What a day! Day 2 at HexCon 2020 was as exciting and informative as Day 1, if not more. Complete with training sessions, breakout sessions, networking opportunities, fun games and a Meet with CEO session, we saw an impressive turnout making Day 2 an unmitigated success.
As we see the end of the first ever Hexnode User Conference, HexCon20, here’s what happened today:
- Breakout Sessions
- 1. Leveraging Microsoft Cloud platform: Azure
- 2. A look at unconventional uses of Hexnode
- 3. Make the best out of your Kyocera devices with Hexnode
- 4. Selecting the best out of Hexnode and Samsung
- Hexperience of Sana’ Al-Sharaideh
- 5. A brief look at Desktop Virtualization
- 6. Endpoint security risks no one is talking about in 2020
- 7. SaaSOps: A new way to automate management tasks and protect data
- 8. How to dramatically reduce your Enterprise Mobile Expenses
- 9. Endpoint security: Best practices
- 10. Are VPNs really secure?
Breakout Sessions
1. Leveraging Microsoft Cloud platform: Azure

Steef-Jan Wiggers, Azure Technology Consultant and Microsoft Azure MVP, educated us on what Microsoft Azure is, and how to leverage the Microsoft Cloud Platform for your business. Various benefits of cloud such as flexibility in capacity, lower cost, availability, reduced carbon footprint and easy management were discussed. Steef-Jan also threw light on the different Azure services such as security, networking, storage, IoT, databases and more. Azure IoT technologies, services and solutions have been implemented across different industries and organizations like retail, healthcare, energy and government. The use of Microsoft Cloud Platform Azure was demonstrated through three different use cases: IoT Use Case, Hybrid Use Case and Security Use Case in detail.
The session also discussed on how the organizations can get started with Azure. The five pillars of Microsoft Azure Framework identified are:
- Cost Optimization
- Operational Excellence
- Performance Efficiency
- Reliability
- Security
2. A look at unconventional uses of Hexnode

In a brief 12 min talk, Mikołaj Sikorski, New Business Developer DAGMA IT, provided us with new insights into the unconventional uses of Hexnode in the business world. Mikolaj listed three examples of the uses of Hexnode:
- Mikołaj talked about the employment situation in Poland and the necessity of providing the employees with exciting benefits. With the “New Normal”, one of the easiest method of entertainment is gaming. While the employees are encouraged to refresh their minds by gaming, the corporate devices used for the gaming purposes have to secured and managed by a suitable MDM solution like Hexnode.
- The logistics industry employs many truck drivers. These truck drivers are often equipped with tablets or devices with destination maps and directions. Mikołaj told us a story of how an accident occurred because the truck driver was watching a movie on the designated device. Using Hexnode, the company deployed 1500 devices in Kiosk Mode – so that the devices were locked down to the bare essential apps. The use of additional MDM features like Geofencing enabled the admin to block access to any unofficial/unneeded apps once the driver left his home/office.
- Using personal devices to access work-related documents is a big security loophole. Hexnode resolves that by implementing BYOD, so that the work apps and data are isolated in a separate container.
3. Make the best out of your Kyocera devices with Hexnode
 Bill Veasy, Director of Enterprise Sales at Kyocera International, hosted an informative session on managing Kyocera devices with Hexnode MDM. Kyocera is a giant in Rugged Mobile device industry, with around 265 companies spread over in 40 countries. The rugged devices are used in toughest conditions. Hexnode-Kyocera partnership allows easy management of these rugged devices:
Bill Veasy, Director of Enterprise Sales at Kyocera International, hosted an informative session on managing Kyocera devices with Hexnode MDM. Kyocera is a giant in Rugged Mobile device industry, with around 265 companies spread over in 40 countries. The rugged devices are used in toughest conditions. Hexnode-Kyocera partnership allows easy management of these rugged devices:
- Hexnode Kiosk Mode: The rugged devices are locked down to the required apps, increasing the productivity of the employees.
- Low cost of ownership, as there is a reduction in cost of replacing broken phones
- The Kyocera phones are Android Enterprise recommended and have zero-touch support, i.e, the devices can be enrolled into the MDM using out-of-the-box enrollment method.
