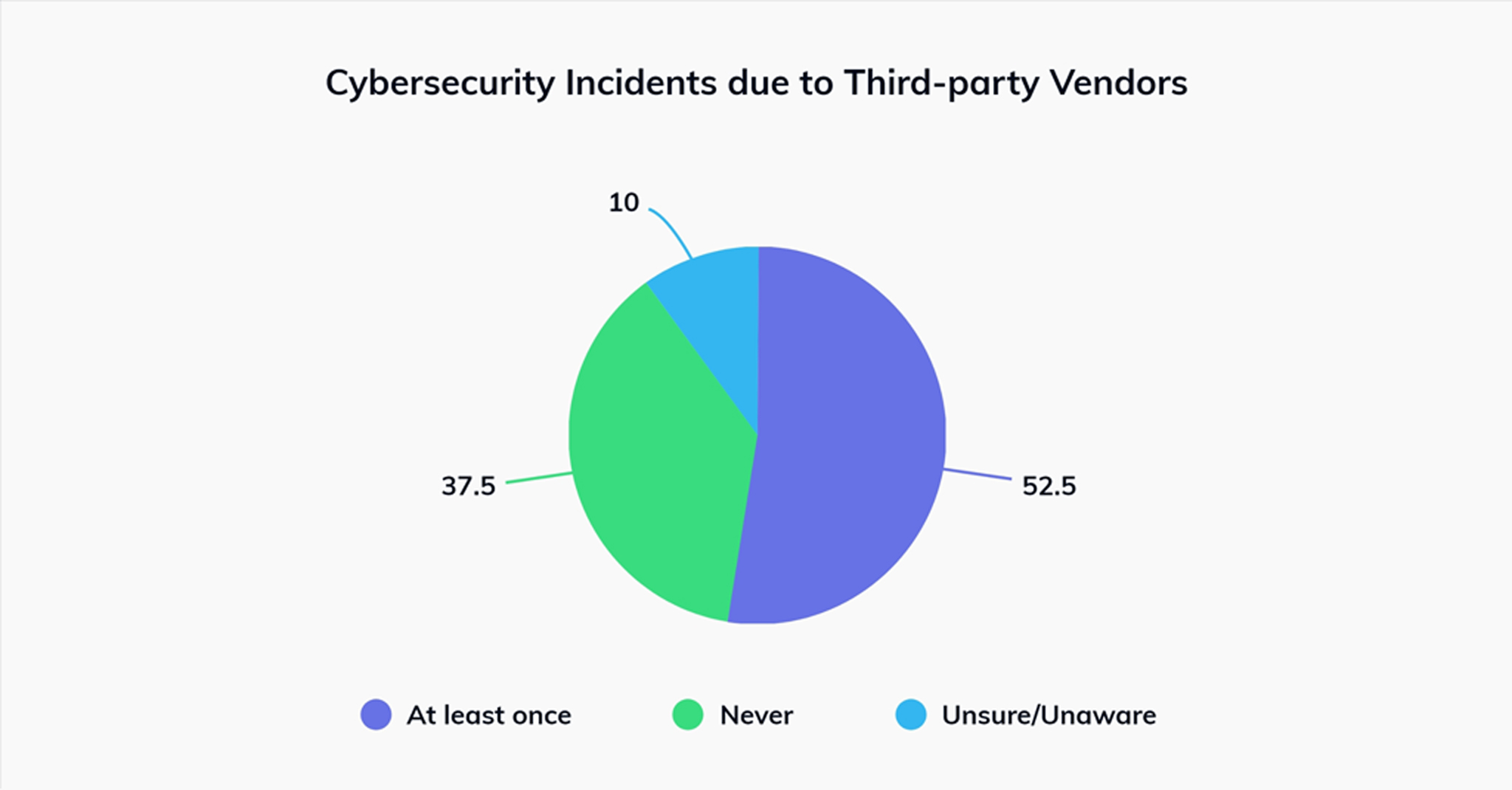
This strategic outsourcing enables organizations to adapt to fluctuating demand, expand into new markets, and navigate complex regulatory landscapes more effectively. However, while third-party partnerships offer numerous benefits, they also introduce risks related to data security, compliance, and reliability. Therefore, it’s essential for firms to manage and regularly update the software to ensure seamless operations.
