Have you missed Day 2 of @HexCon22?
Don't worry!! We've got your back. Visit this blog to see what you missed on Day 2.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

HexCon22 has officially concluded. As much as it aches to see the event end, we are glad to be a part of HexCon22.
We’ve got some fantastic highlights coming up for you, including talks on cybersecurity, incident response, data protection, and more. Many of our speakers used their experience to give insights on what organizations need to know about keeping their people, devices, and networks safe and secure.
Here’s a short rundown of what happened on the final day of HexCon 22:
Lesley Kipling, Chief Cybersecurity Advisor at Microsoft, talked about cybersecurity and introduced us to a concept called “Just Culture” at HexCon 2022. She explained just culture as a supportive and encouraging culture where employees report issues without the fear of losing their job.
She believes that rewarding those who report is preferable to punishing those who do not. It contributes to the organization’s “Just Culture.” Moreover, she feels that identity protection is critical, and that attitude lies at the foundation of the zero-trust strategy. She urged everyone to utilize authentication rather than passwords, as it makes life more difficult for attackers. Sadly, after an incident, most people play the blame game. She highlighted her dissatisfaction with the way security is blamed when a breach happens, as if IT is the only department that suffers when a breach or hack occurs. The session was concluded by recommending corporations to see security as a business risk.
“Work is something you DO, not a LOCATION”.
Bil Harmer, Operating Partner of Security, Craft Ventures started the session with this statement. Technology is no longer the sole domain of technologists. He additionally mentioned that it is due to BYOD and the present work environment.
Bil also discussed the Snowden effect. When Snowden disclosed massive passive surveillance, the world witnessed a major demand for data encryption.

It is also critical to be aware of Business Email Compromise (BEC). The FBI currently ranks BEC as the top crime. It was further revealed that over $43 billion in losses had been recorded. Malware as a service is rapidly expanding these days. The platform offers criminals tips on how to personalize ransomware demands as well as the possibility of translating the malware into several languages.
Jaye Tillson and John Spiegel, Directors of Strategy and Network Transformation at Axis Security, used the HexCon22 platform to explain down the notion of ‘Zero Trust’ for all of us. They discussed the Security ServiceEdge forum, its objective, and its purpose. To understand more about zero-trust, they interviewed its founders. They discovered that zero-trust is a concept, not a technique, and advised us to never trust and always verify.
Both of them feel that, even if the world has changed, zero-trust is still as crucial as it was before. They discovered the importance of knowing your business. It’s not only about technology; it’s about people as well.
Fighting cyber-attacks is a difficult struggle that everyone agreed on. As a result, we must educate everyone on it, not just the IT crew. They further claim that the inventors of zero-trust were the first to notice that IT had a major security problem. The discussion concludes with the realization that the existing solutions will no longer work in the future.
As global connection and cloud service usage grow, so does the danger of cybercrime. Traditional data security procedures may no longer be sufficient. Simon Newman, Interim CEO of the Cyber Resilience Center for London, spoke about cybercrime and security resilience in his session.
According to him, cybercrime is on the rise and is likely the fastest-growing crime. Businesses are less capable of detecting breaches than they were five years ago, which concerns Simon. Globally, conviction rates for reported attacks are exceedingly low. This presents a hurdle to law enforcement. Simon closes the session with some simple precautions to take to keep safe, such as:Have you ever seen an AI digital twin of a speaker deliver a session? That’s exactly what happened here! As AI algorithms have access to more data, replacing old methodologies with AI can improve threat detection and reduce cybersecurity issues. Igor van Gemert, CEO of Learnmetaverse.today, who is well-known for his revolutionary technological proposals, simplified it for us.

The entire session was divided into two parts. Initially, he discussed reducing cyber dangers and events. Later, the operational technology in the industry area was explored. The explanation by him for threat hunting was also shocking. The future of threat hunting lies where machine learning automates analysis and model building using algorithms that enable organizations to proactively search for advanced threats through big data.
Igor also demonstrated supervised and unsupervised machine learning, as well as their outcomes, using basic examples. Thousands of employees operate across the world at several global secure operating centers to reduce digital hazards for us. He concludes by describing how AI is used in cybersecurity applications.
