If you are an Android user, you will have come across apps asking permission to access different systems of your device, like camera, mic and so on. They do this because, most of the time, apps need access to such systems to function, even if it is unclear why that permission is required.
In some instances, apps might ask for permissions with malicious intent. Sometimes the intent is very evident, while in other situations, it is tough to understand whether permission is necessary or not.
- What are app permissions, and what are the different types?
- Install-time permission
- Special permission
- Runtime permission
- Workflow for app permissions in Android phones
- Why does Android runtime permission pose a threat?
- How stay away from the risks of Android runtime permission
- How can a Unified Endpoint Management solution help you in this matter?
- In conclusion,
What are app permissions, and what are the different types?
App permissions are requests made by applications to access or use different components and features of an Android device. Depending on when the application makes the request, there are different permissions.
Install-time permission
This permission allows the application to access specific restricted systems and actions. These actions have minimal effect on the system and other apps. Install-time permissions are presented to the user by the App Store when they try to install it. Install-time permissions have two main sub-categories:
- Normal permissionThis permission extends beyond an app’s sandbox and will affect other apps and the whole system. The data and actions accessible through this pose minimal threat to the user’s privacy and the functioning of other apps.
- Signature permissionThis kind of permission is only given by the system if the application making the request is signed with the same certificate as the application that first declared the permission. After that, permission will be automatically granted without telling the user if the certificates match.
Special permission
As the name suggests, these permissions are unique and are used for particular operations by particular apps. Common apps usually cannot request these permissions as they are sensitive, and user authorization is necessary to grant them. Therefore, the request process is a bit different for apps to use these permissions.
Runtime permission
Runtime permissions are the requests that pop up when you try to open an application. These permissions allow apps to access certain features and perform specific restricted actions on the device.
The system and other apps are severely impacted by the data and actions to which this permission provides access. Therefore, runtime permission’s primary goal is to stop apps from accessing users’ private data without authorization.
As mentioned earlier, Android runtime permission usually comes as a pop-up box providing the user with three options:
- Always allow: The app can always access the requested feature, even when not in use.
- Allow while in use: The app can access the requested feature only when it is running and requires that feature.
- Deny permission: The app cannot use the requested feature even if it is necessary for it to run normally.
Runtime permissions are considered dangerous permissions because the actions and data they give access can significantly affect other apps as well as the whole system. In contrast, other permissions either extend only to the app’s sandbox or have little to no effect on the system and other apps.
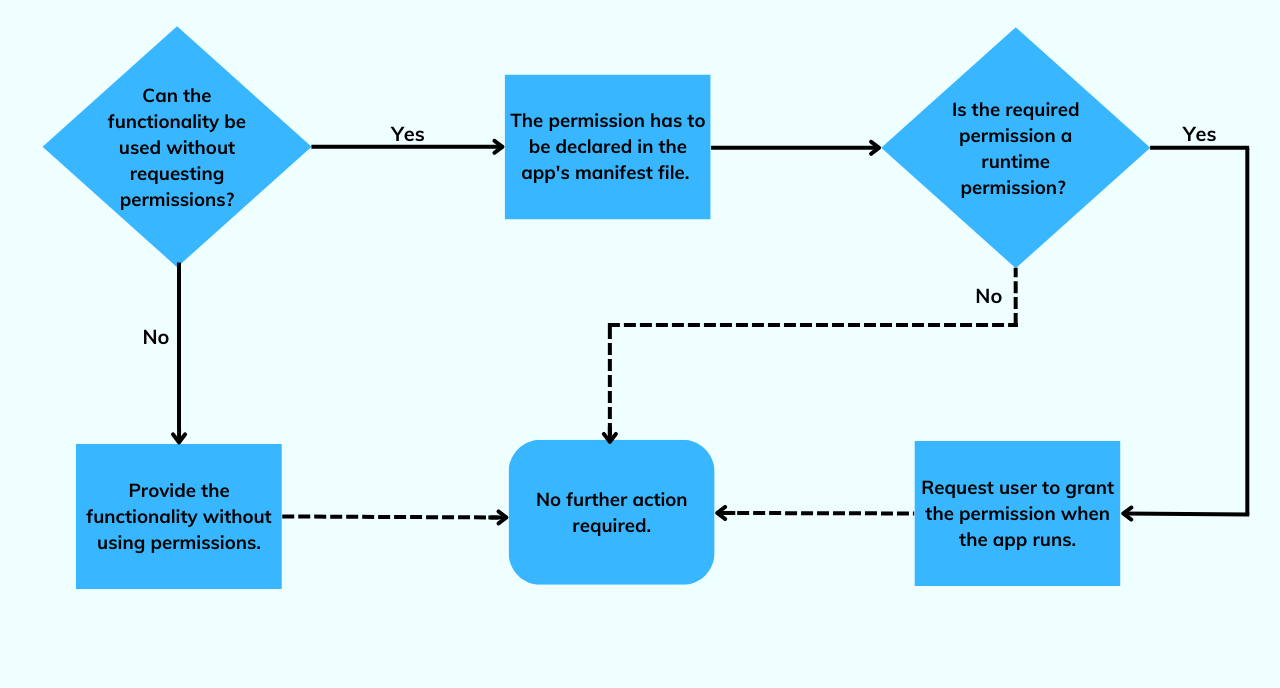
Workflow for app permissions in Android phones
For apps to offer specific functionality, they must access certain restricted data and actions. There are two options available on Android for doing this: one where the app has to request permission and one where the app can directly perform the action without declaring permissions.
