Missed out the Day1 @ HexCon21?
We’ve got you covered with this quick recap blog.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

The past two days of Hexnode’s annual user conference, HexCon21 have been a whirl wind of excitement. As the Day 2 of HexCon21 comes to a close, here we’re outlining the key takeaways from Day 2 for any of you to catch up on the sessions you’ve missed.
Day 2 officially kicked off with the opening keynote from Matthew Rosenquist, the CISO and cybersecurity evangelist at eclipz.io. Possessing experience of over 30 years in the industry, he talked about the interdependence between digital technology and security. He drove home the fact that every new technology comes with associated risks and that trust is crucial for the continued innovation of technology.
Here are the critical points of interest that Matthew Rosenquist discussed in his talk.
Here are some significant cybersecurity best practices that Matthew Rosenquist proposed during his talk, for distinct divisions of individuals.
Abbas Kudrati, APAC Chief Cybersecurity Advisor at Microsoft, discusses how Unified Endpoint Management solutions can play a role in your Zero Trust network architecture.
The 3 key principles he talks about as being part of zero-trust are,
Moving on, Abbas Kudrati talks about how Unified Endpoint Management solutions can reinforce that Zero Trust network architecture.
He also specified five unique use cases or scenarios where a Unified Endpoint Management solution can play an important role in Zero Trust network architecture.
Ulf Mattsson, the chief security strategist at Protegrity, spoke at HexCon21 about the security and privacy trends in the cloud at financial institutions. He elaborated how, as more people started to work from home due to the pandemic, data became much wider and less controlled, ultimately resulting in a distributed corporate environment.
He talked about the different data regulation policies including EU GDPR, US CCPA/CPRA, PCI DSS, US HIPAA, and the kind of data that are considered sensitive.
Moving on, he talked about the factors impacting security information in coming years, including,
Ulf Mattsson also talked about the different data protection techniques used in financial institutions, including 1 and 2-way transformations, hashing, data masking, differential privacy, k-anonymity, and more.
He talked about the different use cases and data privacy techniques, and their requirements in the financial sector. He also discussed risk management, including the pyramid of risk, and how to utilize IT for competitive advantage.
Ulf Mattsson predicts that CASB and encryption will be the top trends where end-users will make future security investments, and shows how CASB can protect sensitive data both in the cloud and on-premise.
John Grim explains how the VERIS Framework underpins the Data Breach Investigations Report (DBIR). VERIS employs the A4 Threat Model to describe key aspects of incidents and breaches that affect victim organizations.
He then talks about the key highlights from the 2021 Data Breach Investigation Report (DBIR), and how it was developed using the VERIS A4 threat model.
DBIR 2021 offers an in-depth look into data breaches and cybersecurity incidents. It takes data from 88 countries and 83 contributors. It has taken into account 79,635 total incidents, and have considered 5258 data breaches.
John Grim then moves on to explain the VERIS framework (Vocabulary for event recording and incident sharing), which consists of four fundamental elements.
He then goes on to explain each of these fundamental elements in detail.
John Grim ends the session by talking about the many different use cases for the VERIS framework and provides relevant information for the same.
Scott Augenbaum, retired FBI special agent talks about tackling cybercrime in the industry. The global damages of cybercrime keep on increasing – says Scott.
There are around 294 million smartphone users, 32 million businesses, and 56.6 million students attending elementary and secondary school in the US. The FBI’s Intercrime compliant center states that cybercrime has increased 400% since the pandemic. The global cost of cybercrime increased 100% in the past 5 years, and currently sits between 1 trillion to 6 trillion dollars, and the worldwide spending on information security is forecasted to reach 170.4 billion by 2022.
Scott has spoken to over a thousand victims whose attacks could easily have been prevented in his time.
He talks about the four truths behind cybersecurity
He then goes on to share the common mistakes that happened in each of their victimizations
Scott ends the session by talking about a few steps and strategies you could adopt to stay safe online.
Curtis Wick from Kyocera International talks about the benefits of Rugged devices for the 5G evolution.
Businesses face a lot of challenges when mobile communication is concerned. With Kyocera OEMConfig, EMM solutions can include specific Kyocera APIs for configuration and implementation. Curtis discusses the rugged capabilities of Kyocera devices, which includes,
He goes on to talk about the benefits that 5G evolution promises, including,
Curtis also talks about the market focus for rugged 5G devices, which has expanded to,
Chris Roberts, one of the world’s foremost experts on Counter Threat Intelligence and vulnerability research within the Information Security industry, joins us on an interview with Sarika Abraham, Marketing lead at Hexnode, to discuss some of the most common vendor questions on cybersecurity in the enterprise, and how we can keep ourselves secure in the age of online business. He talked about his background in the security industry. As one of the well-known hackers and researchers, Chris has been deeply involved with security R&D, consulting, and VCISO services, in his quest to protect and defend organizations against various types of attacks. He answers questions about,
Chris also shares his views on modern technology including,
And just so much more answers to all our burning questions.