Kimberly Simon, VP of Marketing & Strategic Partnerships at ControlCase, discussed cybersecurity methods and how compliance may assist. She began by outlining who is the target of all cybercriminals. If we are ignoring cyber security, we are costing the company.
The speaker also identified phishing and compromised credentials as the top two first attack routes. She indicated that most of the work was spent identifying and containing stolen or compromised credentials.
Kimberly distinguished between two sorts of compliance: security compliance and privacy compliance. She also talked about many key facts, including:
According to recent research, it is reasonable to conclude that remote work is here to stay. Burton Kelso, a tech expert, speaks to HexCon participants on smart ways to manage enterprises remotely and safely. It is critical to ensure that when working remotely, you are taking precautions to protect yourself from cyber criminals.
Some of the most serious hazards to remote employees include:

More than 99% of cyber-attacks rely on human interactions. The speaker concludes by suggesting ways to be followed to keep you safe from cyber criminals. They are:
The cybersecurity skills gap is a reality, and bridging it requires understanding the underlying reasons for the shortage. Codrut Anderie, a cybersecurity leader, analyzes if it may be considered an acceptable business risk. Cyber risks must be controlled and prevented since they harm not just organizations and their data, but also human rights and lives.
A very complex issue that has arisen in the current circumstances is that, while there are many positions available, the recruiting criteria are also equally high. He also feels that the requirement of extensive certifications for an entry level position makes it harder for people to enter the field. This issue puts additional strain on current cybersecurity professionals, who must handle everything in the end.
The speaker was successful in changing the listener’s perspective about cybersecurity skill gap. He closes the session by saying,
“Cybersecurity professionals help and protect society. As a result, we require them in the same way that we require doctors, engineers, teachers, and any other professions.”
Dejan Draguljevic, Senior Executive VP of Business Development at Pradeo, offered realistic proposals for detecting mobile threats and improving the worldwide security of information systems. He commenced his session by discussing the latest relevant news on cyber-attacks and phishing. Hence, an extensive knowledge of the unified endpoint structure is required.
