What is Role-Based Access Control?
Role-based access control is a security framework that controls access to resources based on the user roles.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Elaine Claire
Apr 21, 2025
9 min read

In a world where digital systems are integral to every aspect of business, managing the evolving needs of user access throughout their journey can quickly become overwhelming. Think of a scenario where a company hires a new employee, who needs access to various systems from day one. However, as she transitions into her role, her responsibilities change, requiring different levels of access. Without a dedicated tool that serves the purpose in place, managing these access rights can become chaotic and prone to errors.
Identity Lifecycle Management (ILM) is the systematic approach to managing user identities and their access privileges throughout their lifecycle within an organization – from onboarding to off-boarding. It encompasses everything from granting access rights when employees join, to adjusting permissions as roles evolve, and finally, securely revoking access when they leave. With the rise of remote work and cloud solutions, effective ILM is more crucial than ever. It enables organizations to maintain security, streamline processes, and enhance productivity in an increasingly dynamic environment. Understanding ILM’s role in today’s environment requires examining why dedicated ILM tools and systems have become essential.
Identity lifecycle management tools largely enhance workforce efficiency and help to alleviate redundancy in identity management. Though a large number of enterprises still rely upon traditional manual practices for onboarding their employees, these methods are highly inefficient, especially on a large scale.
Manual methods are still prevalent in managing evolving access privileges and their de-provisioning. This often causes security loopholes, as accounts and access privileges may remain active after employees leave or no longer need access. This may lead to exploitation by rogue workers and adversaries.
Download the White paper to enhance your organization's access management methods and ensure device and data security.
Download PDFAn efficient ILM overcomes these challenges by automating the process of onboarding, re-provisioning access and de-provisioning privileges causing reduced chances of error and vulnerabilities. They aid in improved workforce efficiency by granting day one access to applications and IT services.
Privilege creep is a threat to the data security and integrity of the organization. It is the situation of unregulated gradual accumulation of access rights where an employee has greater access than they require to perform their tasks.
Consider an employee who initially needed access to specific financial data for a project. Over time, as they transition to new roles or responsibilities, their access rights may not always be updated to reflect these changes. As a result, they retain access to sensitive financial information they no longer need. This scenario, known as privilege creep, becomes a security risk, as it gives individuals more access than is necessary for their current role. Privilege creep often arises from insufficient access management and inadequate processes for revoking unnecessary permissions, ultimately leading to data security vulnerabilities within the organization.
Implementing effective ILM practices helps enterprises address privilege creep by enforcing the principle of least privilege. This ensures employees only have access to the resources they need for their roles, reducing unnecessary access and strengthening security.
ILM systems also generate detailed reports on user activity and access changes, making it easier to meet compliance requirements for regulations like GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), or SOX (Sarbanes Oxley Act). These reports provide transparency on who accessed what, when, and why, which is crucial for both internal audits and regulatory inspections. By automating compliance monitoring and reporting, ILM helps organizations stay ahead of legal requirements and avoid costly penalties.
The stages of ILM define the steps for managing user identities and access throughout their time within the organization.
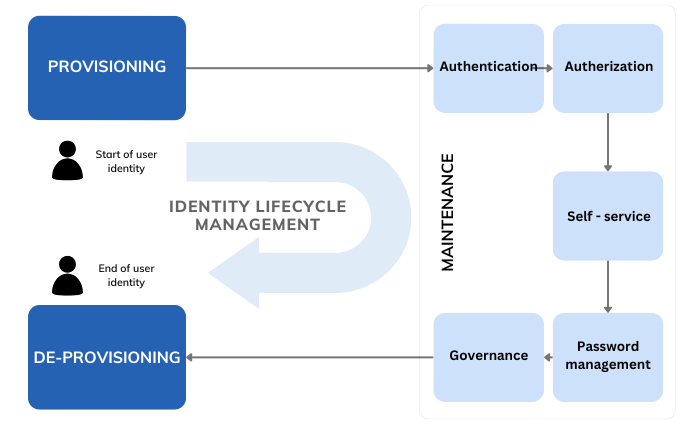 Stages of Identity Lifecycle Management
Stages of Identity Lifecycle ManagementProvisioning marks the beginning of the identity lifecycle. It involves creating user accounts and assigning them the necessary access to systems, applications, and data. This typically happens when a new employee joins or when an existing user requires access to new resources. Automated provisioning ensures that access is granted quickly and accurately from day one, minimizing delays and reducing the risk of errors compared to manual processes.