- Timely security updates using Hexnode MDM
The partnership was further illustrated with the help of two case studies – in construction and manufacturing.

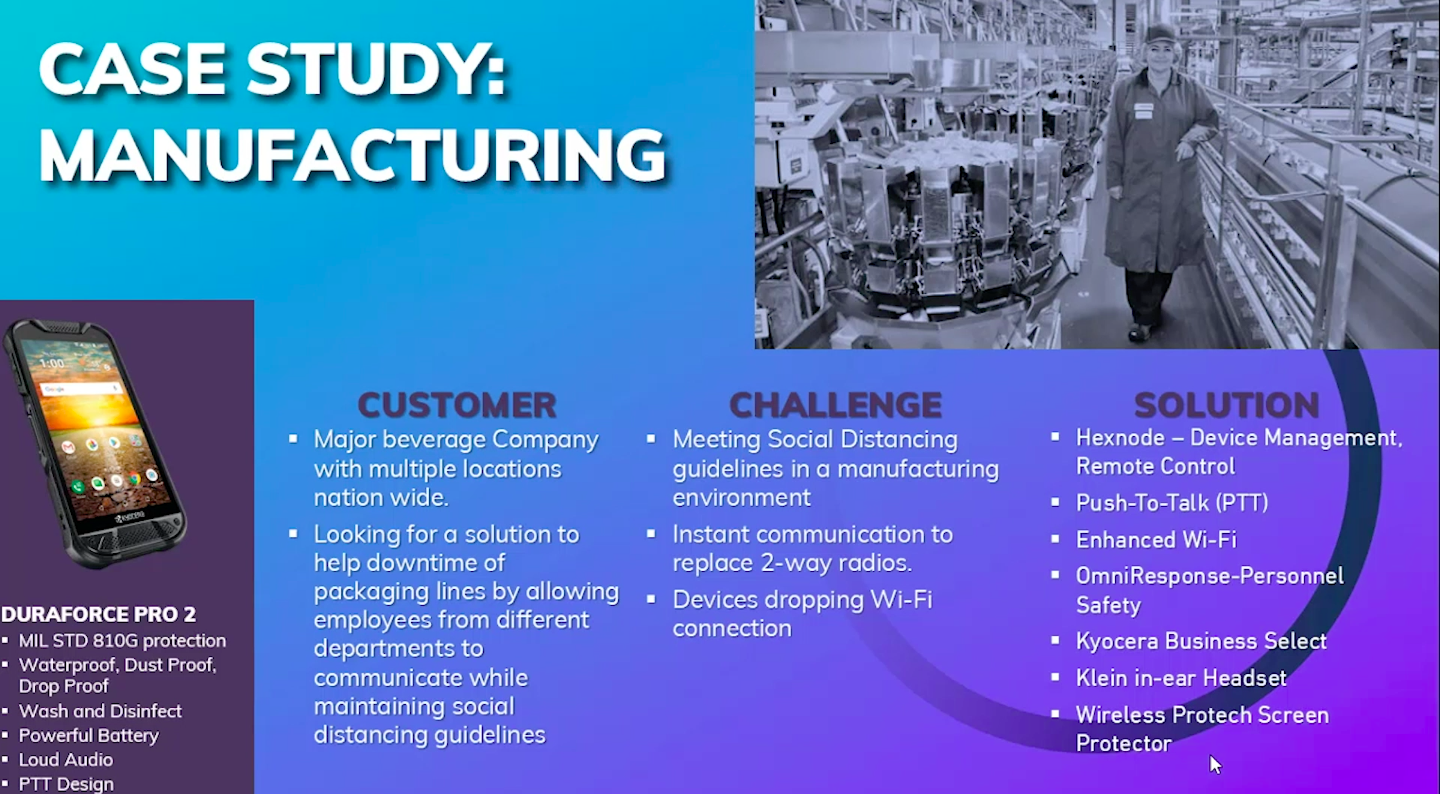
4. Selecting the best out of Hexnode and Samsung
 This session provided us an illuminating discussion between Sunil Kumar Behera, Technical Account Manager at Samsung Electronics, and Sarika Abraham, Marketing Manager at Hexnode. Important questions such as “What is Samsung Knox?”, “How does Samsung Knox increase the Mobile Device Management capabilities?”, “How does Knox Service Plugin(KSP) work?” and more were addressed.