Our mobile devices will be linked to our IT system, from which hackers will attempt to obtain as much information as possible once compromised. The three primary areas in which the hacker attempts to attack. It includes the operating system, the network, and the applications.

Dejan ended the session by demonstrating the smishing attack, phishing and spyware. He also highlighted how Pradeo can be integrated with Unified Endpoint Management.
While many organizations allow employees to use personal devices, there is uncertainty within policies and awareness-raising activities. Furthermore, even with business-owned devices, there may be major gaps in whether businesses can manage their devices and whether support personnel are adequately trained. Steven Furnell, Professor of Cyber Security at the University of Nottingham, led us through an informative presentation on device management.
His session provided the following significant takeaways:
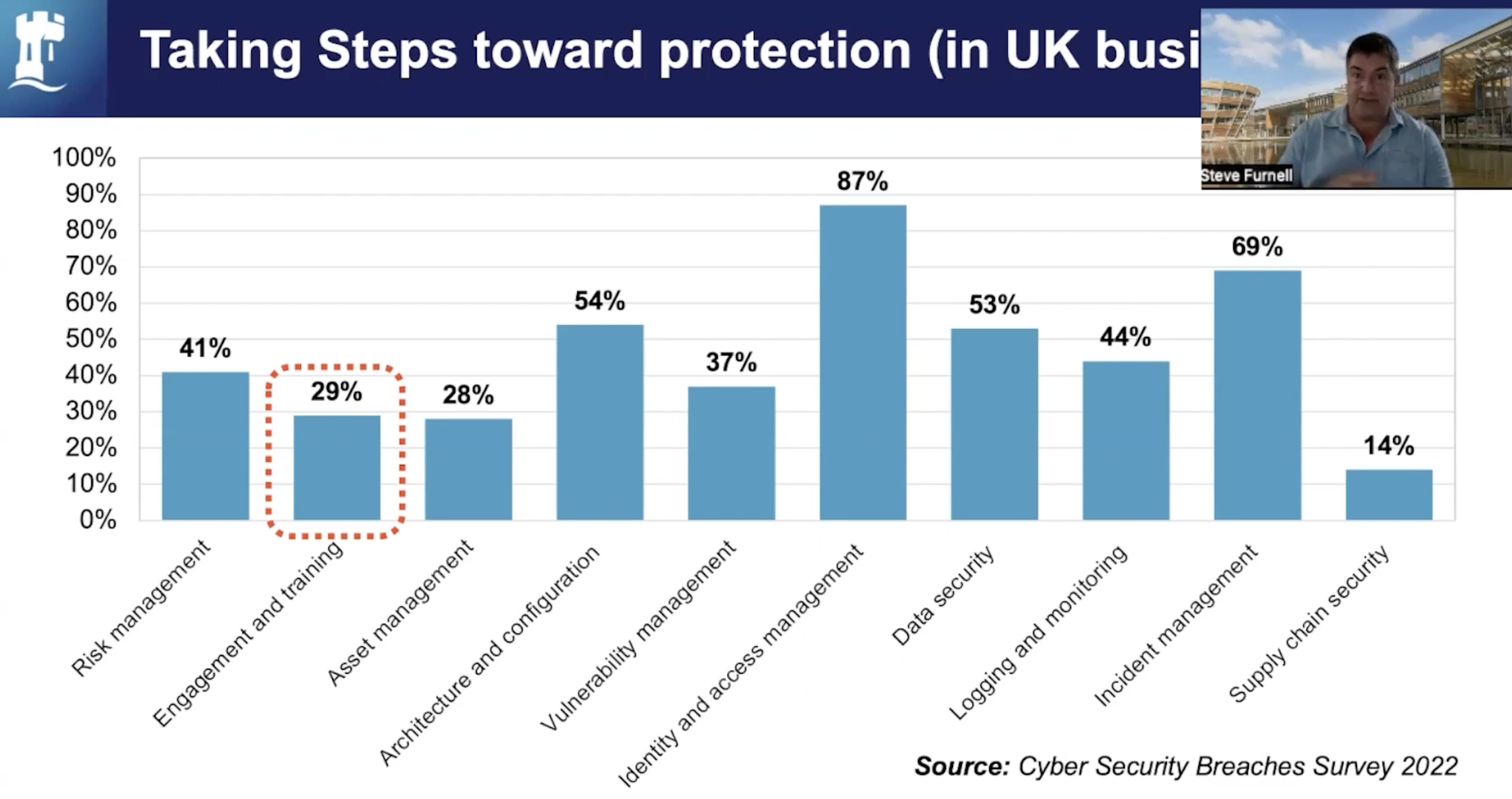
Most users are unsure of what to do; they require a policy to guide them, as well as public awareness to support the policy. He concludes by stating that diversity must be skillfully handled, that technology may make a substantial contribution, but that technology alone is not the answer.
Enterprises and organizations worldwide struggle with the handling of cyber-risk and its role in enterprise risk management. John Giannakakis, Co-founder of G+P Law Firm shares his thoughts on the inclusion of cyber-risk in enterprise risk management frameworks, stating that it should be at the forefront of consideration when setting up enterprise risk management frameworks.
Quoting ex-FBI Robert Mueller: “There are only two types of companies: those that have been hacked, and those that will be.” He went on to pinpoint a few examples of major cyber threats, as defined by the NCSC (National Cyber Security Centre) of the UK.
Mr. Giannakakis continued to dive into the realm of risk management and how cyber-risk can be mitigated by enterprises worldwide. As well as detailing some common problems faced by enterprises during cyber-risk management, he also made clear distinctions between risk impact and risk description.
From a legal standpoint, Mr. Giannakakis educated viewers on some major problems faced by companies during cyber-risk management, while providing clear definitions which should be taken note of during enterprise risk management. He concluded his session by advocating cyber-risk to be a key factor within any organization’s enterprise risk management framework.