Albert E. Whale, founder and CEO of IT Cybersecurity solutions, talks about the possibility of vulnerabilities affecting the system due to the omission of user behavior and their factors from corporate security strategies.
Albert says that most security strategies are always focused on the network, in a static state. As a result, assessment and testing are completed on devices, without considering the human factors. Hence, these tests become inaccurate.
He says the 3 pillars of cybersecurity are,
Albert also shares his experiences from his company on how users can affect the security network. He says that vulnerabilities from user behavior can be classified into three.
Michael Manrod, Chief Information Security Officer (CISO), and Christian Taillon, Threat Response engineer at Grand Canyon Education, discuss revisiting the security fundamentals required to mount an effective defense against ransomware and other common threats of this era.
They talk about the emerging trends and happenings in the cybersecurity industry including,
They also talk about a few threats to expect these days, most notably Malware-as-a-Service loaders such as Night Spider’s Zloader, or Wizard Spider’s Bazar loader.
Moving on, they talk about some of the few common problems they have identified when reviewing security strategies, including
Lastly, they finish by talking about the current trends and solutions being used by businesses to protect hosts and enforce security. These include,
Donald Allen, the #1 bestselling author at dacybersecurity.com, talks about the role of passwords in cybersecurity and about different methods to protect against threats.
Donald Allen begins his talk by mentioning the human element in cybersecurity. He quotes that, 85% of all successful cyberattacks involve the human element. He further quotes from Verizon’s 2021 DBIR, stating that,
Next, Donald moves on to talk about the different ways how cybercriminals can steal your password.
He further goes on to share some of his experiences and stories in the cybersecurity and threats domain. Donald then talks about the steps that you, as an individual, can take to prevent potential threats and attacks.
Lastly, Donald concluded his discussion by summarizing the key points from his talk as follows.

When it comes to cybersecurity, Sami Laiho (Microsoft MVP), Senior Technical Fellow at Adminize, talks about how it is always better to be proactive than reactive. He talks about the different tactics you can implement to convert to a proactive strategy.
Sami begins with Directory Tiering – The process of splitting your environment into 3 layers, and never allowing higher admin layers to access lower admin layers. He demonstrates how to do this in a standard windows domain environment, with the help of a domain controller and a client system.
Next, Sami talks about MFA – A very effective protection against phishing attacks. He goes on to explain that using biometrics as a second factor can be very powerful, and then demonstrates how to implement 2FA in a domain environment with a third-party app (DUO).
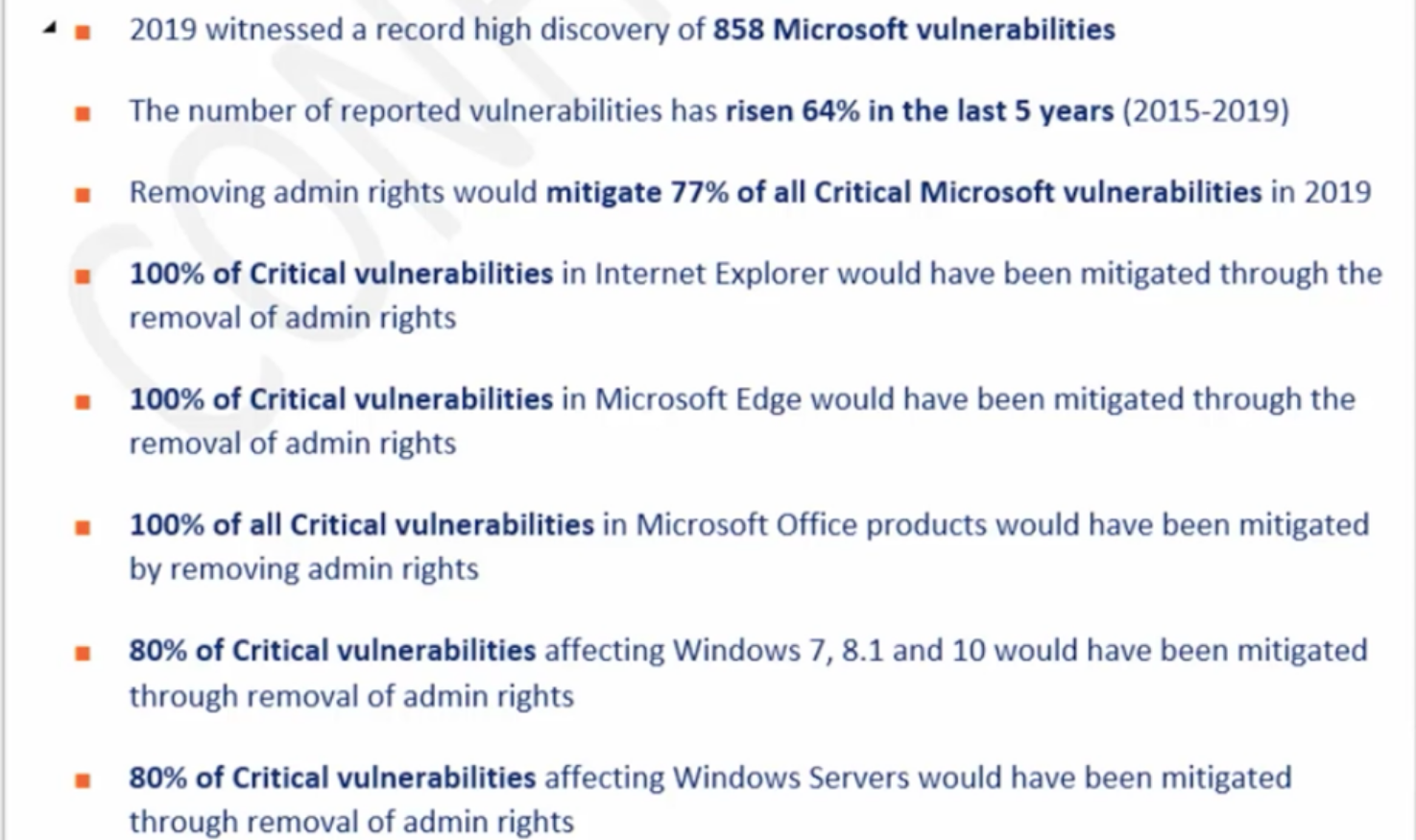
