Geofencing– Reducing corporate risks down to zero in device management
Want to know more about how geofencing can help keep you safe from corporate risks in device management? Take a detour!

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

Sitting down with a cup of coffee and scrolling the phone for the latest tidbits of technology, you can’t help but smile at how far we’ve come from the first wheel. We’ve managed to fit the world into the palms of our hands, so to speak. There was a time when we had to wait months to hear from our loved ones, but today, all we have to do is ring them up, or if we want to see them, then Skype them.
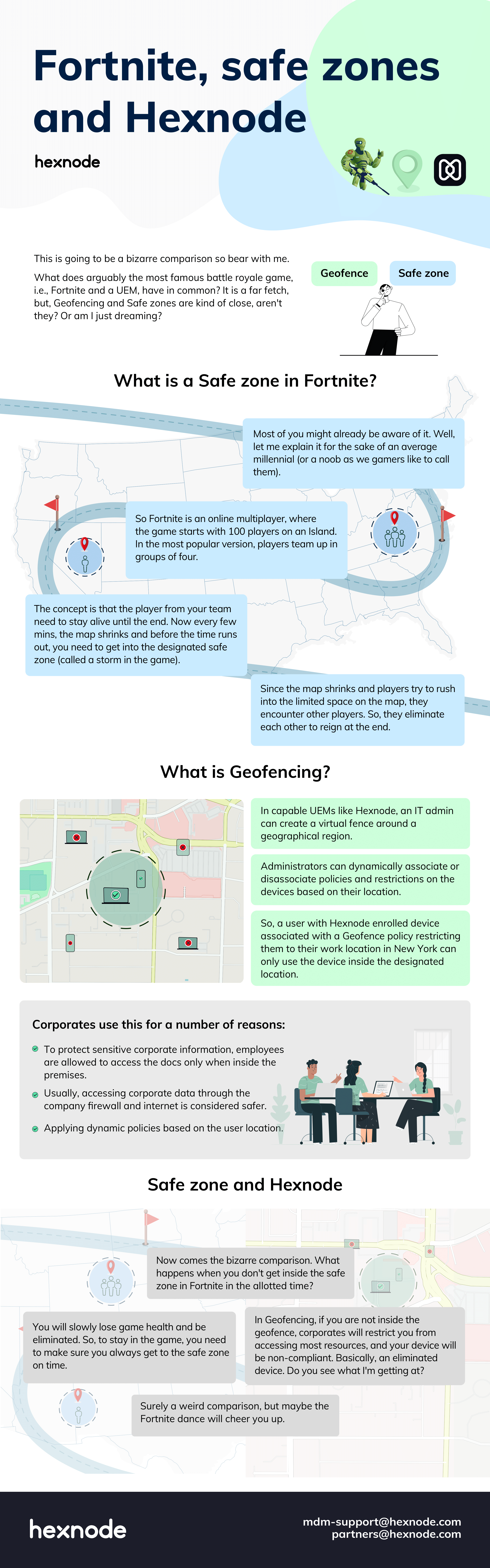
In today’s rapidly evolving technology landscape, geofencing is a powerful tool with growing significance. Geofencing is a revolutionary concept that utilizes location-based technologies to define virtual boundaries and trigger actions based on the movement of devices or users within those boundaries. Setting up these virtual perimeters enables organizations to create intelligent, dynamic systems that automate processes, enhance security, and streamline operations. At its core, geofencing relies on defining geographical boundaries using coordinates or specific points of interest. These boundaries can be as broad as an entire city or as narrow as a specific building or room.
Now for the how of geofencing. The underlying technologies that enable geofencing encompass a combination of GPS, Wi-Fi, and cellular data. GPS (Global Positioning System) provides accurate location data by utilizing satellite signals, enabling devices to determine their precise coordinates. Wi-Fi positioning systems use the signal strengths of nearby wireless networks to estimate the device’s location within a smaller, localized area. Cellular data, on the other hand, leverages the cell tower infrastructure to triangulate the device’s position.
Geofencing has gained immense traction in various industries, revolutionizing the way organizations manage devices and user access. As far as the retail industry is concerned, geofencing allows businesses to send location-based promotions or notifications to customers when they enter a specific store or area. This targeted approach can enhance customer engagement, drive foot traffic, and improve sales.
