Back in the old days, maintaining one’s identity in the enterprise was as simple as setting up a username, and associating a password with it.
Fast forward to today, times have changed. Businesses can no longer rely on the old-fashioned and error-prone processes to assign and manage user privileges. Instead, we rely on ‘automation‘ to take over these tasks, thereby reducing the load on IT to maintain an expanding database of identities, and manage their corresponding levels of access. And this, is the foundation over which an identity and access management solution operates.
What is identity and access management?
Identity and access management (IAM) in the enterprise, refers to a businesses’ ability to manage identities and define the roles and access that individual users (and devices) are entitled to in an enterprise network. This in turn, facilitates the user’s/device’s access to corporate resources within the company’s cloud/on-premise infrastructure.
Or, as the people at Gartner would like to say,
Identity and access management (IAM) is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.
Now, on closer examination, the core functionality of an identity and access management strategy can be derived from the two terms it incorporates. Identity management, and access management.
Let’s take a closer look at these two terms.
Together, they make up a single solution termed ‘identity and access management’.
What is the purpose of IAM?
In today’s distributed business environment, your employees and customers exist globally, and at least some (if not all) of your corporate infrastructure resides in the cloud. As a result, phishing, spoofing and other social engineering attacks have become significant threats to enterprise security. Identity thefts have increased twofold, and enforcing strong usernames and passwords just won’t cut it anymore.
Your business must be ready with a proper solution to validate employee credentials and regulate their access to corporate resources, all the while ensuring that the least possible time is wasted through the authentication process. Identity and access management frameworks aim to accomplish just this.

IAM equips IT with the ability to secure and maintain your employees’ identities, while also controlling their access to sensitive information within the corporate network. With IAM, employee access can be limited to just the tools and resources required to carry out their specific tasks.
Moreover, regulatory guidelines such as the Health Insurance Portability and Accountability Act (HIPAA), hold businesses accountable for managing access to customer and employee information. In addition, the General Data Protection Regulation (GDPR) mandates that organizations safeguard the personal data and privacy of European Union citizens and businesses. With the help of identity and access management solutions, organizations can ensure that their workflows and processes comply with these regulations.
How does identity and access management work?
On a fundamental level, identity and access management solutions are designed to accomplish three key functionalities: identify, authorize, and authenticate.
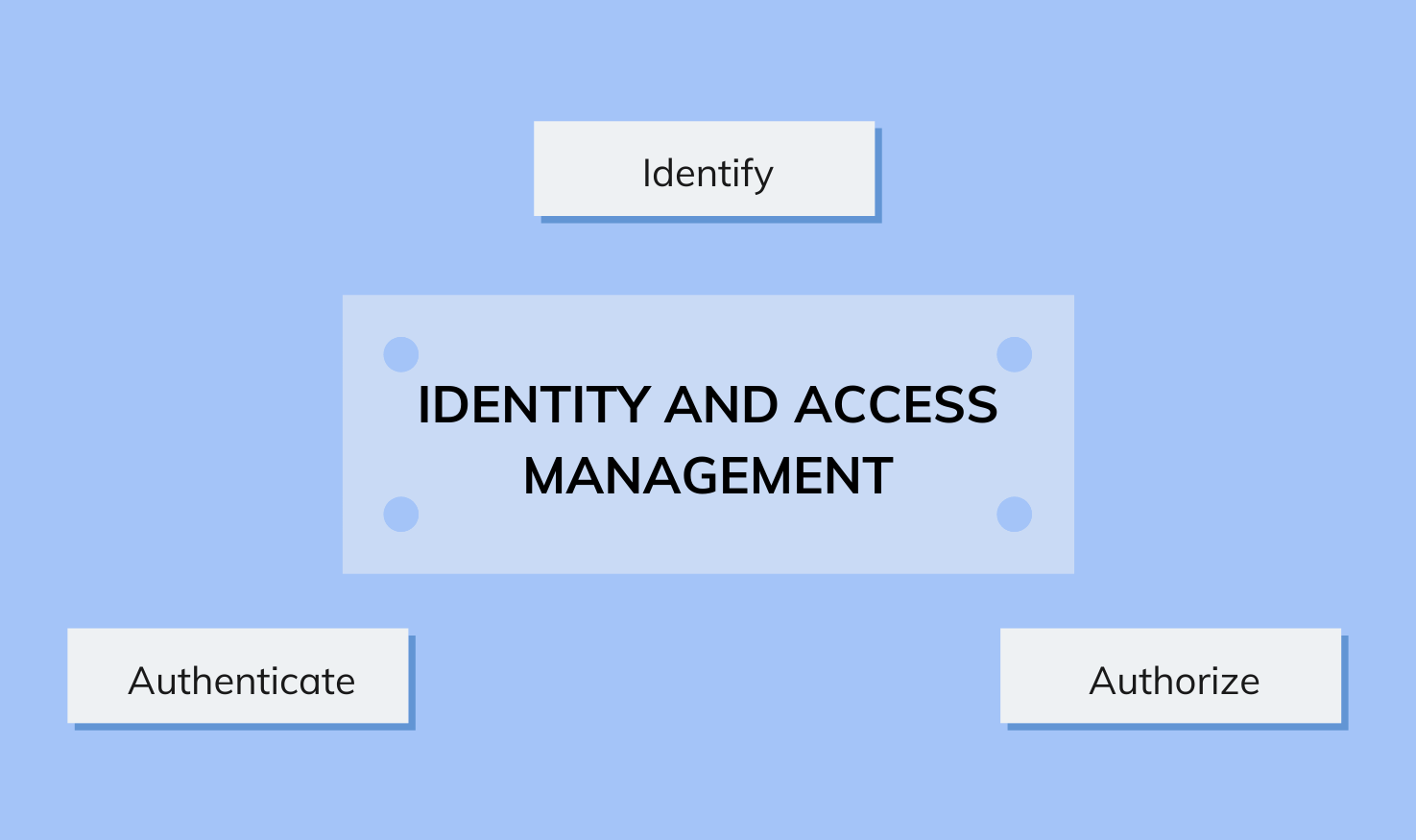
- Identify: Maintain and manage a directory (or repository) containing the attributes, characteristics, and specifications of entities (users and devices) within a system. This includes adding, removing and updating individual entities and their roles within the system.