This session provided us an illuminating discussion between Sunil Kumar Behera, Technical Account Manager at Samsung Electronics, and Sarika Abraham, Marketing Manager at Hexnode. Important questions such as “What is Samsung Knox?”, “How does Samsung Knox increase the Mobile Device Management capabilities?”, “How does Knox Service Plugin(KSP) work?” and more were addressed.
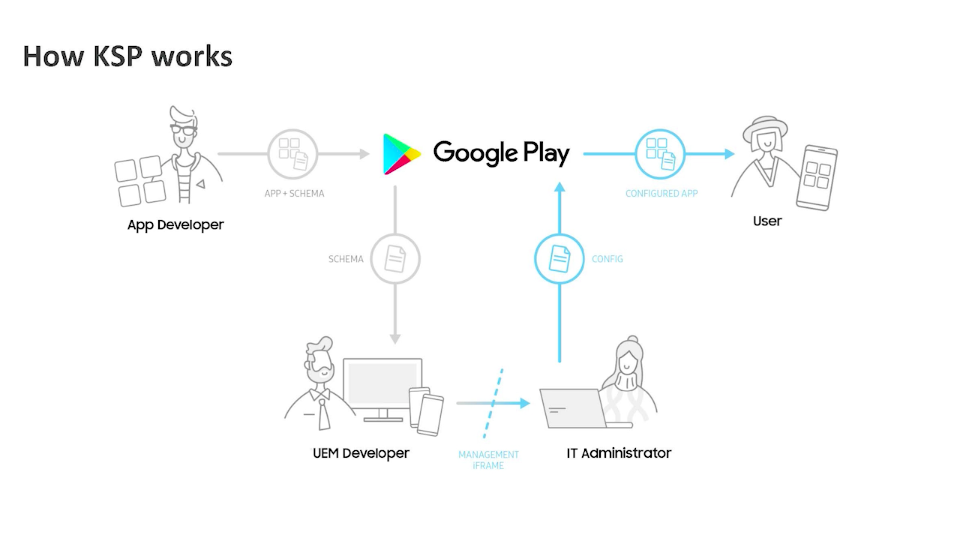
Knox platform builds a unique trusted environment in four ways:
- It establishes a hardware root of trust on which other components rely
- Build trust during boot using features like Trusted Boot
- Maintains trust while the device is in use using features like Real-Time Kernal Protection(RTP)
- Proves trust on-demand through device health attestation
5. A brief look at Desktop Virtualization
 The COVID-19 pandemic called for a new agile and productive work environment. Asad Siddiq, Director at Bounce Back Technologies, addresses this challenge and provided us with a brief overview of virtual desktops and the way they can be used anywhere, any place and anytime by the employee. All the major cloud services provide Desktop as a Service(DaaS) solution. A single virtual desktop that users can login from anywhere, anytime and on any device using Single Sign-On(SSO), complete control over security, storing everything on cloud and lack of delays are some of the many advantages of Desktop Virtualization discussed in this session.
The COVID-19 pandemic called for a new agile and productive work environment. Asad Siddiq, Director at Bounce Back Technologies, addresses this challenge and provided us with a brief overview of virtual desktops and the way they can be used anywhere, any place and anytime by the employee. All the major cloud services provide Desktop as a Service(DaaS) solution. A single virtual desktop that users can login from anywhere, anytime and on any device using Single Sign-On(SSO), complete control over security, storing everything on cloud and lack of delays are some of the many advantages of Desktop Virtualization discussed in this session.