In the transportation and logistics sector, geofencing enables efficient fleet management. Companies can monitor the movement of vehicles, track delivery routes, and receive real-time alerts when vehicles deviate from predetermined paths. This not only enhances operational efficiency but also ensures better security and adherence to schedules. Geofencing also plays a pivotal role in enhancing security measures. Organizations can establish secure perimeters around sensitive areas, such as data centers or restricted facilities. If a device or user breaches these boundaries, instant alerts can be triggered, enabling prompt responses and mitigating potential security risks.
Additionally, geofencing finds its application in workforce management. Employers can define geofences around job sites or remote work locations. This allows them to track employee attendance, automate clock-ins and clock-outs, and streamline payroll processes. Furthermore, it ensures that employees adhere to safety protocols and regulatory requirements within designated areas.
At the end of the day, with geofencing, devices can be configured according to their locations by selectively enabling device functionalities at different locations.
IT administrators face numerous challenges when managing a mobile workforce. Add to it the considerations for the diverse range of platforms supporting these devices, and you get yourself one fine pickle. Well, geofencing is one powerful tool that IT admins can use to wrangle their devices into a fence of sorts to better manage and secure them.
One of the primary needs for IT administrators is granular control over device usage, security, and access. With employees working remotely or on the go, it becomes crucial to enforce policies tailored to specific locations or scenarios. For example, certain applications or data may need to be restricted within the office premises or accessible only from approved locations. Granular control ensures that employees have the appropriate level of access based on their geographical context. This is where geofencing proves invaluable. By utilizing location-based restrictions and policies, IT administrators can establish virtual fences around specific areas or define boundaries for device usage. These geofences act as dynamic barriers that trigger predefined actions or enforce policies when devices or users enter or exit designated areas.
Hexnode UEM lets you create geofences by simply dragging across the map overlay. You can create multiple geofences and conveniently name them based on their regions. Dynamic grouping allows you to choose geofencing criteria to have devices automatically moved into a group when they travel in or out of a geofence. This way, you can have all the devices with policy violations together in a single group. And then, all you have to do is use your trusty Hexnode portal to remotely lock the devices in that group. Yup, a few well-placed clicks and devices far away are locked! Pretty handy, right?
You can also drill down to individual devices and view their location history or initiate further actions, say a device wipe. Here’s a general overview of how Hexnode and geofencing work hand-in-hand to give you the best of management and security for your endpoints.
Hexnode UEM’s console provides an easy and efficient way for admins to create a geofence. All they have to do is provide a name for the geofence and select the area from the map. And thus, the selected area transforms into a geofence. Et voilà!
Dynamic groups are what the term suggests. Groups that keep changing over a periodic sync based on some condition or criteria. So technically, Hexnode UEM allows you to construct dynamic groups by setting the criteria to group the devices and the opportunity to include or exclude certain geofences. As and when the devices enter a particular geofenced area, they are added to the corresponding dynamic groups. Consequently, the policies attached to the dynamic group are also pushed onto the devices and thus trigger the corresponding actions.
If you have a chance for a do-over in device management, here’s what you should do differently
Once the policies get associated, everything else is seamless. The devices within the area can generate instant or periodic reports. And when a device leaves or enters the geofence, Hexnode UEM verifies the geofencing criteria mentioned in dynamic groups and moves the devices in and out of the groups.
If any of the associated policies gets violated, prompt notifications enable you to take appropriate actions. Admin can send notifications to the devices from the console even in kiosk mode. Additionally, Hexnode ensures that both single-device messaging and broadcasting are possible.
When employees bring their own devices, there are certain things that you need to take care of. Say, you want your employees to not use social networking sites when at work. You can do so with Hexnode UEM by blocking those applications when they enter the company premises. So, you see, geofencing for the win!
And so, here we go. Geofencing addresses the challenges that come up with managing a mobile workforce and a wide array of devices. By enabling location-based restrictions, automating actions, and facilitating granular control, geofencing empowers IT administrators to enforce device usage policies, enhance security, streamline workflows, and ensure regulatory compliance. And while we are at it, if you are looking for a UEM solution that harnesses the power of geofencing, look no further than Hexnode!