This phase focuses on managing user identities and access throughout their lifecycle in the organization. It includes updating permissions based on role changes, ensuring only the right people have access to specific resources.
Key components like authentication and authorization safeguard access, while self-service options, such as password resets and access requests, empower users and ease the IT workload. Governance controls also play a key role in maintaining compliance and enforcing least-privilege access as responsibilities shift over time.
De-provisioning occurs when users leave the organization or no longer need certain access. This stage involves revoking permissions and removing accounts to prevent unauthorized access.
Timely de-provisioning is crucial to data security and regulatory compliance. Automating this process helps ensure that access is removed promptly and consistently, protecting the organization from potential security breaches.
Identity Lifecycle Management (ILM) offers a range of features that help simplify how organizations manage user identities and access. These functions are designed to improve both efficiency and security, ensuring that users have the right access at the right time.
ILM offers tools that simplify and automate the entire employee onboarding and off-boarding process. These tools ensure that new hires quickly receive the access they need to start working, while departing employees have their access promptly revoked. This automation minimizes delays, reduces human error, and strengthens security by consistently managing access rights as employees join, transition, or leave the organization.
Self-serve portals are a key feature of ILM, empowering users to request access changes or reset passwords through intuitive platforms. By allowing employees to manage basic tasks independently, these portals reduce reliance on IT support, speed up processes, ultimately enhancing overall efficiency within the organization.
This feature ensures that access requests go through proper channels for approval. This results in timely decision making and reduces manual errors.
ILM solutions help us keep a record of access changes. This functionality supports audits, ensures regulatory compliance and enhances visibility into identity management processes.
ILM solutions with the ability to easily integrate with HR platforms and corporate directory services ensures that identity data is always up to date. This simplifies identity management for organizations.
Identity lifecycle management has changed over the years and has adapted to meet the needs of the ever-evolving digital landscape.
As organizations are moving away from traditional on-premises solutions to cloud-based services, the ILM sphere has undergone a significant transformation. Cloud-based ILM solutions often delivered through Identity as a Service (IDaaS), offer several advantages including scalability, lower operational costs and better integration with modern cloud applications.
Additionally, it also makes it easier to manage identities for remote or distributed workforces, offering more flexibility than legacy systems.
As workforces become more flexible and location-independent, the need for IDaaS solutions has grown significantly. This shift has driven the evolution of identity lifecycle management, with several expert solutions emerging to meet the demands of modern enterprises.
Managing identities and access is critical, but what happens when the devices tied to those identities come into play? This is where Unified Endpoint Management (UEM) steps in, extending ILM capabilities to include seamless device management for a more comprehensive approach. While ILM focuses on managing the entire lifecycle of user identities, UEM takes this a step further by combining identity management with comprehensive device oversight. This creates a unified solution that addresses both identity and device needs. Thus, providing organizations with a comprehensive approach to security and management.
UEM solutions with ILM capabilities offer a holistic approach to identity and device management. These solutions encompass ILM functionalities within its framework. Notably, Hexnode UEM is adept at bringing robust ILM capabilities to the table.
With easy enrollment via directory integration, organizations can seamlessly sync user data from platforms like Microsoft Active Directory (AD) and Azure AD, simplifying onboarding and access provisioning.
Hexnode strengthens authentication through its robust set of features. It secures user authentication through password policies, ensuring secure access to critical resources of an organization. It also provides strong governance by allowing administrators to enforce policies that manage user access and maintain compliance with organizational and regulatory standards.
Features like Hexnode Access further enhance login security for macOS and Windows devices through cloud IdP-based authentication, while conditional access restricts access to Microsoft apps based on device compliance, adding an extra layer of protection.
Hexnode offers enhanced reporting functionalities to monitor device activities and ensure compliance with data regulations, all while maintaining data security. Additionally, Hexnode seamlessly integrates with third-party applications, enabling efficient identity and device management across multiple systems while prioritizing robust data security at every step.
By integrating these features, Hexnode strengthens security and boosts operational efficiency, offering organizations a secure and simplified approach to identity management.
ILM not only helps organizations enhance their operational efficiency by automating identity management but also strengthens security by minimizing risks such as privilege creep and unauthorized access. With the current pace of digital transformation, ILM is now essential for keeping up with the security and access demands. Consequently, organizations with dedicated identity and access management will be better positioned to manage identities effectively while keeping security and compliance in check.
Check out our 14 day free trial for a comprehensive solution to your ILM and device management needs
Try out now