6. Endpoint security risks no one is talking about in 2020
 Joseph Steinberg, Cyber Security Expert, Founder and CEO of SecureMySocial, captured our attention with a real story of a cyberattack on the endpoints at his workplace 23 years ago. Since then, there has been huge leaps in technology, and the attacks have also become more sophisticated. Endpoint Security is perhaps tougher and more important today than it was 23 years ago. Joseph identifies three areas of endpoint security that are not getting enough attention:
Joseph Steinberg, Cyber Security Expert, Founder and CEO of SecureMySocial, captured our attention with a real story of a cyberattack on the endpoints at his workplace 23 years ago. Since then, there has been huge leaps in technology, and the attacks have also become more sophisticated. Endpoint Security is perhaps tougher and more important today than it was 23 years ago. Joseph identifies three areas of endpoint security that are not getting enough attention:
- Definition of endpoints: The older definition of endpoints was that of desktops and laptops in the office physically connected to the network. Today, endpoints are not necessarily in the office, are very mobile, and display a diverse set of technology. The focus is on endpoints and not on the environments in which they reside. The environment is also important for endpoint security.
- Endpoint security and server security has gotten blended, but people don’t recognize it. For example, in supply chain attacks, a third-party code may inject a malware that you may in turn transmit to your client – and you become an unwilling participant in the cybercrime.
- Management of endpoints in an efficient manner is necessary to keep them secure. The device management solution should meet all business requirements and should not rely on endpoint users for the management of the endpoints.
7. SaaSOps: A new way to automate management tasks and protect data
SaaSOps will be the heart and soul of IT… Covid-19 has forced businesses to adapt SaaS-based tools, and now they must continue to change and adapt or they will not survive
-Colin McCarthy
 The VP of Global IT Essence, Colin McCarthy, gave us an enlightening talk on SaaSOps – Software as a Service Operations. The ‘New Normal’ has accelerated the adoption of cloud based collaboration tools and the drive to be a Zero Trust Network model company. Researches show 85% of business apps will be SaaS-based by 2025. Organizations need to have the ability to manage, integrate and secure SaaS environments. A major challenge for IT admins is Shadow IT, I.e., downloading unsanctioned SaaS apps. SaaS management platforms(SMP) centrally manage Google Workspace, Office 365, Slaac, Zoom and many others. Workflows can be created to automate repetitive tasks and alerts setup to prevent potential data loss.
The VP of Global IT Essence, Colin McCarthy, gave us an enlightening talk on SaaSOps – Software as a Service Operations. The ‘New Normal’ has accelerated the adoption of cloud based collaboration tools and the drive to be a Zero Trust Network model company. Researches show 85% of business apps will be SaaS-based by 2025. Organizations need to have the ability to manage, integrate and secure SaaS environments. A major challenge for IT admins is Shadow IT, I.e., downloading unsanctioned SaaS apps. SaaS management platforms(SMP) centrally manage Google Workspace, Office 365, Slaac, Zoom and many others. Workflows can be created to automate repetitive tasks and alerts setup to prevent potential data loss.
Colin discussed the benefits such as support and services, Google Apps Manager(GAM) which is available for free, and ease of testing as everything is built around the publicly published API. In 2020, organizations highly leveraged SaaS platforms to shift employees out of physical offices into remote home-based working environments in a short amount of time.
Top priorities to pivot from a physical to a completely virtual environment were identified including but not limited to video conferencing, better secure remote workplace, making IT decisions that directly impact profitability. Balancing security vs productivity is an important consideration in SaaSOps.
8. How to dramatically reduce your Enterprise Mobile Expenses
 Alex Dukhovny, Executive Vice President at Intratem, discussed with Amith Manoj, Senior Product Evangelist at Hexnode, on ways to reduce the Enterprise Mobile expenses. Gartner estimates that 80% of the companies would over-spend on their wireless bills. Using the data management feature of Hexnode, you can greatly reduce the data usage by allocating specific amount of data to each individual user.
Alex Dukhovny, Executive Vice President at Intratem, discussed with Amith Manoj, Senior Product Evangelist at Hexnode, on ways to reduce the Enterprise Mobile expenses. Gartner estimates that 80% of the companies would over-spend on their wireless bills. Using the data management feature of Hexnode, you can greatly reduce the data usage by allocating specific amount of data to each individual user.