Next on the list, he talks about the principle of least privilege – He says, in Windows, if you let users log on as an admin, then there is no security. Windows did not build the security subsystem to withstand the use of admin rights. However, with a no-admin approach, we get
Sami goes on to show relevant news and reports on attacks and vulnerabilities that occurred when users were given admin rights,
Next, he talks about Allow Listing – Sami says that by allowing listing/whitelisting applications, we can easily block most malware from entering our Windows environment. He then goes on to show a demo by setting up an allow list on his personal machine.
Sami also talks about why we need encryption
Last on the list is the need for Monitoring – Someone needs to keep monitoring what’s happening in the environment. Be it using CM solution, Microsoft Azure Sentinel, Splunk or other monitoring solutions and software.
Madhu Maganti, a prominent Cybersecurity Leader and Trusted Advisor (ABIP CPAs & advisors), talks about building a strong security culture in the workplace.
Madhu begins by talking about the difference between positive and negative work cultures

Madhu then talks about how to improve your cybersecurity culture, by following certain steps
He also provides us with good tips and instructions on setting up an effective security culture in the workplace.
Dr. Lanre Philips, a proven expert in the FMCG, banking, telecommunications, and information technology industry, delivered his thoughts on businesses creating opportunities in a world of limitations. He shared stories of being a resident of Nigeria and how change is constant in everyone’s life. He opened our eyes to the fact that we wake up each day with expectations and spend the day trying to bring it as close to reality as possible.
Dr. Lanre highlighted the seven steps involved with change: immobilization, denial, anger, bagging, depression, experiencing, and acceptance. The rate at which people move through these steps is different for each individual. The faster you get from immobilization to acceptance, the quicker you can adapt to changes.
Dr. Lanre Phillips left us with a series of thought-provoking examples to show why your environment, your business, and your knowledge of your customers will help make you a better entrepreneur.
“Change is constant, the best we can do is try and repackage ourselves”
Some of the most challenging areas of growing a company can be connected to the lack of leadership and cultural management. Josh Allan Dykstra, CEO of Helios, delivered an engaging talk on how businesses can remotely build a great work culture. He used the metaphor of the importance of an operating system to a device to signify the role of work culture in a company.
Work culture, just like the device OS, dictates what can and cannot happen at your business. Unfortunately, when founders build a business, they unknowingly create an OS that is codified later into what is commonly regarded as the work culture. Josh delivered ideas on how these issues can be circumvented by employing a 3-step process.
Step 1 – Making the OS visible
Making the work culture an opt-in program considering that the entire workforce cannot adapt to rules, but they can look forward to aims and aspirations.
