HexCon 22 started off with a set of brilliant speakers spanning various industries who have shared important insights into the industry of cybersecurity, endpoint management, compliance, and other crucial aspects of the technological space.
Here’s a quick wrap-up on what happened on Day 1.
- Keynote: The future in focus
- How to reduce the risk of a major cyber incident and how to reduce the effect of one if it happens
- Prepare for the future of work with Unified Endpoint Management
- Securing software supply chain
- Information protection and governance
- Mobile devices and apps are the new endpoint threat
- Confessions of a CIA spy – The art of human hacking
- Hacks That Bypass Multi-Factor Authentication and how to make your MFA solution phishing resistant
- The vital nature of vision and power of mindset
- Why is SaaS the forgotten part of the cloud?
- Cybersecurity Investment Prioritization: Unlocking the leader mindset
- Internet of things security and best practices
- The state of CyberWars, the future of cyberspace
- Misunderstandings draining ROI: What do most people get wrong?
- A beginner’s guide to secure browser or browser isolation 101
- Vulnerabilities: What they are & how to use them?
- Built for business and rugged device management
Keynote: The future in focus
Apu Pavithran, founder and CEO of Hexnode, kicked off HexCon22 by describing the vision of Hexnode. “To make your work routine simple!!” He discussed the need to create a safer cyber environment for yourself and others around you.
Rachana Vijayan, CMO, and Director of Sales, Marketing, and Partnership at Hexnode, emphasized the growth of HexCon, which is still in its infancy. “Grow, Learn, and Evolve” was a crucial lesson, indicated by her for the company’s future orientation.
Rachana also announced the extension of Hexnode Academy, which will allow clients to get certified in industry-specific courses. UEM for kiosk management, UEM for education, UEM for retail, and UEM for healthcare are among the new free courses.
The keynote also included other important announcements from Hexnode COO Bijo Paulose John and CTO Sahad M. They revealed the new updates for Hexnode users, that would be available on the websites by the end of 2022.
The keynote concluded with the announcement that Hexnode Do, our SaaS Ops management product, will be launched soon.
How to reduce the risk of a major cyber incident and how to reduce the effect of one if it happens
Ciaran Martin is the managing director at Palladian capital and holder of several other advisory roles in the private sector of cyber security. He also played a major role in forming the national cyber security division of the UK’s national intelligence agency GCHQ in 2016 and served as its first CEO.
Ciaran talks about,
The fear and doubt around the cyberspace
The pandemic changed the perception of cyberspace as not something utilitarian, but also a place you go to socialize and work. The summer of 2021 was ravaged by cyber-attacks, principally by ransomware, which served as a statement to societies about the importance of these cyberspaces.
How to build up your defenses
The first step would be to follow the basic security requirements like maintaining a management suite, a firewall a VPN, and other mainstream security measures. Besides this, it is important to have organizational awareness, this is where Unified Endpoint Management software helps.
How to prepare your response to an incident
Is it a huge attack? Do we need to inform the state authorities? Have any partner companies been affected?
Ciaran says that these are the kinds of questions that need to be answered beforehand as a preparation measure for any future cyberattack. At the end of the day what organizations care about the most is to get things working again, so it is important to invest in backup and other safety tools that can ensure the corporate can get back to its operations quickly even after an attack.
Think together to solve the cybersecurity problem
Historically in light of any problem, it is the easiest to solve it from its source. It is the same with cybersecurity. The internet has grown far beyond the control and regulations and none of us were prepared for it. Ciran urges us to think differently when we are looking at future developments like IoT. It is important to question what might be the problem and try solving it right from the source.
What inspired you to push for the formation of the National Cyber Security Centre?
He mentions the multiple threats that companies were facing in the UK and as before outsourcing the data and getting solutions was never a long-term viable option. With the help of NCSC, they aimed to help businesses, and schools and advise them on cyber threats and help them in case of an attack.
What are the key factors that organizations should consider when developing a cybersecurity strategy?
The first step is to identify the important assets of the company and find out ways to protect them. The ability to detect normal behavior is fundamental to detecting any cyber-attacks, regardless of an insider or an outsider threat.
