Apple’s midyear event Worldwide Developers Conference (WWDC) is entirely virtual this year. The ongoing event WWDC 2020 sets the stage for exciting announcements about the new operating systems, new software, and technologies for software developers and consumers alike.
The consumers have a lot to look forward to as the first day of WWDC unveiled interesting new features. App Library and app clips for iOS, and Control Center for macOS are some of the noteworthy developments.
Apple has launched its new OS versions iOS 14, iPad OS 14, and macOS Big Sur. For the Macs, Apple has switched from the Intel processors to custom ARM-based CPUs designed in-house, just as it has been done for iPhones and iPads till now. Apparently, the change would bring about a “whole new level of performance” with efficient usage of power.
What do all these developments mean for Apple device management? Let’s have a look at what’s new in managing Apple devices in the 2020 version of WWDC.
- Managing macOS Big Sur
- 1. Automated device enrollment and setup
- 2. Lights Out Management for Mac Pro
- 3. Supervision for User Approved MDM
- 4. Managed Software Update
- 5. Managed Mac Apps
- 6. Content Caching Information
- 7. Bootstrap Tokens for Easy Security
- 8. Preventing accidental installations of downloaded Profiles for Mac
- 9. Preventing silent profile installs from the command line
- 10. networksetup Limitations for Standard Users
- 11. Format change for Serial Numbers
- Managing iOS 14 and iPadOS 14
- 1. Locations for Volume Purchased Apps and Books in Apple Configurator
- 2. Setup Assistant Skip options
- 3. Shared iPad for Business
- 4. Prevent the uninstallation of Managed Apps
- 5. Managed Open-in for My Shortcuts
- 6. Managed Notification Previews
- 7. Set Time zone for managed devices
- 8. Per Account VPN for iOS
- 9. Wi-Fi Mac Address Control
- Custom App Distribution Support for Apple School Manager
- Device Authentication and MacOS account types
- Single Sign-On
- Federated Authentication and SCIM
- To sum up…
Managing macOS Big Sur

1. Automated device enrollment and setup
Just like for the OS X series, the organization would need to have an Apple Business/School Manager account for zero-touch deployment (formerly Apple DEP). The organization owned devices are automatically enrolled in the MDM when the user selects the language and connects to the Wi-Fi. Enrollment customization allows for brand customization and authenticated enrollment. The use of authenticated enrollment is useful for third-party integrations such as Microsoft Active Directory and OKTA. The IT admins can pre-populate the macOS account name and select which steps are to be shown in the setup assistant.
2. Lights Out Management for Mac Pro
The admins can remotely startup, reboot, or shutdown one or more Macs even if they are unresponsive. The task is accomplished by sending a command from the MDM server to the MDM-enrolled controller on the Mac network. Lights Out Management requires:
- macOS Big Sur
- The Macbook Pros to be on the same subnet
- The Lights Out Management Payload to be installed.
How does it work?
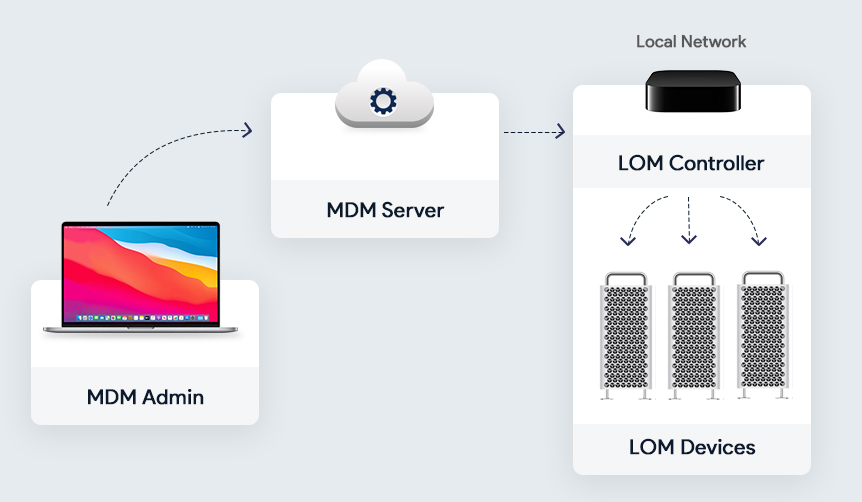
One of the enrolled Mac devices in the local network acts as the LOM Controller. All the other enrolled Macbook Pros act as the LOM devices. All these LOM devices are connected to the LOM Controller. A command is sent to the MDM server which is received by the LOM controller which in turn distributes it to the other enrolled Macs in the network.