Step 2 – Make it tangible
Focus on the principle the company needs; borrowing ideas from a company that made their public is a good place to start.
Step 3 – Practice the OS
Your company OS should be used patched and tweaked to accommodate for nuances of your business.
Julie Alleyn, Founder of Pegaus Evolution, helps organizations create a great working culture and stimulate employee engagement. She talks about how managers can help employees return to work successfully as she looks at the last 18 months. She goes on to address the apprehension from employees in preparation for returning to work.
Julie talks about how the work atmosphere changed during the pandemic. She addresses how organizations were skeptical about allowing employees to work from home and how it was proved wrong. Longer work hours during the pandemic proved challenging to the employees, especially since they failed to find a balance between work and personal life. The overdose of bad news on the media also contributed significantly to the apprehension.
She then talks about what employees can do to ease the transition – how employees can recognize the signs of stress and how they can find ways to cope. She talks about the different activities that employees can do to feel more relaxed.
She also talks about how managers can further help employees in returning to the office as she lists out different activities that they can do for employee well-being. Julie finally talks about how all of these can be implemented in the current scenario and what should be avoided while doing so.
Randy Marchany, Chief Information Security Officer (CISO) at Virginia Tech, addresses the difficulties of implementing work from home scenarios in the enterprise. There are five steps to a successful work from home environment, says Randy.
If you use your home computer for work purposes, you must follow your office’s security requirements, and create a separate user ID for work-related necessities.
As an enterprise IT admin who must secure a work-from-home environment, there exist some questions you must find answers to before allowing employees to work from home.
Randy ends his session by laying out specific steps you must follow to protect your computer in a work from home scenario
It’s been 2 years and the COVID-19 still continues to wreak havoc across the globe and it seems like it’s here for the long haul. And among all of its dreadful impacts, the alarming rate of cyberattacks is often the most overlooked one. It’s only after when Dr. Dave Schippers shared his thoughts on this that many of us realized why businesses of all sizes are equally vulnerable to cyber attacks amidst the global pandemic.
Dr. Dave Schippers, Chair of Information Technology Decision Sciences at Walsh College, being a cyber security professional gave some valuable insights on the impacts of COVID-19 on cyber security through his session along with some good tips to tie over the challenges. He started the session by explaining some of the important cyber security industrial terms like cyber kill chain, zero-trust security model, response plans, etc. Following this came the most awaited part: the lessons learned from the cyber security incidents in 2020.
Dr. Dave says that the attackers exploited the public’s interest in staying alert of the pandemic status to carry out targeted phishing and this led to a substantial increase in the number of incidents the world over. He talked about all the attack vectors the criminals are using and the ways by which the pandemic turned out to be the right time for them to implement them. Most of the statements were backed by statistical data and this made the presentation further interesting for the cyber security enthusiasts.
Rafay Baloch, Lead Security Researcher at Cyber Citadel, talks about his research on browser security and walks us through the different ways how one can bypass anti-phishing detection mechanisms.
Rafay begins his talk by specifying the need for mobile browsers. As of 2020, 63.4% of the global mobile population is accessing the internet through their smartphones. However, a study by IBM revealed that users are three times more likely to fall prey to phishing attacks on a mobile phone as opposed to a desktop computer.
Next, Rafay talks about how browsers work, explaining the roles of the user interface, browser engine, and rendering engine. He then talks about the same-origin policy and how it blocks potential attacks to retrieve data from your websites. Rafay then moves on to talk about spoofing attacks and their different categories and classifications
He then talks about each of these attacks in detail, along with how to recognize and counter them. Rafay also talks about anti-phishing filters and how attackers bypass anti-phishing filters to fool the recognition systems.
Mario Demarillas, the Board of Director, Chief Information Security Officer (CISO), and IT Counseling and Software Engineering head at Exceture.inc, talks about some of the prominent ransomware attacks in 2021.
Mario says the top three ransomware attack vectors were due to
He then talks about the cyber security tactic and techniques that can be used by security heads to protect companies from potential ransomware attacks.
In addition to the breakout sessions, there were product training sessions on Apple user enrollment, ROM enrollment, IoT management, Hexnode Okta integration, Scripting, Windows Defender, Mac security management and the whole new UEM migration tool.
Short bursts of gamification added a bit of fun to the day. The Selfie contest required the attendees to take a snap and share their HexCon moment on the wall as well as on social media along with the hashtags #Hexnode and #HexCon21.

Wrapping it up, all the insightful sessions, fun-filled games and interactions with the great minds in the industry made day 2 of HexCon21 pretty exciting just as day 1.
Stay tuned for the Day 3 recap and more blogs on HexCon21!