Do you think we will have adequate security to stand against cybersecurity threats in the coming 10 years?
There are always attacks that are evolving along with every new digital development but we can see a shift in the approach in the industry. This has trickled down to every industry and since we understand the impacts of cybersecurity in technological development and we are not rushing to do it first but the importance is to do it right.
Prepare for the future of work with Unified Endpoint Management
The UEM market has developed in the past 4-5 years and has had a massive boost during the pandemic when enterprises revisited the idea of investing in modern tech that can help their employees to work from anywhere.
UEM helps maintain device diversity which is well needed for remote and hybrid work. Another driver for the UEM shift is the seamlessness of the whole process. UEM gives enterprises the ability to purchase the devices from the manufacturer, drop ship and automate the entire setup process before deploying them to their employees.
Here are four approaches to UEM that were mentioned in the session:
The factors that make for a good UEM in 2022 are
- Anywhere OS support
- Employee experience management
- Cloud-based modern management
- Endpoint automation
- Security convergence
Moving on, Rachana Vijayan, CMO of Hexnode helps us understand why Hexnode can be seen as the best UEM out there to fill in all your needs.
Why Hexnode?
Hexnode offers a user-centric suite that offers unified policy management. It has advanced support for BYOD, CYOD, COPE, COBO, and fully managed corporate devices. All of this with flexible device onboarding options and competitive pricing.
Hexnode’s capabilities stretch to
- Unified Endpoint Management
- Security Management
- App Management
- Content Management
- Business Containerization
- Kiosk Management
- Expense Management
Expansion
Hexnode is on the road to expansion while forming ISV partnerships with well-known brands like Keeper, Drata , Kaspersky, and Secureframeile at the same time their trusted customer base includes renowned brands like Volvo, McDonalds, and EY just to name a few.

Securing software supply chain
Similar to a logistics Supply Chain, the delivery of the products and services online can also be seen as a Software Supply Chain effort. Speaker Roman Zuckhov starts off by explaining the importance of the Software Supply Chain., He points out that regardless of whether an online product/service is based on open source or a proprietary product they all go through the company’s software supply chain. This puts us at the mercy of the corporate to uphold best security practices.
