Restaurants and retail stores can best be described as people’s destinations or people’s hubs. Considering this people-centric nature, industries have begun resorting to practices that their customers best prefer. With changing times, the way payments are made and logged have also undergone major transformations beginning with the initial manual registers to the most recent POS systems, a remarkable journey worth noting.
“When I was young, people lived from paycheck to paycheck. Today, it seems like they live from credit card payment to credit card payment.”
Recollects Robert Kiyosaki, the renowned American author and businessman, on the changing trends in the payment sector.
Nowadays, we often hear the term Point of sale (POS) linked with the payment sector. The term actually refers to the place where the customer pays for the availed services, inclusive of all the taxes. It includes collaborative payment tools and is often seen located at the end of the physical store. These tools can either be a POS terminal with systems or a virtual one with mobile or computer-based payments.
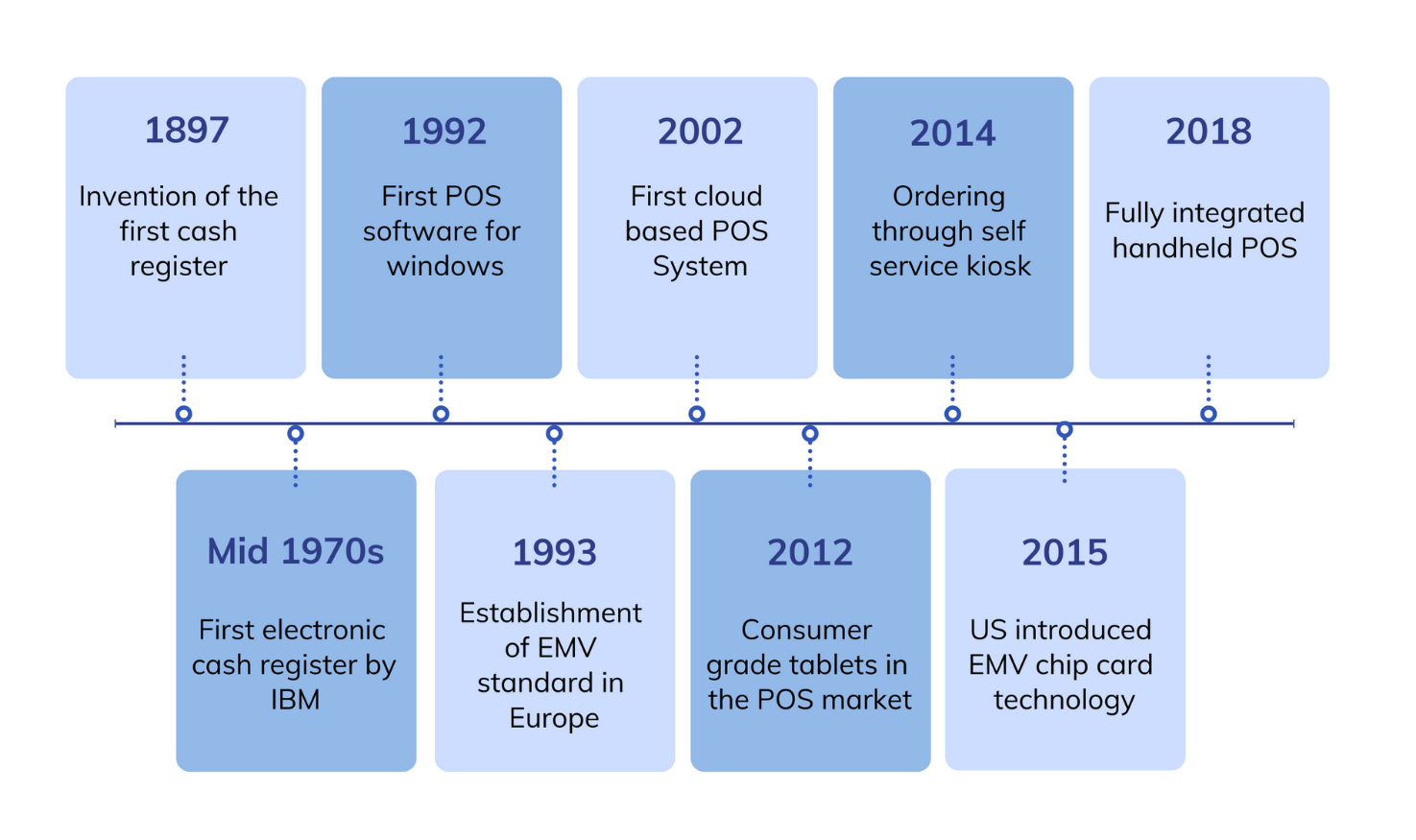
Evolution of POS
POS: Some terminologies