3. Supervision for User Approved MDM
The announcement of supervision for User Approved MDM has revolutionized the face of Apple Device Management. Now, the admins have the same control over the user-enrolled devices as they had on the devices enrolled with Apple Business/School Manager. The admins would be able to query, list, and delete local users, control Activation Lock Bypass, install supervised restrictions profile using MDM, or even schedule software updates.
4. Managed Software Update
Using an MDM, the IT admins can now manage the software updates in the enrolled Mac devices. Here is a list of how IT can manage the software updates:
- Force the managed Macs to accept the software update.
- Defer major OS and non-OS updates for 90 days.
- Removal of software update catalog.
- Removal of the Ignore Flag for major updates only.
5. Managed Mac Apps
Managed Apps have been around for a long while for iOS devices. For Mac devices, managed apps are a welcome addition. The Managed Mac apps can be removed from the Macs by MDM command or on disenrollment of the devices. Similar to the managed apps on the iOS, app configurations and feedback are supported for the Managed Mac Apps. The unmanaged apps can be converted to managed apps using the MDM solution if the devices are enrolled using the automated device enrollment.
6. Content Caching Information
Content caching is a macOS service that speeds up software installation and helps to reduce internet data usage for the Macs in the same network. This is achieved by saving the content already downloaded by the local Macs in a content cache so that the other devices can retrieve this information without browsing the Internet.
The Content Caching Information command helps the IT admin to determine whether the content caching is turned on and working properly for the users. It gives crucial information such as registration state, cache pressure, bytes served, and many more.
7. Bootstrap Tokens for Easy Security
Bootstrap tokens are encryption keys provided by the MDM server used to create admin accounts in the macOS devices without using a password for authentication. Instead of using complicated workflows for creating the admin account and user accounts, the bootstrap token enables users to get a secure token and boot a Mac that uses FileVault. This is a coveted feature for network accounts. The admins can take advantage of authorized software updates and kernel extensions once this is implemented. Bootstrap tokens are supported on all the latest Macs with Apple T2 Security Chip.
8. Preventing accidental installations of downloaded Profiles for Mac
For iOS devices, the downloaded profiles have to be manually installed from the device settings to prevent the accidental installation of potentially harmful profiles. The feature is now implemented for Mac devices too. To install the downloaded profile, the user has to go to the device System Preferences > Profiles > Downloaded Profiles and install the profile using the user password after previewing it.
The user can choose not to install the downloaded profile. Once downloaded, the profile stays on the system preferences pane for eight minutes before being removed.
9. Preventing silent profile installs from the command line
For enhanced security, complete silent installation of profile using the terminal would no longer be supported from macOS Big Sur. The profiles to be installed using the terminal would be treated as a downloaded profile. The user would have to go manually to the System Preferences and install the profile just like with a downloaded profile. All other features of the profiles command line tool would remain the same and work as expected without allowing the installs.
10. networksetup Limitations for Standard Users
The networksetup tool makes it easy for the users to view and edit the network settings using the terminal. Previously, the admin and standard user accounts had the same control over networksetup. With the advent of Big Sur, there is now a clear set of limitations for standard accounts. The standard users can:
- Read network settings
- Turn Wi-Fi on or off
- Change the Wi-Fi access point.
The device security is additionally hardened by a new Privacy setting: “Require an administrator password to access system-wide preferences”. However, admins can get around this setting using the sudo command.
11. Format change for Serial Numbers
Serial numbers of the Mac devices serve not only as unique identifiers but also for automated device enrollment. The existing 12-digit serial numbers contain bits of identifiable information such as where and when the device as built. To prevent malicious use of identifiable data, Apple will now use completely random 10-character serial numbers.
