Why Enterprise Mac Management
Learn why managing Macs in the enterprise is essential for the security of your business

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Alma Evans
Sep 30, 2020
13 min read

For decades, Apple strongly advocated that their MacBooks and iMacs are free from serious security threats. One should admit that the statement is overwhelmingly true up to a certain extend as Macs were a far less tempting target for cyber attacks. But those days are long gone. The prime reason for macOS being less prone to attacks as compared to Windows was the relatively lower number of systems running the macOS. But as Apple’s operating system is becoming much more popular, threats targeting macOS is unfortunately far too common. Despite all the stringent security measures taken by Apple for macOS protection, the threat landscape for the platform is changing, malicious codes targeting Macs are proliferating than ever, and the company may have to acknowledge that their highly regarded operating system is no longer resistant to malware attacks.
With the increase in market share, Mac has become an attractive target, and cybercriminals are toiling more to develop advanced full-fledged malware for the platform, mostly targeting business users than other individuals. To add, in-built defense mechanisms and security measures for Mac failed to come to fruition, leaving the doors open for these malicious actors to intrude. macOS malware has come a long way from isolated incidents to thousands of malware data breach cases reported in the past few years. What this sudden change is aiming to tell is that it is high time to come out of the presumption that macOS is invulnerable to security threats, have a long hard look at the different aspects of macOS malware, and think what you can do to ensure the device safety.
Malware, the short form for malicious software, is any code, script, computer program, or other kinds of software specifically designed with malign intent to damage, disrupt, or gain unauthorized access to a computer, server, or a network of computers. They can hide within the system and collect sensitive data that is being processed in the computer’s chip or stored within the system. Mac system rarely shows symptoms that tip off to being infected by malware. Many malware doesn’t act suspiciously but runs quietly in the background as cybercriminals are giving particular care to build sophisticated malware programs.
The installation process of most malware starts with users unknowingly downloading app installers or files from the web. Being unauthorized, the software will be blocked by the built-in security features in Mac, but the user will be provided with instructions to bypass the security restrictions to install the package. The intended software is then installed along with malware payloads, which are saved to any hidden folder so that there is nothing suspicious.
Once the malicious software is installed within the system, it searches throughout the system for executable files. It then affixes malicious code at the beginning of the file, and when the file is finally executed, the malicious code will be the first thing to be executed. The code can copy file content to new invisible files and do other malicious actions.
Most of the data breaches and damaging malware attacks happen due to negligence, which opens up potential security holes that the malicious threats take advantage of to harm your Mac or your privacy. Users clicking on malicious links, downloading apps from unreliable or illegitimate sources, allowing unauthorized access to their systems, leaving sensitive data exposed, failing to update the software on time, etc. can welcome malware to their system. Any Mac user can fall victim to this.
One of the common ways cybercriminals use to distribute malware is to embed them in genuine looking apps or maliciously modifying genuine applications. The norm of installing apps outside the Mac App Store turns out to be a blessing for cybercriminals. Malware are also distributed with email as attachments and through the internet in the form of web downloads. Criminals provide fake data that make everything appear authentic.
Installation of malware on Mac cause many hardware and software vulnerabilities, totally wrecking the system proving arduous to get rid of which includes:
Malware can range from annoying and relatively harmless popups to outright full-fledged damaging programs. A single malware program often includes multiple malicious functions with equal or varying threat levels. Many intents to take control of the user’s Mac, host illegal content, collect sensitive information, and spread the infection to all other computers belonging to the same network. Some malware can be quite a nuisance than a danger. There are different types of malware with different malicious codes contained in them, and each of them behaves entirely different once they get into the Mac system.
Malware are always evolving to become more potent. Here is a quick list of some recently reported Mac malware:
Some recent statistics
In the last decade, the cyber threat landscape is clearly showing an inclination towards businesses with increasing business-focused threats and more sophisticated attack vectors. Initially, Macs were less susceptible as they were less in number for enterprise use. But as the enterprise share of the Mac platform suddenly shoot up, there’s a sudden uptick in the threats targeting Macs.