POS System
A POS system collectively refers to all the hardware and software components used for billing in a POS store. It usually consists of all the necessary devices for efficiently managing the sales and the related transactions. Some of the commonly seen components of a POS system are as follows:
- Display unit showing the billing information
- Software interface for completing the transaction process
- Input device like keyboard or touchscreen for product selection and entering data
- Barcode scanner for scanning commodities to be billed
- Printer for printing the receipt
- Cash register for storing the cash received
POS Software
It refers to the software running on the POS system, or in other terms, it comprises the terminal’s operating system. This software interface has simplified the process of inputting data regarding purchasing the various products and getting accurate cumulative data logs of the required products. It further helps in processing orders using the available hardware components.
Different firms may have different data collection requirements, and hence, POS software is often tailored to meet the respective industry’s needs.
POS Terminal
It refers to the payment receiving section of the POS system. Here devices like a card reader or other payment accepting devices are found, which accepts payments for the orders made through the POS system. With integrations with the POS software, bill printing and card swiping can be carried out on a single hardware device. This simplifies the process of order management and makes the checkout process faster. These terminals accept a wide range of payment modes, from chip-based cards to detecting contactless cards and other online payment modes like Google pay, Apple pay etc.
Some benefits of the POS system

Increased efficiency
POS system has eliminated the need for people to remember the price and details of various products in the store. Now all the person needs to do is scan the product’s barcode to fetch the required product data, making the process faster. Further, this system also helps keep track of employees and their checkout speeds and helps in taking appropriate measures to enhance the employees’ efficiency.
Easier analysis and inventory management
With a POS system in place, upon adding the existing stock level upon the system implementation, the inventory level is automatically adjusted by the software with each purchase. Further, it has also made it possible to get accurate sales reports and trend analysis to get a clear picture of your businesses’ status.
Maintaining consistency of the catalog in multiple stores
POS software helps in maintaining a digital catalog of data that can be accessed from any preferred location. This means that once a product price is set in one of the stores, there is no need to enter the same data again in the other stores.
Increase store profitability
Effective inventory management and buying behavior records of customers can help in creating personalized marketing campaigns. This helps increase the store’s profitability. Other practices like instant access and enabling selling and ordering from anywhere can further enhance customer satisfaction and hence profitability.
Why is there a need for management of POS devices?

The greatest recorded data loss due to a POS system breach occurred in 2013, compromising nearly 70 million individuals’ data. This has served as an eye-opener to all the businesses that took POS security lightly. Some of the essential aspects necessitating POS management are as follows:
The data your business collects is your responsibility
Taking precautions before an incident occurs is always better than paying the incident’s cost after its occurrence. Securing the data in these devices can be particularly demanding if left unattended or lost, or stolen. Hence, appropriate measures to prevent such instances are essential if you aim to build a stable customer base.
Downtime and overhead cost have a considerable impact
In industries where time is money, even a minute of POS device downtime can result in a tremendous loss. This has created a need to effectively manage these devices to avoid such incidents. Not just this, when POS devices are used alongside other applications, it can give rise to additional overhead costs making device management a necessity.
Not all your employees need access to all data levels
Even in organizations with the most trusted employees, a minor mishap can put the whole organizational data at risk. Hence, managing the devices and controlling the access levels so that only those employees who need them for their duties have access to them can make things easier and guarantee customer trust.
Staying informed about your device in real-time
The changing technology and widespread internet connectivity have made it possible to remain connected, dissolving all regional barriers. Now managing the device in real-time, getting updated location information, monitoring device health and status, and security and compliance information have become integral components of POS devices. All these data can help ensure the judicious use of these devices.
POS vulnerabilities and their fixes