9. Endpoint security: Best practices
 Bob Fabien Zinga, Cyber Security Executive and Director of Information Security at Directly, conducted an informative session going into detail about the importance of endpoint security and the best practices to follow while ensuring endpoint security. Bob recommended using Hexnode MDM and implementing the following measures:
Bob Fabien Zinga, Cyber Security Executive and Director of Information Security at Directly, conducted an informative session going into detail about the importance of endpoint security and the best practices to follow while ensuring endpoint security. Bob recommended using Hexnode MDM and implementing the following measures:
- Updated OS – The endpoint devices should have updated OS at all times. Bob illustrated the importance of installing the updates regularly using the example Conficker and Flashback. Conficker affected Windows devices and was discovered on November 7, 2008. The patch was released on October 8, 2008, almost one month before discovering Conficker. If the devices had been updated, then they would have been safe. Similarly, Flashback affecting macOS was discovered on 1st April 2012, while the patch was released on the 5th of the same month.
- Full Drive Encryption(FDE)
- Password policies – Long and complex passwords would be a harder nut to crack. Different passwords should be used everywhere.
- Turn on firewall
- Restrict admin access- Follow the Principle of Least Privilege
- Avoid malicious websites – Use web content filtering to block access to potentially malicious websites.
- VPN – Secures the corporate data and prevents man-in-the-middle attack.
- Backup the data – Whenever possible, backups of data must be generated.
10. Are VPNs really secure?
 Levent Ozdayi, Value Added Services Manager Logosoft Information Technologies, addressed the concerns on how secure the widely used VPNs are.
Levent Ozdayi, Value Added Services Manager Logosoft Information Technologies, addressed the concerns on how secure the widely used VPNs are.
VPN endpoints are vulnerable to attack even from junior hackers. Multiple challenges are faced by organizations in implementing VPN. The traditional VPN is very susceptible to security breaches. Implementing a VPN is no easy task as it is often costly and hardware dependant. Scalability is also a challenge. Levent also threw light on how using Hexnode would ease and secure implementing VPN in the corporate devices.
In addition to the breakout sessions, training sessions on Mac Management, Windows Management and Integrations & API were held. As a special treat, the Hexnode certification exam was hosted live for everyone who registered for HexCon20. The attendees had access to both levels of certification just for the day.
The day wrapped up with a closing keynote speech from Apu Pavithran, founder and CEO of Hexnode.
Stay tuned for more blogs on Hexcon20 so that you can catch up on everything you missed.


 Sana’ Al-Sharaideh, Manager in ITC Research and Development at Nathealth, and a valued customer of Hexnode, shared with us her experience with Hexnode MDM. Nathealth covers the widest medical network in Jordan and has deployed over 6500 devices across the Kingdom. The requirement was to install a customized app in the deployed devices and to restrict the device settings. Initially, there were many challenges such as preventing uninstallation/deletion of the custom app and blocking the user access to device settings. After testing multiple MDMs, Hexnode was found to be the most reliable MDM with all the required features and excellent customer support. On deploying the devices using Kiosk Mode, the users were no longer able to access any unnecessary apps or the device settings unless allowed by the admin. After the deployment, the workload was reduced by a whopping 70% – leading to greater ease in day-to-day tasks and remote operations.
Sana’ Al-Sharaideh, Manager in ITC Research and Development at Nathealth, and a valued customer of Hexnode, shared with us her experience with Hexnode MDM. Nathealth covers the widest medical network in Jordan and has deployed over 6500 devices across the Kingdom. The requirement was to install a customized app in the deployed devices and to restrict the device settings. Initially, there were many challenges such as preventing uninstallation/deletion of the custom app and blocking the user access to device settings. After testing multiple MDMs, Hexnode was found to be the most reliable MDM with all the required features and excellent customer support. On deploying the devices using Kiosk Mode, the users were no longer able to access any unnecessary apps or the device settings unless allowed by the admin. After the deployment, the workload was reduced by a whopping 70% – leading to greater ease in day-to-day tasks and remote operations.