Managing iOS 14 and iPadOS 14
1. Locations for Volume Purchased Apps and Books in Apple Configurator
Apple Configurator is a great method to deploy iOS, iPadOS, and tvOS devices when time is of the essence. The devices can be configured with ease and speed by the Apple Configurator app using a USB cable. Now, the Apple Configurator supports Locations for Apps and Books provided by Apple Business/School Manager. Locations can be used to distribute entirely different sets of apps and books to different devices as per the enterprise requirements.
2. Setup Assistant Skip options
The Setup Assistant Skip keys allow you to skip the setup panes and get to the home screen of the device with minimum steps. Two new keys have been introduced for the purpose:
- Getting Started
- Update Completed
The Setup Assistant Payload can be used to skip the setup panes during the upgrade for all supervised devices.
Schools have been using shared iPads for providing a personalized experience for the students even if they are sharing the iPads. Now, businesses can use shared iPads by signing in with the Managed Apple IDs created by Apple Business Manager. This feature would prove to be a boon for service industries like restaurants for taking orders from their customers.
With Microsoft Azure Active Directory integration, users can sign in to the shared iPads using federation authentication. Shared iPads also support Single Sign-on extension.
Additionally, shared iPads supports dynamic number of cache users that allows you to set the amount of storage for each user. The IT admin can also delete all the users of the shared iPad at once.
4. Prevent the uninstallation of Managed Apps
To prevent the removal and offloading of critical managed apps by the users, specific managed apps can be marked as non-removable. When the user attempts to delete or offload a managed app, an alert is displayed and it is prevented.
5. Managed Open-in for My Shortcuts
Shortcuts are a new productivity feature for getting things done quickly. What does managed open-in for shortcuts mean? When a shortcut triggers an action where the data flow is not allowed, the shortcut immediately stops running. This is done by preventing the data flow between the managed and unmanaged apps and services. This ensures that the organizational data is protected from accidental leakage.
6. Managed Notification Previews
Device and data security can never be compromised on. With managed notification previews, you can prevent the apps from displaying message previews in notifications. The IT admin can choose to show the preview always, when unlocked or never. This feature is available only on supervised devices.
7. Set Time zone for managed devices
Remote management of devices across different locations in the world is becoming the norm these days. Setting the correct time zone is an essential feature for IT admins. For devices located in different parts of the world, Apple has introduced the capability to choose specific time zones for individual devices. This feature is not dependant on the location services of the device.
8. Per Account VPN for iOS
Virtual Private Networks allows users to send and receive data across public networks. IOS supports three types of VPN:
- Full Tunnel: Allows all traffic to pass through it.
- Split Tunnel: Chooses which traffic to pass through it.
- Per-App VPN: Allows only certain apps flow through it.
The newly introduced Per Account VPN for iOS allows you to choose a replacement VPN for Contacts, Calendars, and Mail domains. Just like you can associate the traffic of an app with the VPN, individual accounts can be associated with the VPN.
9. Wi-Fi Mac Address Control
Beginning from iOS 14, a new security feature has been introduced. Whenever a device connects to a Wi-Fi network, it will use a random MAC address instead of the original device MAC address. For enterprise networks and captive portals, this feature may result in unexpected behavior. If the device fails to join such a network, the device would use its original MAC address. This feature can be disabled by the user in the device settings. The IT Admin can also disable this feature using the Wi-Fi payload.
Identity management has become the centerpiece of authentication for users in an enterprise. It is a critical part ensuring security across all Apple devices. WWDC20 had the following instore for a higher level of organizational security.
Device Authentication and MacOS account types
With the decline in the usage of shared devices, Apple has outlined that they always recommend local accounts over network/mobile accounts for 1:1 deployments. The local macOS directory service becomes the source of truth with the user record being stored locally on the mac which ensures password management on the mac and removes any unnecessary login delays. Local accounts provide the best, most reliable experience. Apple also asked enterprises to consider not binding their mac to a directory service and to instead opt for the built-in Kerberos extension, other SSO extensions or additional add-ons from MDM vendors.