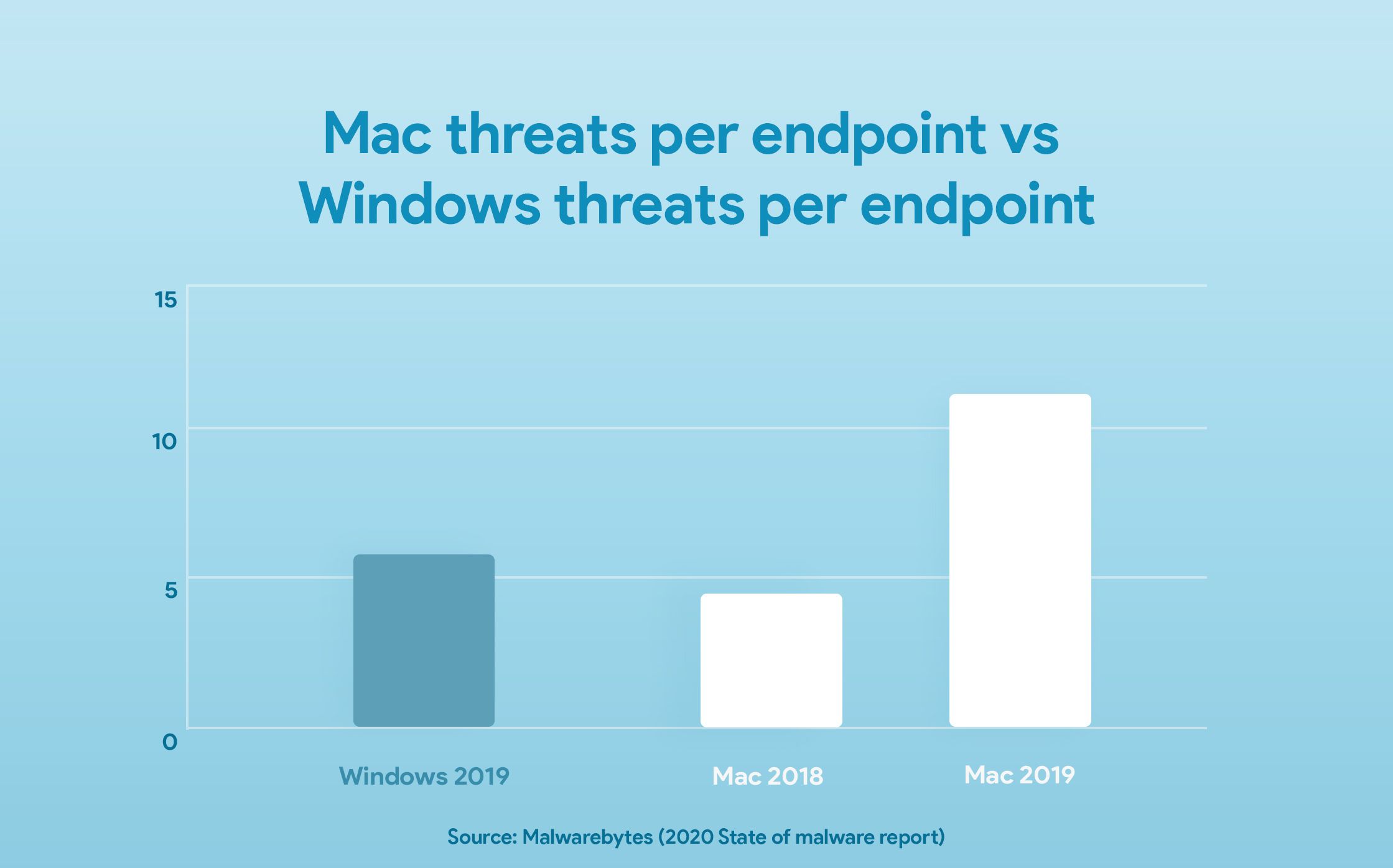
The 2020 State of malware report by Malwarebytes shows that Macs has surpassed Windows with more threats per endpoint in the period of 2018 – 2019.
In order to prevent malicious attacks, Apple has in hand some of the strictest security strategies, though, on occasions, some effectual malicious software slips out of the net to enter the Mac system. There are stringent security checks for all the apps distributed via the Mac App Store. In addition to this, there are some other security mechanisms and examinations a Mac software should pass through.
Gatekeeper has been an inevitable part of Apple security mechanism for years since macOS Mountain Lion and is often referred to as OS X’s defense against malware. Gatekeeper’s duty is to check the downloaded to make sure that only trusted software runs on Macs. Gatekeeper checks code signing and ensures that the app is verified by Apple before allowing the application to run on the system in order to minimize the likelihood of inadvertently executing malware.
App notarization is one of the toughest security measures taken by Apple for software distributed outside the Mac App Store. Notarization is the process of getting a stamp of approval from Apple after an app downloaded from a third-party server passes through the notarizing security process by the Apple notary service, which scans the software for malicious content. Gatekeeper allows only notarized software to run on Mac.
The default Mac internet browser, Safari, has the capability to identify websites containing malware. Safari is a full-featured browser with many more security features, including ad-blocking, blocking unwanted popups, private session browsing, intelligent tracking prevention, warning before connecting to unencrypted sites, and prompts of approval before downloading files.
All the above-mentioned security mechanisms are helpful but can’t be considered universal. History shows that many advanced malware can easily bypass them. With this in the mind, it’s better to complement the Apple security mechanism with additional security measures. Businesses themselves have to reconsider their security strategy and take steps to tie over the ever rising tide of malware attacking macOS.
As macOS cannot be considered totally bullet-proof, an average Mac user should exercise cautious online behavior to take malware off their system. Understanding the different ways by which Macs can be infected is the prime step to keep your Macs and files safe and secure. Some of the major malware attacks can be prevented by simply taking the proper security measures while using the device and the internet. As malware are always evolving, there is a constant need to update the security practices to inhibit the latest mode of attacks.
Here are few guidelines to ensure that Mac systems are less susceptible to malware:
If the system is found infected with macOS malware: