File encryption: A comprehensive guide
Understand the do's and don'ts of file encryption to safeguard your data effectively.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Aiden Ramirez
Mar 25, 2024
17 min read

Ensuring the security of your organizational data can often be the critical difference between success and failure. As Stephane Nappo once said, ‘It takes 20 years to build a reputation and only a few minutes of a cyber incident to ruin it.’ Fortunately, the IT world offers a range of tools and techniques to protect against potential data breaches, from Data Loss Prevention tools to Data Encryption techniques. Today, we’re going to delve deep into the latter, aiming to better understand the ‘what’s, why’s, and how’s.’
Data encryption may not be the easiest concept to grasp, but it’s an essential part of safeguarding your organization’s sensitive data. At its core, data encryption converts data into an unreadable format, ensuring that only individuals with access to a secret key can read it. Furthermore, encryption can be applied to both data at rest (data stored on an internal or external storage device) and data in transit (data being transferred over a private network or the internet).
As we touched on earlier, encryption works its magic by turning sensitive data into cipher text. But here’s the million-dollar question— why should you care about it? Well, imagine this scenario: your laptop is stolen, and your files aren’t encrypted. In such a situation, the thief can easily access all your information. The thief can simply boot your device with a USB drive and access your disk, even without knowing your password. Therefore, it’s a good practice to encrypt your sensitive data, if not your entire hard drive.
In addition to protecting your privacy from cybercriminals and other threat actors, encryption can also assist you in achieving regulatory compliance. Many industries and governments have established rules, such as GDPR and HIPAA, that require organizations to encrypt and protect all personally identifiable data. Adhering to these regulations is much more easier when you have a robust data encryption system in place.
There are different types of encryption techniques available, but most of them can be classified into two distinct categories: symmetric and asymmetric. Let’s explore each of them.