If permission is required, it must first be declared in the app’s manifest file. If it is normal permission or signature permission, then no additional step is required, whereas, for runtime permissions, the application has to make a request to the user when it is run to grant access.
Why does Android runtime permission pose a threat?
Android runtime permission was created with one thing in mind: user data privacy. Even though that was the intent, a severe threat was hidden underneath. If malicious apps are granted access to these dangerous permissions, the data can be compromised, and the malicious entity can do restricted actions on the device.
Depending on the permission granted, the severity of the threat might vary. For example, if a malicious app is given access to the network state permission, then the app can download malware on the device and send an SMS to the device. Also, they can modify the connections; these malicious connections drain the battery and data really fast.
Some of the other commonly exploited permissions are:
- SYSTEM_ALERT_WINDOW – Apps can use this to display false and fraudulent ads over other apps and inject ransomware that causes persistent screens.
- Full internet access – Malicious apps can use this to make unwanted internet connections and download malware on the device.
- Modify/Delete SD cards – This permission can be abused by hackers who save copies of the information they’ve stolen or files before transferring them to the command center. Unsurprisingly, malicious software can even remove images or other files from the SD card.
Concerns over privacy must also be addressed here in addition to all of the other threats. Sensitive information can be made public once it is in the hands of hackers, which is a major setback to the privacy of personal data. However, governments have addressed the importance of data privacy and have imposed strict rules like GPDR.
How stay away from the risks of Android runtime permission
When it comes to businesses and other organizations, they must make sure that each and every employee stays safe online. IT admins can take some of these measures to make sure that employees are protected from the threats of Android runtime permission:
- Be careful while pushing an app: Employees frequently ask IT administrators to push new applications to their devices. IT administrators must ensure that these apps are safe to use and only come from reputable sources, such as trustworthy app stores or trusted developers, before deploying them to devices.
- Set up permissions before device deployment: One thing an IT admin can do is install essential apps on work devices and set up permissions way before the devices are deployed to the employees.
- Blacklist unnecessary apps: IT admins can restrict employees from downloading and installing unnecessary apps on their devices. This way, no malicious application will find its way into corporate devices and boost productivity.
- Verify the permissions of any custom apps before deploying them: Many organizations seek out independent developers or companies to create apps that are specifically catered to their needs. When distributing these custom apps, make sure that all of the permissions they ask for are necessary. If you have any questions about the app permissions, contact with the developer to get clarity regarding it.
- Constant device monitoring and auditing: Regular device monitoring and app auditing can help admins determine if any threats have found their way into the corporate devices and ensure that all apps are working as intended.
Now you might wonder, is it worth spending this much time downloading an app? The short answer to this would be prevention is better than cure. The repercussions of data breaches are more significant when compared to the investment you make to secure your data.
So, think about it, do you want to spend a few extra minutes or hours researching an app or do you want to spend days picking up the pieces after a data breach?
How can a Unified Endpoint Management solution help you in this matter?
Deploying, configuring and managing apps on corporate devices is a time-taking task for IT admins when done manually. This is where a UEM like Hexnode can help you. Apart from just distribution and managing, you can also configure app settings and permissions.
You can configure permissions for apps remotely from the management console and either allow or deny them. Once the configuration is applied, the app will function even if specific permissions are denied. Also, the app will not prompt the user to configure the permissions. As a bonus, the user won’t be able to modify the permissions through settings.
Featured resource
Hexnode Android Management Solution
Download the datasheet to learn how Hexnode’s Android Management solution helps businesses ensure seamless deployment, configuration, regulation, monitoring, and supervision of end-user devices.
Download datasheetHexnode also lets you blacklist apps that employees should not use, so no known malicious apps would be installed on the devices.
Using Hexnode, you can remotely monitor and audit all devices in an organization from a single console. This can help IT admins figure out if there is something wrong with the devices. Remote troubleshooting is also possible with Hexnode.
In conclusion,
Created with great intention, runtime permissions are now a huge risk to Android devices. Even though Android came up with solutions to secure your devices from the risks of runtime permissions, cyber-attackers are finding newer methods to exploit this feature. Being careful and using security tools like Hexnode is your best option to take care of your corporate Android devices.
Sign up for a free trial
Sign up for a free trial with Hexnode and see how Hexnode can help you manage your Android devices.
Sign up