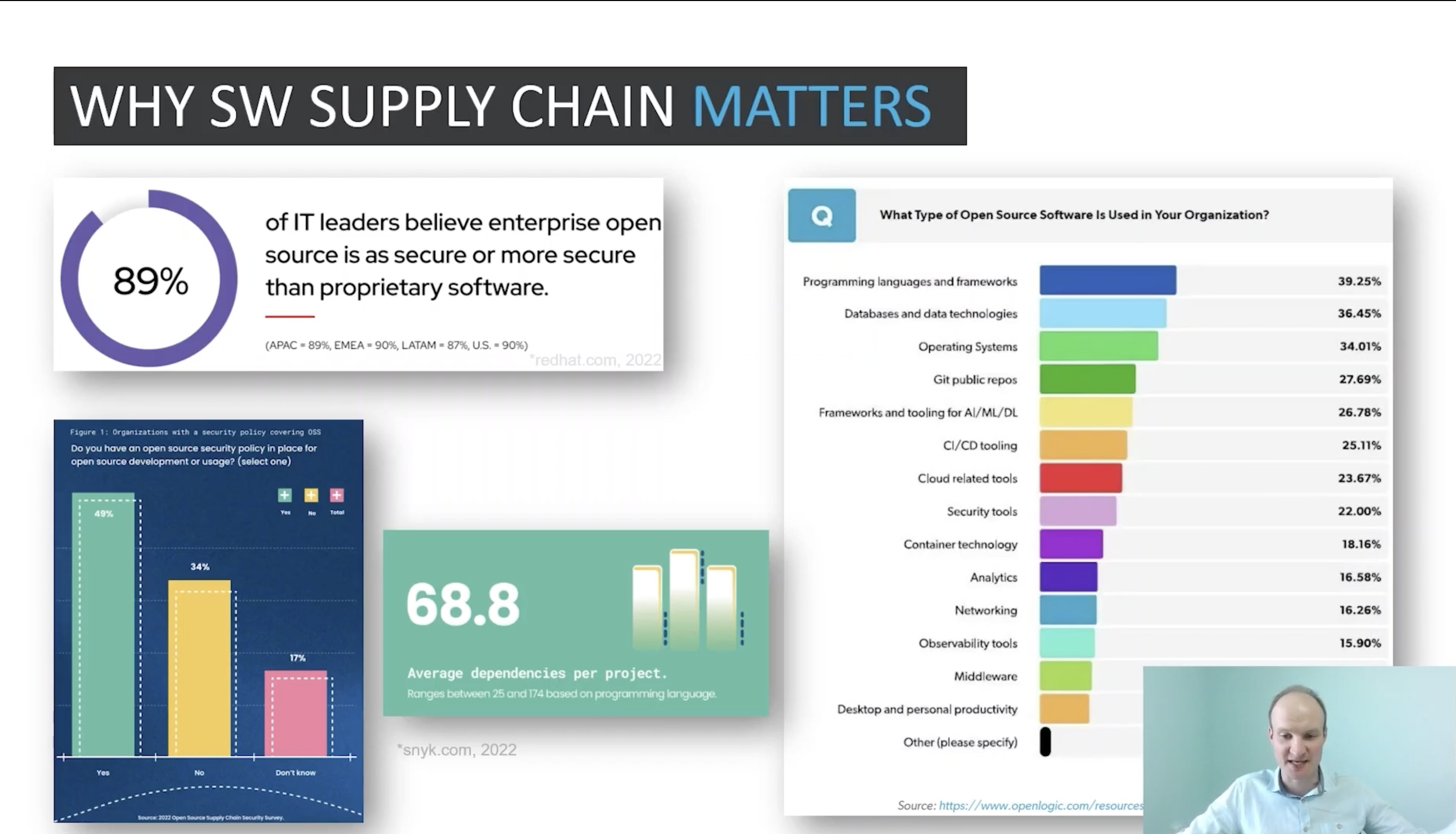
- Implementing responsible product developments, secure engineering, maintenance, and support processes and tools for each software lifecycle milestone
- Follow standards like ISO/IEC 27001, NIST CSF, CIS SSC security guide, DOD DevSecOps framework, etc.
- Leverage one of the SDL maturity models like OWSAP SAMM or BSIMM
- Buy and integrate tons of specific Security products
- Implement SLSA framework
Information protection and governance
Data loss prevention has been a buzzword for a long time in the cybersecurity space, specifically because its importance has only been growing. Dr Abhilasha Rakesh Vyas in her session focused on two key agendas. Information protection and governance and its importance.
Prevent Data Loss and configure Data Loss Prevention policies.
The primary argument for information governance was that “data is exploding” and it is growing both in terms of structured and unstructured data., This calls for a requirement to manage this huge pile of growing data. Many countries are now increasingly adopting data protection laws.
Discovering and managing data is the first problem we face when trying to protect our data and there are four steps to going about the process:
- Knowing your data
- Protecting your data
- Preventing Data Loss
- Governing your data
Mobile devices and apps are the new endpoint threat
In the rapid move towards digitalization, Philip Ingram’s session introduces viewers to the threat through endpoints. The session starts off by talking about the footprint that apps and devices have across the globe.

Mobile devices are growing in numbers due to various benefits like data costs getting cheaper, their handiness, and a massive boost in computing power. This, in turn, increases the threat landscape. It is pointed out that 95% of mobile devices carry no security. Talking about apps and connections, it is important to be wary of the permissions that the apps ask for.
Phillip justifies this statement by asking, “when you use a free app, have you ever thought about why it is free?”
He says “That it is because you are the product”
Data introduces new threats like Disinformation, misinformation, deception, and fake news. When information holds this high degree of power, it is a given that there are going to be businesses that are going to fight for it. On the other hand, when an attack happens on your digital assets, it is only a matter of time before everyone knows. This can lead to a wave of bad news that can hit your reputation beyond recovery.
Finally, he emphasizes the importance of intrusion prevention and malware detection for mobile devices along with local device detection.
Confessions of a CIA spy – The art of human hacking
Peter Warmka kicks off by telling us about the time he worked with the CIA as a human collector for 20 years. This included work that required him to collect information on human sensitive data, where it can be obtained, who holds power to what data. These were all important questions that his job answered.
Threat actors who gain access to this sensitive data can be of four types
Threat actors
Criminal group, intelligence services, Industrial competitors, an activist group and lone wolf.
Objective driven
Businesses can make use of customer data, and employee data. Other reasons like damage to reputation by sabotaging the systems is also one type of objective-driven threat
Insider
These insider threats can be anyone from your employees, and contractors to associated businesses. This is a tough one because there are definitive ways to prevent external threats with placeholders at every point and insider threat is more often than not unpredictable.
Social Engineering techniques
Social Engineering constitutes a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information. There are a few such mentioned like,
- Phishing
- Smishing
- Vishing
- Face to Face manipulation
He mentions in his session the importance of social awareness in threat detection and counteraction.
Hacks That Bypass Multi-Factor Authentication and how to make your MFA solution phishing resistant
Multi-Factor Authentication tools have been thought of as the best solution to combat entry-level threats. Here, Roger Grimes explains to us that even MFA can also be bypassed. The important thing to consider is that some MFA solutions work better than others.
The session dived into the topics about:
- Characteristics that make MFA easily hackable
- The recommendations by the USA government for an effective MFA
- Features that you should look for in a strong MFA solution
- Phish-resistant MFA you should be using
- Why a strong human firewall is your best, last line of defense.
The vital nature of vision and power of mindset
In the space of sessions on cybersecurity, business mobility and the digital age, Danny Bader’s session on ‘The vital nature of vision and a positive mindset’ was a breath of fresh air. His eye-opening narrative on life and mindset started off with the topic of growth and how curiosity plays a vital role in it. Danny shared a life-altering incident in his life and the struggles he endured to jump back right in. Amidst all the chaos, acknowledging one’s own values helps s define our purpose, and as a result, the ability to build a life around it. Quoting famous personalities and their zeal through inspiring anecdotes, Danny Bader emphasized stillness, self-belief, and imagination; all contained in an acronym- H.U.T- Hold Useful Thoughts. The highlight of the session was when he read out a wholesome letter to himself his own self, which was vital for him to shape his vision for the future.
Why is SaaS the forgotten part of the cloud?
Where is your data going? Jerich Beason, CISO of Capital One, got the session rolling with this interesting question. All our sensitive data is present in SaaS and no firewall can protect the SaaS environment from attackers. Hence, SaaS security is a growing concern.
He concluded by sharing the Top 4 SaaS Security risks which are:
- Inventory and discovery
- Access controls
- Incident readiness
- Misconfiguration
Under each of these points, Jerich focused on bringing up questions that made the listeners think about the security that they rely on. He also emphasized that SaaS security should be at the top of the organization’s priority list for the long-term run.
Cybersecurity Investment Prioritization: Unlocking the leader mindset
Marcos Semola, Cybersecurity Partner at E&Y talked about rapidly growing cybersecurity threats and how we could work to unlock the leadership mindset to prioritize investment in cybersecurity properly.
Only 36% of new company initiatives include cybersecurity teams in the planning stage. Furthermore, 7% of the cases do not involve a cybersecurity team at all. This makes him believe that the leaders are not able to see the risk and take the right decision in the long run. He explained the gap between the necessary level of information security and the current level of information security. He also discussed the NIST cybersecurity framework and its components.
Internet of things security and best practices
More organizations realize that fighting cybercrime is not core competency. Sunil David, Advisor and Consultant to IOT and AI Startups, agrees with this statement in his session. When it comes to cyber security, firms have no choice other than to invest in the appropriate tools and technology. He explained the end-to-end security for IOT as a multi layered approach which is layered with Endpoint-Connectivity-Data/Application.