Also known as private-key cryptography, this encryption technique employs the same key for both encryption and decryption. The movie ‘The Imitation Game’ actually does an excellent job of explaining how symmetric encryption works. Symmetric encryption is typically used within closed systems. If used in open systems with multiple users, this technique requires both the sender and receiver to have access to the same key. Therefore, there is a possibility of third-party intrusion, which can compromise your organization’s data. However, on the plus side, symmetric encryption is faster than its counterpart.
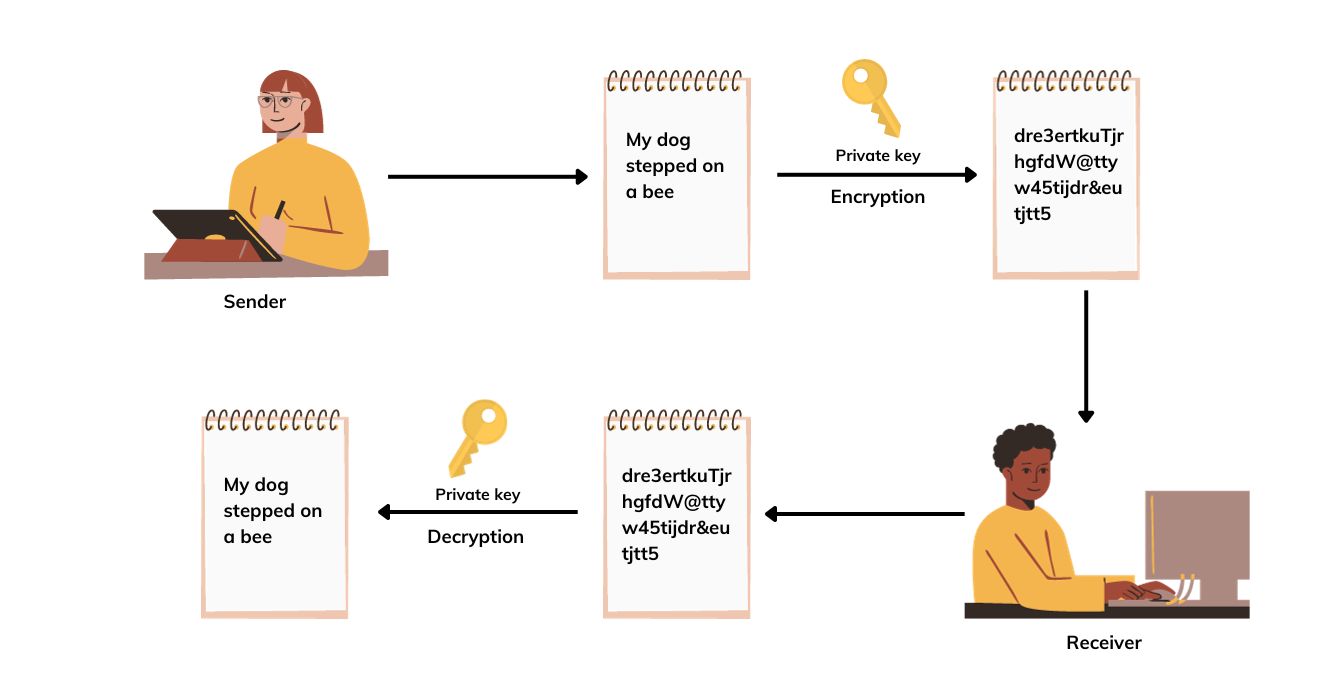
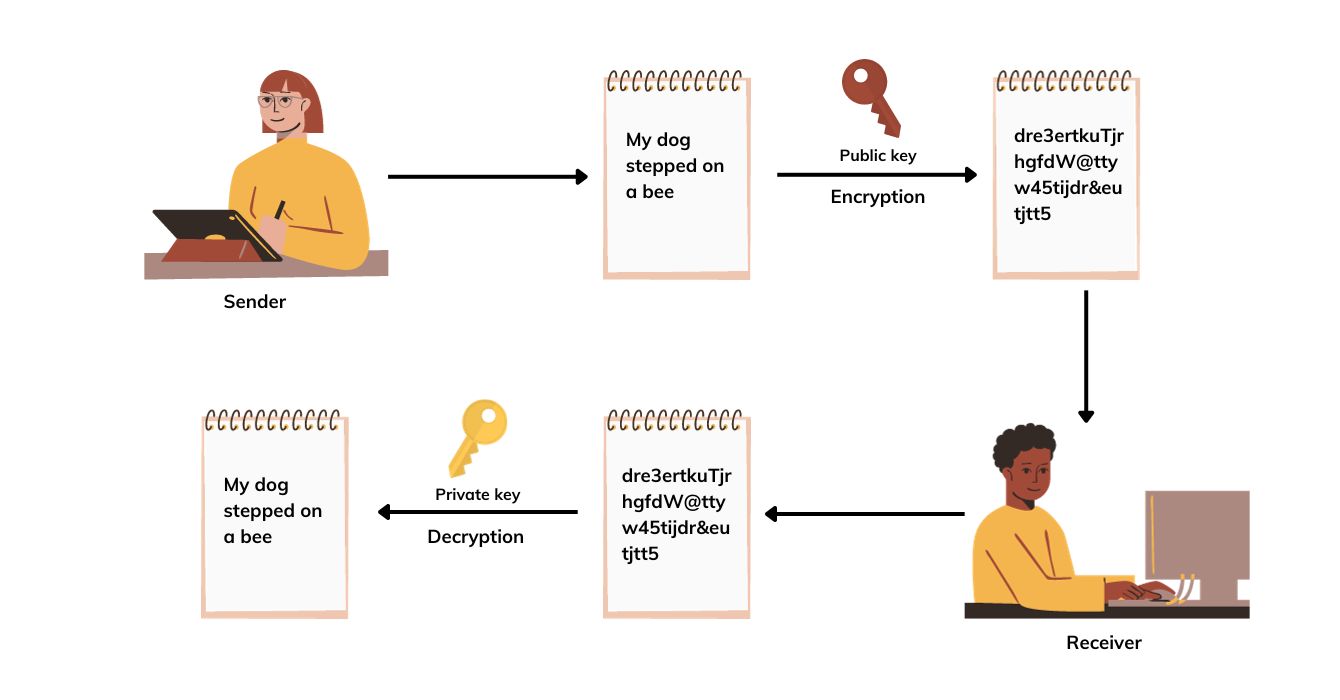
This method is also known as public-key cryptography. Unlike symmetric encryption, this method uses two keys for the encryption process: a private key and a public key. Although not identical, these two keys will be mathematically linked. In this method, the public key is used for encryption, and the private key is used for decryption. One important point to note is that the encryption key cannot be used for decrypting, and vice versa.
Hashing is the process of generating a unique fixed-length signature, known as a ‘hash,’ for a given dataset. The hash typically appears as a string of characters. Hashing distinguishes itself from other encryption methods in two ways:
Taking these characteristics into account, we can conclude that hashing is not precisely encryption; rather, it functions more like a fingerprint for the provided input. For this reason, hashing finds applications in areas such as password storage, database indexing, and data compression.
An encryption algorithm refers to the technique used to transform plaintext into ciphertext. It involves performing mathematical operations on the plaintext using a unique key to produce the encoded output. And so, selecting the appropriate encryption algorithm for your business use case is crucial because each one comes with its own set of benefits.
The Advanced Encryption Standard (AES) is a widely adopted symmetric encryption algorithm utilized for data security. AES was established as a standard by the U.S. National Institute of Standards and Technology (NIST) in 2001 and remains a trusted standard within the U.S. government.