The source of truth for network accounts is a directory service. The contents of the home folder can be directly accessed over a network but modern apps with databases, file sizes, and types, and mobility present challenges for network accounts. This has led to Apple considering network accounts as legacy but it is not deprecated and can be used if absolutely necessary.
If you really need to use a network account then a mobile account should be your first consideration. They are a type of network account where the source of truth is a directory but the credentials are cached locally. A local home folder is also created which solves the issue of modern apps though mobility is still a factor. The local directory ensures that the users can use the credentials even without a network, but this can cause login delays.
Single Sign-On
The introduction of single sign-on extensions have proven effective for device management. Apple has focused on its improvement which yielded the following upgrades.
User channel profile discovery is Apple’s way of helping MDM’s easily integrate configurations of SSO extensions on their devices. This is supported on both iPadOS and macOS. Settings on the user channel take priority over the system settings. This leads to easier user settings like setting a username.
Apple has also significantly improved how an SSO extension works with per-app VPN. Associated domains now work with per-app VPN and as a result SSO redirect extension can now redirect traffic for identity providers that are on-premise. SSO extensions inherit the per-app VPN settings of their host app. This can cause performance issues as all the traffic is routed through the same VPN, to counter this a new excluded domains list for per-app VPN has been introduced for load balancing via direct device to cloud idp traffic. Per-app VPN can also be reserved to be triggered for auth-only requests.
Associated domains also get a boost with the entitlement com.apple.developer.associated-domain.mdm-managed which is now public and no longer requires authentication from technical support. Apple app site association file will be no longer directly accessed by the device by default instead the file is accessed by an apple-operated content delivery network that is dedicated to associated domains which reduces the load on servers and routes devices to a known fast connection. For managed apps and for non-internet facing domains an additional parameter can be added to specify it.
WWDC20 has also revealed that Apple has focused a great deal on their Kerberos extension. The menu-extra on macOS now represents the state of the extension. A customizable UI to match the name of your identity in the Kerberos extension will be made available. Help text can also be added to the bottom of the sign in window to inform users when they have trouble logging in. More control for admins, when a user is prompted to login for the first time which is delayed until the first authentication challenge or the admin runs a prompt to enable it. An optional managed app access control is also added which can restrict unmanaged source applications from accessing credentials.
Federated Authentication and SCIM
It is a simple and secure identity management architecture that spans organizational boundaries, it allows organizations to connect to existing identity systems based on Azure AD.
To set up federated authentication the first step is to complete a domain verification. From here you can sign in as an administrator and provide consent. Now you have to sign in as a user in the domain for completing the test. The next step is to review username conflicts and initiate a resolution for it. Once these steps are complete you can turn on federation for your organization.
System for cross-domain identity management (SCIM) is Apple’s latest integration to aid federated authentication management. SCIM is set to be rolled out later this year. It is aimed at the synchronization of account data between the Azure active directory and Apple Business Manager or Apple School Manager. It is a standards-based data exchange that spans an entire accounts life cycle (creation, updating, and deletion). SCIM ensures that the 2 repositories are synced up at all times. It is available for all federated organizations and is definitely an integration worth the wait.
The session ended with a reminder that SSO extensions and federation are complementary services Apple still relies on managed Apple ids for authentication, federation helps create a bridge to enable external integrations.
Apple Push Notification service (APNs) is an Apple service for maintaining communication between the Apple devices and third-party services such as an MDM. In WWDC 2020, it has been announced that APNs would support proxy configurations from macOS 10.15.4 and iOS 13.4. This development now makes it easier for Apple devices to communicate with the MDM even in a proxy network. APNs proxy support will provide full MDM functionality on proxy enabled networks. The APNs traffic is encrypted and hence is completely secure.
To sum up…
Each update of Apple’s OS platforms brings with it a wide array of tempting features for consumers and professionals alike. Many new ground-breaking features and technologies have been announced in WWDC that could totally change the face of Apple device management as we know now.