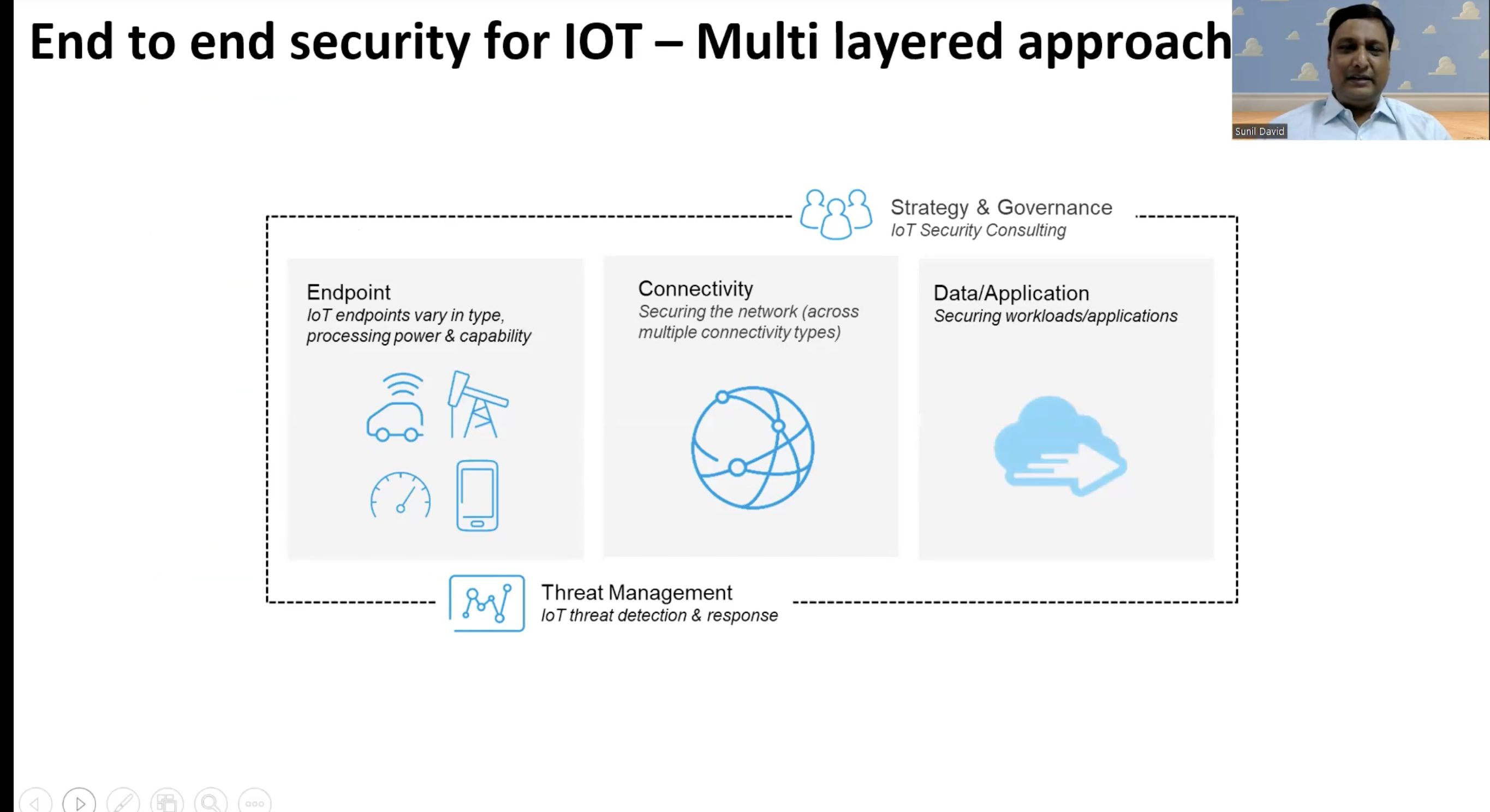
Sunil concludes the session by stating that “Security is a business problem, not a technology problem”.
The state of CyberWars, the future of cyberspace
Nick Shevelyov, Strategic Advisor at Glynn 100, talked about the overall enterprise risk management that he came across in the 25 years where he has been working and ties them with lessons from history.