Promoting cyber-hygiene is the number one thing every small and medium-sized business owner must do to become more cyber-secure. The same point has been echoed by Cybersecurity Evangelist and Amazon.com bestselling author Donald Allen. Even today, there are people who underestimate the impact of being lax with cybersecurity and how it can impact personal and enterprise data. Cyber-hygiene is becoming as important as any other mundane routine in our daily lives.
“Cyber-security is not just a technological problem – it is a human problem too.”
Donald went on to state that cyber-hygiene is a C-Suite priority. Employees of an organization follow the example set by the C-Suite – if the leadership do not practice good hygiene, the same would pass to the rest of the organization.

With more than 8 years experience in Information security and technology, Fatma Al Lawati, IT Governance, Risk Management and Compliance Assistant Manager at Oman Air, talks about the need to strike a balance between data privacy and trust, by combining security and convenience.
Fatma kicked off the session by introducing the ‘privacy paradox’ – A person’s intention to protect their online privacy, vs. how they behave online, compromising their privacy. Giving some examples from real life Fatma highlighted some of the methods by how privacy is compromised online.
With more than 20 years of experience providing Integrated Risk Management (IRM) SaaS solutions to clients in 120 countries across various industries, Mathieu Gorge, CEO and Founder of VigiTrust, talked about the steps to be taken when cyberthreat is heightened.
He stressed how the attack surface is rapidly growing and the need for strong worldwide data protection and privacy regulations. Mathieu highlighted the global risk landscape and described the geopolitical impacts on the tensions between Russia and Ukraine.
He talked about how risk professions can talk to the key decision makers to enforce the 5 pillars of security.
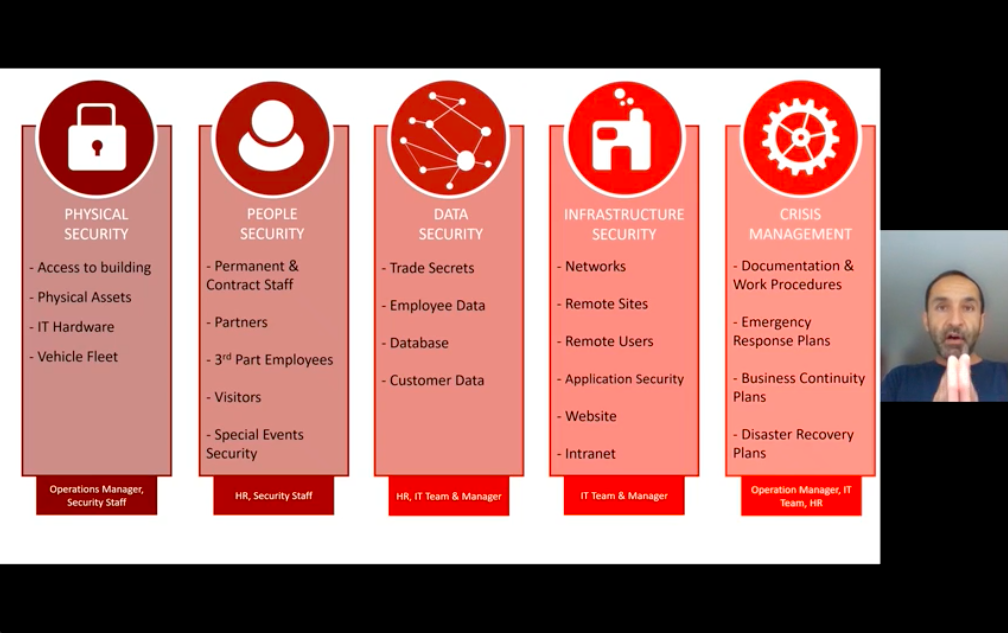
With 25 years of experience in the security industry, Joshua Belk, Co-Founder and Tech Psychologist at OPSEC360, explains the do’s and don’ts of work-life balance using examples from his own life.
He begins the session by highlighting how remote work and distributed teams are in the mainstream, and job security is weak. In such a scenario, Joshua outlines the steps you need to take to take care of yourself, and your career.
Regardless of priorities, the one thing we have that is all equal to everyone is time.