Malware
POS malware is specially designed to steal payment card data from point-of-sale terminals. One of the most straightforward vulnerabilities hackers can exploit to access the card data is the connection between the POS workstation and the store server. All they need to do is introduce a malicious tool to the location of the terminal.
Once the hacker gains access to the network, the extent of the loss can be far beyond expectations. Some of these include:
- Manipulating the sales values and adding special discounts, thus lowering the price of products as per their discretion
- Increasing the price of products digitally keeping the tagged values unchanged affecting the company’s reputation
- Turning off POS terminals of retailers remotely creating massive loss due to downtime
- Timely patching and upgrading of operating system to eliminate entry points for hackers into the network
- Network segmentation so that the sensitive data is safeguarded away from the reach of the malicious actors
Absence of separate hardware security module for storing the encryption keys
Storing user data in the same place as encryption information can make things easier for hackers. In this case, gaining access to one of these automatically gives you access to the other. For this, a separate hardware security module can be used to store your encryption data. The POS data stored can be easily accessed by attaching the device directly onto the server or computer.
- Using an external hardware security module for storing encryption information away from the device that may be targeted by hackers
Not changing default manufacturers passwords

Enforcing strong password policies that ensure that the manufacturer’s password is scrapped before its use.
No separation of POS Data from the business network
Using the same business network to push updates to your POS data environments and devices can potentially put your data at risk. Here access to your network allows direct access to all your POS data. However, creating small pathways from the business network to the POS data environment can be a complicated task for small businesses. Hence, it’s often seen that they resort to practices like multi-factor authentication (MFA) from the business network to the POS device. Similar is the case with coffee shops and restaurants that provide Wi-Fi to their customers. Separating the POS device network from this public network is vital for ensuring data security.
- Ensuring separation of business network and the sensitive POS data
- Implementing MFA in case the separation of POS data from the network is not possible
Adopting systems running old operating systems
It’s a known fact that Microsoft only extends its support to its modern versions. So, if you are still running an old version of Windows that Microsoft no longer supports, you won’t receive frequent security patches to fix operating system issues. It means, once hackers are lucky enough to find an entry point into the software, your POS data will be compromised.
- Ensuring that the system is running on an operating system backed by Microsoft
- Patching the device at the earliest to ensure a secure system
Using fraudulent devices

- Implementing POS systems of firms having a good reputation
- Gather information about the system from its users to ensure its credibility and functioning
RAM scraping
RAM scraping, also known as memory scraping, is a technology used for extracting sensitive payment card data from the memory of the payment application process. This is implemented in specially crafted malware attacking payment applications by stealing cardholder information from memory.
RAM scraping is a technique used by hackers to rip credit card data directly from the POS device’s memory before it gets encrypted on the network.
- Isolating the POS system from the business network can help reduce these kinds of attacks
- Ensuring the communication of POS systems with known devices alone by tightening your company firewall
MDM for POS device management

- Simplified policy deployment to devices or groups giving the user the flexibility to model the policies as per the organizational needs
- Single or multi-app kiosk modes restricting the device to the essential apps alone to function as self-service kiosk
- Whitelisting the required apps as background apps which can only be accessed when the application locked in kiosk mode invokes them
- Allowing the end-user to access some essential settings on the device while hiding the unnecessary ones with the peripheral settings
- Web app kiosk enabling the device to be locked down to the whitelisted URLs alone.
- Real-time device troubleshooting using remote view and control eliminating chances of downtime due to commuting
- Easy deployment of enterprise apps and application management for simplified device setup
- Pushing secure Wi-Fi networks to prevent intrusions
- Location tracking and geofencing policies to keep track of device and impose location-specific policies
- Enforcing strong passcode policies to check the use of default passwords and for ensuring periodic changes
Some POS best practices
Some of the best practices to prevent a POS system compromise include:
- Utilizing real-time detection and PCI compliance monitoring tools for actively monitoring your POS system for changes
- Installing antivirus software on the POS system
- Adopting best of class end to end encryption around critical data like the cardholder’s information
- Restricting the communication access to the POS system to the necessary hosts alone
- Implementing the more secure chip-card enabled POS terminals
- Creating awareness or training employees to detect and report cases of tampering at the earliest
- Hiring security experts for enhanced data protection
What’s awaiting us?

- Image scanning of the items on a conveyor belt eliminating human errors and the need for double scanning
- Self-checkout or robot-based checkouts for easier shopping
- Replacing tags attached to garments with a biodegradable RFID transponder which gets deactivated on payment completion
- Biometrics like a fingerprint, an eye scan or facial recognition for enhanced store operations and customer experience
- Complete elimination of long checkout lines by the full-fledged implementation of one-click and contactless payments
- Digital product tracking for self-checkout and sending automated digital receipts to the user upon purchases