Did you miss day 2 of @HexCon23?
Don't worry!! We've got you covered. Check out this blog to catch up on all the highlights from Day 2.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

As we bid a fond farewell to HexCon23, the excitement for what’s in store is nothing short of exhilarating. Our distinguished speakers delivered insights on fortifying the safety and security of individuals, devices, and networks in every organization. The three day event had everything from cybersecurity and data protection to the crucial realm of API security. Here’s a quick sneak peek into the thrilling highlights that unfolded on the last day of HexCon 23:
Andrew Wilder, Vice President and Chief Information Security Officer at Hillenbrand, covered 3 main sections in HexCon23:
He grabs the audience’s attention and explains the history of IAM (Identity and Access Management) using easy-to-understand terms. His terminology includes:
In the evolution of Privileged Access Management (PAM) section, Andrew explains about the Wild West, PAM vaults, Password rotation and Machine learning (ML) & Behavioral analytics (BA).
The most recent PAM solution now incorporates Machine Learning (ML) to assess whether an account is being used in an unusual or typical manner. Additionally, the Behavioral Analytics (BA) tool aids in identifying and addressing such irregular activities.
Andrew wishes for a future of Identity and Access Management where it’s a world without PASSWORDS1! Relying solely on passwords is an ineffective approach to safeguarding access to resources.
Merlin Namuth, Chief Information Security Officer, offers a thorough exploration of commonly accepted notions in cybersecurity, providing a comprehensive understanding of these concepts. According to him, HR departments often craft job descriptions that set unrealistic expectations, such as demanding 10 years of experience in a field when the technology itself has existed for only 5 years. This mismatch between expectations and reality is a contributing factor to the shortage of cybersecurity professionals.
The organization’s security awareness training has the potential to mitigate risks effectively. Equipping the organization with the necessary tools and knowledge allows them to safeguard themselves and maintain compliance. According to Merlin, the primary focus of awareness should be on educating employees about
Merlin also underscores that security represents an additional cost for the organization. Security programs are centered around preserving the confidentiality, integrity, and availability of data. Furthermore, ensuring the security of your organization also enhances the stability of its systems and environment.
Sunil David (Digital Technology Consultant, Ex- Regional IOT – Director, AT&T India) starts his section with the key trends to watch out for in 2023.
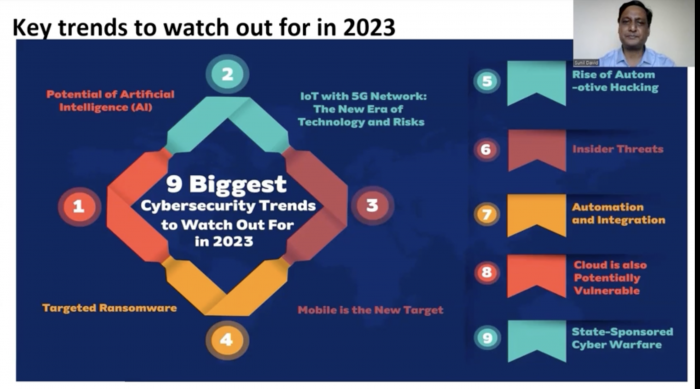
He explains the key features of 5G networks, which include:
Notably, 5G networks are designed with security in mind, which makes them instrumental in propelling the adoption of IoT (Internet of Things). Enterprises can seamlessly connect all their devices to the internet using 5G, due to its exceptional data rates and capacity. Moreover, enterprises can harness the network’s reliability and resilience while prioritizing security.
However, there are also several security concerns associated with 5G networks. The top four among them are:
Sunil wraps up the section by emphasizing the significant role of AI in countering cybersecurity threats during the 5G era. In the present landscape, organizations must shift from merely detecting cyber threats to forecasting them, and AI can play a pivotal role in this transition.
T.J. Preyear, a Security Analyst at ISE, captivated the audience’s interest by commencing with his personal exploration of hacking tools. He also provided an explanation of how hackers utilize these tools, discussed the primary hacking tools commonly found in the modern digital landscape, and highlighted the benefits they bring.
As per his perspective, the key attributes essential to becoming an ethical hacker include:
He also pointed out that hackers consistently strive to discover novel methods for exploiting vulnerabilities in digital systems, driven by their contrarian mindset, dedication to research and curiosity. He wraps up the section by detailing the specific tools that hackers incorporate into their toolkit, which encompass:
T.J. Preyear effectively engaged the audience’s interest by explaining how these tools are employed, providing insight through various scenarios and real-life anecdotes. This demonstrates the idea that numerous factors can potentially pose threats, emphasizing the need for consumers to maintain vigilance. While it is reasonable to place trust in our surroundings, verifying their authenticity is crucial to prevent falling victim to deception.
Art Ocain, Strategic Alliances and Incident Response Product Management at Airiam, initiated the section by outlining the key objectives of cyber resilience: Anticipate, Withstand, Recover, and Adapt. These phases are integral components of the Cyber Resiliency Engineering Framework (CREF), a toolkit designed by MITRE to engineer resilient systems.
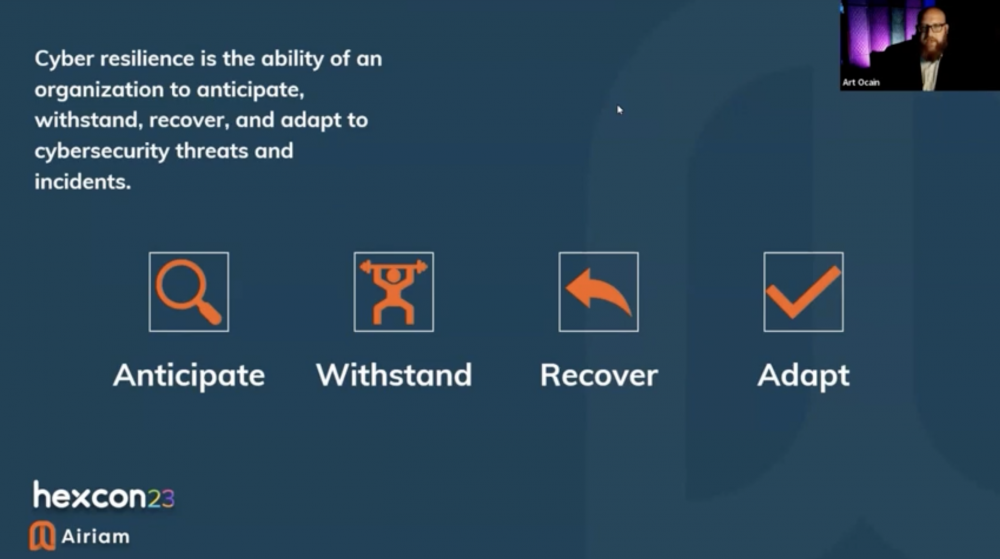
He then delved into strategies for ensuring an organization’s continuous operation during an attack and, in the event of a disruption, how to swiftly recover and regain stability. The primary significance of cyber resilience encompasses:
Ilias Mavropoulos began the session by addressing three key questions:
BYOD entails employees using their personal devices at work to access organizational networks and sensitive data, potentially improving employee retention, comfort, and task efficiency. However, unregulated BYOD can pose significant security risks.