- Authorize: Assign roles and privileges to individuals or groups of entities in the network, and grant them permission to access the required corporate resources based on their level of authorization.
- Authenticate: Protect sensitive data within the system, and secure corporate infrastructure by enforcing measures to authenticate users and devices that attempt to access the enterprise network.
The methods and tools used by an IAM solution to fulfil the three functionalities mentioned above include,
However, today, identity and access management solutions oftentimes incorporate additional tools and functionalities, including biometrics, Fast Identity Alliance (FIDO), adaptive MFA, machine learning and artificial intelligence, risk-based authentication, zero-trust network security, and more.
Moreover, identity and access management can be handled in the cloud by employing the help of third-party service providers – This process is called Identity-as-a-Service (IDaaS).
Identity and access management with Hexnode UEM
Hexnode offers a robust suite of identity and access management functionalities, empowering businesses to provide seamless access to corporate resources with minimum downtime. In addition, by implementing a central identity management platform, Hexnode enables you to enforce advanced security policies in the enterprise, all the while maintaining regulatory compliance requirements.
Hexnode’s IAM functionalities

Enforce authentication
Passwords are the first line of defense for any IAM strategy. Prevent potential identity thefts and malicious attacks by enforcing strong password policies in the enterprise, and implement additional restrictions on password complexity, tries after device wipe, password history and age, and more.
Enable multi-factor authentication (MFA) as an additional verification technique for securing all the sensitive data that a corporate user can access. Hexnode enables third-party authenticator apps such as Google Authenticator and Microsoft Authenticator to secure access to the management portal by enabling MFA.
Overcome the need for memorizing complex passwords by supplementing passwords with suitable certificates that you can deploy to your end-users. Store certificates in the Hexnode portal and deploy them to your managed devices.
Maintain and manage employee information and ensure secure access to user data with Hexnode’s seamless integration with Microsoft Active Directory (AD) and Azure Active Directory (Azure AD).
Hexnode’s integration with Okta enables organizations to easily manage access to corporate resources and apps. Businesses can securely onboard devices to Hexnode with Okta directory credentials, and ensure efficient validation of identities with the help of SSO and MFA.
Maintain security
Prevent corporate endpoints from connecting to unprotected networks and remotely set up VPN configurations to secure network connectivity, by pushing Wi-Fi and VPN configurations to managed devices via Hexnode.
Hexnode enables you to containerize and secure your corporate information with the help of Work Profile for your Android Enterprise devices and Business Container for your managed Apple devices.
What is containerization and why is it important for your business?
With Hexnode, you can define compliance settings to ensure that your endpoints conform to corporate regulations and flag non-compliant endpoints. By enforcing automated and periodic compliance checks, businesses can ensure that all the necessary corporate security controls are in place.
With Hexnode, businesses can push device encryption policies to enforce system-level encryption on endpoints. This in turn, secures the critical company data from being accessed by unauthorized users.
Manage access to apps and content
Hexnode enables businesses to push application and website blacklist/whitelist policies to ensure that only the specific apps and websites that sustain corporate standards and security are accessible to users.
With Hexnode, businesses can remotely manage the permissions accessible to managed apps, thereby protecting users from potentially malicious apps.
Making your apps enterprise ready with custom app configurations
Businesses can provide instantaneous access to their required apps by configuring and deploying custom app stores. Also, IT can quickly provision app catalogs on managed devices to minimize the time wasted searching for the required apps.
The future of identity and access management
We all know what’s happened after the COVID pandemic. Remote work has become the standard for enterprises everywhere. And with more and more influx of devices, employees accessing corporate data through open networks, and the looming threat of cyber attacks, the need for a solid identity and access management solution has now become more crucial than ever.
With Hexnode’s IAM solution, businesses can guarantee data protection and efficiently meet the rising demands on regulatory compliance and data security standards in the enterprise.
Go ahead, try it out!
Reinforce your business strategies with Hexnode's Unified Endpoint Management solution
TRY IT OUT