AES offers various key lengths, including 128-bit, 192-bit, and 256-bit keys. Longer key lengths enhance security but may demand greater computational resources. This encryption method is commonly employed for disk encryption (e.g., BitLocker), and file encryption. It also stands out as the preferred encryption algorithm for securing web traffic due to its high level of security, efficiency, and extensive support compared to other algorithms. Furthermore, AES plays a pivotal role in securing sensitive data stored in databases and cloud services.
Triple DES (3DES) is a symmetric encryption algorithm based on its predecessor, the Data Encryption Standard (DES). While DES algorithm is a symmetric-key block cipher that uses a 56-bit key, 3DES offers support for three key lengths: 56 bits, 112 bits, and 168 bits. These key lengths are attained by applying DES encryption three times consecutively. Although 3DES still finds applications in several legacy systems, it is now slowly being decommissioned and replaced by AES. The shift is primarily driven by the diminished security provided by the 56-bit key in comparison to the demands of today’s security standards.
RSA, which is an asymmetric encryption algorithm, is considered to be a fundamental building block of modern cryptography. It is commonly used in secure email (PGP/GPG), secure messaging apps (e.g., Signal), digital signature encryption, and also in some web traffic encryption systems. RSA is considered highly secure when used with sufficiently long key lengths. For example, 2048-bit or 3072-bit keys are the most used ones in RSA today.
ECC is another asymmetric encryption algorithm renowned for its robust security despite relatively short key lengths. To put it into perspective, a 256-bit ECC key offers a level of security roughly equivalent to that of a 3072-bit RSA key. ECC finds broad application in various scenarios, including HTTPS (for web security) and TLS/SSL (for email and online transactions).
Blowfish is a symmetric encryption algorithm recognized for its speed and efficiency. It partitions messages into 64-bit blocks and encrypts them individually, leading to a faster encryption process. Nevertheless, it falls short in terms of security when compared to more contemporary encryption algorithms like the Advanced Encryption Standard (AES).
We’ve seen how encryption can be classified based on the encryption method and algorithm. Apart from these, we can also classify it based on the data it encrypts. Let’s take a quick look at that as well.
Full-disk encryption (FDE), also referred to as whole-disk encryption, secures all the data stored on a storage device. Think of it as placing a lock on your hard drive or solid-state drive (SSD). With FDE, every bit of data on the disk is automatically encrypted, including the operating system, system files, applications, and user data. This is achieved by dividing the disk into fixed-size blocks and encrypting each block using a symmetric encryption algorithm, such as AES.
The encryption key employed in FDE is typically derived from the user’s password. Once the user authenticates, the encryption key is decrypted and utilized to access the operating system and disk contents. Operating systems provide built-in encryption tools like BitLocker and FileVault, which enable you to implement full-disk encryption on your devices.
It’s important to note that ‘full-disk encryption’ differs slightly from ‘device encryption.’ Device encryption is a broader concept encompassing various encryption techniques applied to devices to safeguard data. This can include full-disk encryption and other encryption forms, depending on the context. However, in the mobile device domain, particularly in Android and iOS, ‘device encryption’ is the more commonly used term compared to ‘full-disk encryption.’
File-based encryption, often referred to as file-level encryption, is a method used to encrypt specific target files and folders rather than encrypting the entire disk or device. In this approach, each file can be encrypted with a separate key, which means that the files remain encrypted even after the device is unlocked.
File-based encryption (FBE) is faster and places fewer demands on system resources compared to full-disk encryption because it only encrypts and decrypts files when necessary, rather than the entire disk. To implement FBE, you’ll typically need to rely on third-party tools, as native tools usually provide only full-disk encryption.
In contrast to the encryption methods discussed earlier, end-to-end encryption (E2E) primarily pertains to data in transit. Its purpose is to ensure the confidentiality of digital communications, such as messages, voice calls, or file transfers. With E2E encryption, data remains encrypted from the sender’s end until it reaches the receiver’s end. E2E encryption can employ symmetric encryption, asymmetric encryption, or a combination of both.
When people think of end-to-end encryption, WhatsApp often comes to mind. WhatsApp, in fact, utilizes asymmetric encryption to secure digital communication on its platform. Each user’s public key is stored on a server, while the private key remains solely on the user’s device. This setup allows users to send messages to anyone by fetching their public key from the repository. Only the intended recipient would be able to decrypt the message with their private key.
Choosing and implementing an encryption tool for your organization depends greatly on your specific use case and the level of sophistication you aim for. If you work in an organization that deals with vast amounts of sensitive data spread across multiple devices, it’s advisable to opt for an encryption tool that offers robust security features. These features may include secure key sharing, key management, and audit logging. Fortunately, there is a wide range of third-party tools available to cater to these requirements. Notable options include the Advanced Encryption Package (which supports 17 encryption algorithms), AxCrypt (enabling file and key sharing), and VeraCrypt (supporting multiple encryption algorithms), among others.