APIs, or Application Programming Interfaces, are sets of rules and protocols that enable different software applications to communicate and interact with each other. Alex Olsen, Security Content Creator at TCM Security, delivered an engaging session on API security risks and strategies to prevent them.
In recent times, APIs have gained significant popularity due to factors such as the separation of frontend and backend, the proliferation of microservices, and opportunities for API monetization. However, alongside these advantages, numerous security risks have emerged, including issues like Broken Object Level Authorization and Server-Side Request Forgery.
For any organization, the hiring team is well aware of the woes of shortlisting candidates to fill a job position. The skill gap is a very real and very present issue. Now, imagine the effect of this skill gap in as competitive an industry as cybersecurity. So, how do you stand out in the heavily crowded cyber hiring market? Gerry Gadoury, Founder and MD of RedBeard Solutions, took to the HexCon23 platform to address this very issue.
The session started off by mentioning the two-pillar approach to team growth:
Andy Ellis, Advisory CISO at Orca Security, provided insights into the two standard methods commonly used to measure the effectiveness of vulnerability management programs. In vulnerability management, organizations typically assess how well they meet their Service Level Agreements (SLAs) for patch management.
He also emphasized the importance of structuring security programs to align with potential adversary tactics. Defenses should be designed to counteract attackers effectively. Creating a security program without considering how adversaries might breach is similar to building a “Cyber Maginot Line.”
Christian Hyatt and Cory Wolff from Risk3Sixty talked about hackers, scams, breaches, and, of course, our future in the digital world. The two speakers kicked off the session with an interesting hook:
More data has been created in the last two years than all of the human history
The session was the perfect blend of nostalgia (they mentioned the old Oregon trail game), stats, and interesting questions. The experts raised and answered four main questions throughout the session.
While a major part of the session was answering these questions, the last portion saw the speakers recommend some tips for better protection of data.
Building and evolving a business is always a continuous challenge. But how can a business ensure its privacy while striving for growth? Sawan Joshi, founder of TriStep.io, explains this in his session at HexCon23.
He also directs the audience’s focus toward the challenges faced by Software as a Service (SAAS) providers within a high-risk supply chain. He states that:
Privacy leader is a business leader

Pratyusha Vemuri, Founder & CEO of Panoplia.io, provided insights into the extensive topic of Identity & Access Management (IAM) and its pivotal role in cybersecurity. She initiated the session by clarifying common IAM-related terms such as identity, authentication, and authorization, highlighting the nuances of each.
Authentication, as Pratyusha explained, is the process of verifying the identity of a user, system, or entity, typically employing usernames, passwords, or other credentials. Authorization, on the other hand, involves determining the actions or resources that an authenticated user can access based on their permissions or privileges.
Pratyusha also addressed the evolving cyberthreat landscape that organizations face today and underscored the importance of adopting a multi-layered approach to safeguarding digital identities. She emphasized that while building a highly secure IT infrastructure is essential, it shouldn’t compromise the user experience.
Additionally, Pratyusha provided expert advice on the challenges that IT administrators should tackle to ensure a seamless IAM experience. Her recommendations included continuous monitoring for unsanctioned apps, session monitoring of high-risk accounts, and regular credential rotation.
Deepa Bradley, a global leader in cybersecurity strategy, reeled in the audience for a refreshing session on the current cyber standing. The session hooked us all in with a catchy question,
Why a career in cyber?
To put it in a nutshell, a career in cybersecurity can be highly rewarding due to its high demand, job security, diverse career paths, continuous learning, competitive salaries, global opportunities, and the opportunity to make a significant impact in safeguarding the digital world. So, if you have an interest in technology, problem-solving, and ethics, cybersecurity may be an excellent career choice for you.
As the curtains fall on Day 3 of HexCon23, we can’t help but marvel at the insights and knowledge that have enriched this event. From cutting-edge cybersecurity trends to practical solutions, today has been a treasure trove of knowledge. To wrap up HexCon23, Apu Pavithran, the Co-founder and CEO of Hexnode, took the stage for the closing keynote. He extended his heartfelt gratitude to all those who joined us from around the globe, making this event truly remarkable.
As we bid adieu to HexCon23, we eagerly await the opportunities, connections, and breakthroughs that future HexCon events will bring. Until then, stay vigilant, stay curious, and stay secure!