He said that the more we invest in technology upfront, the more effective will be security risk management. He believes in the discipline of constantly checking on your controls to see if they are performing as well as you thought. He encouraged everyone to think through and undergo continuous verification rather than trust.
Nick said that multiple privacy laws are coming up and it must be treated as a human right. In this session, he referred to the war of Troy and compared it to the third-party applications that launch stealth malware attacks.
Misunderstandings draining ROI: What do most people get wrong?
It’s not unusual in the corporate world to see employers frustrated by missed deadlines or employees facing burnout due to understaffed teams. The session taken by Best-selling author Dr. Shayanna Mungo explained every aspect with her personal experience and observation, which was more appealing!
She explains that the inability to organize the tasks results in the overallocation of duties. It will thereby reduce the focus of employees and the quality of work they do. She names this overallocation as “Spider Overallocated”.
Dr. Shayanna makes the weeds analogy to the enterprise, where she provides a different abbreviation for that. WEEDS are explained as “Wish Everyone Else Does Something”. As weeds are a threat to crops, so for the enterprise! They put the individuals at risk, as they interfere with:
- Mindset
- Attitude
- Tolerance
- Perseverance
- Ability and
- Capability
She concluded the session by warning about the common current team experience existing in the enterprises. If they hesitate to nurture their employees, the entire enterprise can fall!
A beginner’s guide to secure browser or browser isolation 101

Evgeniy Kharam, the Co-founder of the Security Architecture Podcast and VP of Solution Architecture “Herjavec Group” delivered an engaging session on browser security and isolation. Do you know that there is always a chance that your information will be stolen by a remote attacker when you browse the internet? Evgeniy started the session with this normal example of how a user accesses the browser. Thus, the need for browser security for a user.
As a solution to this problem, he explained the importance of remote browser isolation (RBI). It is an online security solution meant to protect users from Internet-borne risks. It is also known as web isolation or browser isolation.
The user can elevate the browsing experience using browser security extensions. These extensions will help the user to analyze whether the websites are phished or malicious. Evgeniy also mentioned the different vendors who offered RBI, browser extension and secure browser and local isolation. The session ended by discussing the risks and concerns under this domain which covered latency, traffic routing optimization, vendor considerations and many more.
Vulnerabilities: What they are & how to use them?
Why should we ignore vulnerabilities and how should we manage them? This was the key focus of the session delivered by Chuck Davis, vCISO of Caveat Labs.
In the 1990’s it was difficult to figure out which patches to install and the compatibility of the systems to be installed. Then, the Mitre corporation came up with the common vulnerabilities and exposures (CVE) database which made life a lot easier. It identified each vulnerability with unique names. NIST put together the national vulnerability database (NVD) that kept a record of the severity of the vulnerabilities by using a common vulnerability scoring system (CVSS).
Chuck also talked about how the need for VPNs shot up in early 2020. From providing enterprise VPN to 10% of the workforce, companies had to provide it to 100% of the workforce once the pandemic began. He describes that although patches are a solution, they have their own sets of challenges. It might need companies to hire external resources and provide them with admin access to their systems. He also clearly explains the CVSS score calculator and its components.
In the session, Chuck also showed a threat matrix based on impact and probability. The whole purpose is to prioritize the vulnerabilities and know the severity score. He concludes by saying the fact that in the cybersecurity industry, success is invisible and failures are in the headlines.
Built for business and rugged device management
The topic of rugged devices grabs one of the top spots when it comes to business mobility. As highlighted by Robin Hammond and Tim Shepherd from the Bullitt Group, they emphasized on the need of rugged devices and their rapid growth in recent years. About 86% of business phone buyers deal with significant damage and an added expense on repairing their devices. Moreover, the shift in working patterns due to the pandemic contributed to the ever-expanding need for rugged devices.
The manufacturers of Cat® phones have bestowed upon us with their participation as well as being a Gold Sponsor for Hexcon’22. We are also thankful to Keeper for joining the wall of Gold sponsors. Their virtual booths definitely provide a lot to explore at Hexcon’22.