Conversely, if you’re part of a small to medium-sized business or an individual—representing the larger demographic—your encryption needs may not demand the advanced sophistication of the tools mentioned above. You might be seeking tools that are relatively straightforward in terms of complexity and cost while still capable of encrypting local drives. Fortunately, most popular operating systems offer built-in tools that meet these criteria. Let’s take a quick look at some of them:
Windows offers you two options to encrypt your device: Device Encryption and BitLocker. The Device Encryption feature is available on every Windows edition as long as the device has a TPM (Trusted Platform Module). With this feature, you can encrypt your system and secondary drives completely. It doesn’t give you the flexibility to exclude a specific disk or partition. Still, it’s better than having no encryption at all.
On the other hand, BitLocker is another full-disk encryption tool designed for Windows devices. It utilizes the AES algorithm with 128-bit or 256-bit keys for encryption. Unlike Device Encryption, BitLocker allows you to encrypt either a single drive or all drives based on your specific requirements. Additionally, BitLocker provides a suite of management tools to enhance data security. It’s important to note that BitLocker is available exclusively on Windows Pro, Enterprise, or Education editions.
FileVault 2 is a proprietary encryption tool available on all macOS devices. In the past, the legacy FileVault software, introduced alongside OS X 10.3 Panther, only supported the encryption of a user’s home directory. However, Apple later launched FileVault 2, which can encrypt the entire OS X startup volume and not just your home directory. Moreover, serving as a full-disk encryption tool, it utilizes the AES encryption algorithm with a 256-bit key.
FileVault is not activated by default when you purchase a new macOS device. You must manually enable it from System Preferences. You have the option to store the recovery key either on your iCloud account or locally on a secondary storage device. However, cybersecurity experts advise against storing it in iCloud, as it can potentially make your data susceptible to social engineering attacks.
iOS uses encryption by default under the name Data Protection. Your data is protected with the device passcode, meaning that Data Protection is only activated when you set up a passcode for your device. It also uses the device’s UID (Unique Identifier) number along with the passcode to encrypt the data. So, an attacker can only try to brute-force the password on the device itself. They can’t remove its storage and connect it to another device to access the data.
Apple has also announced Advanced Data Protection for iCloud, protecting data in transit. This feature uses end-to-end encryption to provide the users with a high level of cloud data security.
Android provides users with two encryption options: full-disk encryption (FDE) and file-based encryption (FBE) on its devices. FBE is available in all Android versions released after Android 7.0. However, FDE is supported only in Android versions ranging from 5.0 to 9.0. It was discontinued in the newer versions as it restricts most of the device functionalities when users reboot their devices.
File-based encryption introduces two storage locations for the device applications— Device Encryption (DE) storage and Credential Encryption (CE) storage. While the former is available to apps right after Direct Boot, the latter is available only after the user has unlocked the device. This segregation also makes work profile containerization possible, as it allows the protection of more than one user at a time.
You should always be careful before starting off with your encryption journey. Remember, your device doesn’t have a brain. So, you should use your own. Here are a few tips to help you;
Choosing an encryption methods is like picking the right tool for the job. There are different types, and you should select the one that matches your use case. Some are super secure but slower than a sleepy sloth, while others are quick but not as strong as the others. So, figure out what suits your data type, size, and what you’re trying to protect.
Your data is precious. Whether it’s chilling in your storage drives (at rest) or zipping through networks (in transit), it needs protection. Encrypting both ensures that even if someone tries to mess with it, they’ll be left scratching their heads in frustration.
No matter how strong your encryption strategy is, if you lose your keys, it’s goodbye to all your data. So, it’s smart to have a backup of your recovery keys. Also, ensure you secure these backups too. You wouldn’t want to leave the spare house key under the doormat, right?
When you’ve got a bunch of devices to encrypt, trying to do it one by one will be messy and time-consuming. Having an automated encryption management system or a Unified Endpoint Management (UEM) solution can help you minimize the fuss. A capable UEM solution such as Hexnode can help you remotely configure encryption settings on your devices seamlessly.
Download the white paper to learn all about data security and how Hexnode can ensure data security in your organization.

Featured resource
Hexnode for data security: Protecting your business data with Hexnode
As we wrap up this guide to data encryption, it’s essential to emphasize that encryption is just one piece of the security puzzle. Your computer and data security need more than just encryption. There are more aspects to cybersecurity, such as network security, malware prevention, identity & access management, and so on. Integrating all these elements into your security infrastructure is vital to effectively ward off digital threats.
Stay safe, stay cyber-secure!
Sign up for the 14-day free trial to experience seamless management of your encrypted devices.
SIGN UP NOW