Third-Party Risk Management programs (TPRM)
Third-Party Risk Management (TPRM) programs are systematic methodologies used by businesses to identify, analyze, manage, and monitor the risks associated with working with third-party vendors, suppliers, contractors, and partners. These programs are designed to protect the organization’s assets, data, reputation, and operations from potential dangers resulting from contacts with other organizations. To our surprise, over 15% of businesses bypass the TPRM process, indirectly exposing themselves to potential organizational threats.
Supply Chain security dynamics and staff sentiments
The research also talks about security dynamics and employee sentiments. Traditionally, supply chain management depended on manual operations, which caused inefficiencies and delays. However, technology integration has transformed operations, greatly improving logistics and inventory management. However, these developments have inherent hazards. In today’s world of sophisticated cyber threats, firms have vulnerabilities that expose them to possible assaults. Recent occurrences show the complex risk environment, which extends beyond typical worries about cyber espionage and critical infrastructure disruption.
Featured resource
UEM for Logistics
As this industry relies heavily on these endpoints for tasks like tracking shipments, managing inventory, and coordinating deliveries, it becomes increasingly vulnerable to cyberattacks. This infographic will help to understand the challenges in the industry and the importance of UEM.
Download the infographicOur report explores critical areas where organizations might be vulnerable. This includes the prevalence of inadequate incident response plans and a concerning level of employee scepticism regarding existing cybersecurity measures. Download the full report to discover the exact scope of these vulnerabilities and gain actionable insights for fortifying your supply chain defences.
Another key finding from our reports showed that 30% employees encounter challenges in receiving adequate IT assistance. When there is so much cyberattacks happening everywhere, getting proper IT assistance is a must.
Supply Chain 2.0
The research also emphasizes the transition to Supply Chain 2.0, which is distinguished by collaboration, data-driven techniques, and customer focus approach. It explores how digital technologies such as IoT, blockchain, and AI provide real-time visibility and cooperation throughout the supply chain. According to the survey, while many firms are adopting IoT devices for tracking, a handful are hesitant to integrate technology. To solve these difficulties, emphasis is placed on cybersecurity measures, personnel training, and risk mitigation tactics. Despite difficulties, Supply Chain 2.0 has the ability to improve logistics operations and create a competitive advantage via strategic strategy and investment. We suggest you to download the report to find some intriguing statistics on the same.
- Tech investments for streamlined supply chain operations.
- Why bridge skill gaps to leverage tech advancements.
- Cybersecurity risks associated with 3rd party vendors.
Improving Supply Chain security on endpoints
Implementing basic recommended practices can help improve supply chain security on endpoints. Establishing clear security policies and processes for device usage and administration is critical. This includes password management standards, data encryption policies, and software upgrades on a regular basis. Furthermore, ensuring that all staff have a proper cybersecurity knowledge and best practices training may help reduce the risk of human error. Stronger physical security measures can also help to prevent unauthorized access and device theft.
Hexnode as a solution
As supply chains get more complicated and scattered, monitoring security across various devices and endpoints may become difficult. This is where Unified Endpoint Management (UEM) solutions like Hexnode come in. Hexnode provides centralized administration and control for a wide range of devices, including smartphones, tablets, laptops, and IoT devices, all from a single platform. It let enterprises implement security rules uniformly across all endpoints with features like location tracking, kiosk lockdown, remote device wiping, compliance monitoring, etc. Furthermore, Hexnode can help with a smooth device provisioning and onboarding procedure, ensuring that all devices fulfill security requirements before being incorporated into the supply chain ecosystem. This helps businesses improve supply chain security while increasing operational efficiency and agility.
Hexnode empowers IT admins with the tools they need to manage the devices, allowing them to effectively identify and respond to security threats. The survey reveals the critical role that IT departments play in identifying and mitigating security breaches, with nearly 70% of breaches being detected by internal teams. This highlights the importance of IT admins having granular control over managed devices.
Lastly…
As we wrap off our analysis of supply chain security through the lens of the Hexnode report, it becomes clear that the situation is both complicated and dynamic. Our research has shown critical aspects, possible dangers, and actionable insights required for navigating the complexities of supply chain management.
This report is an indispensable resource. It provides a road map for increasing operating efficiency, reducing risks, and strengthening supply chain defences against possible vulnerabilities and disruptions. The statistics highlighted, such as the alarming prevalence of poor incident response plans and cybersecurity risks associated with third-party suppliers, emphasize the crucial need of proactive steps in maintaining supply chain integrity.
Looking for a UEM solution?
Try out Hexnode UEM for free to effectively manage your endpoints.
Sign up now





